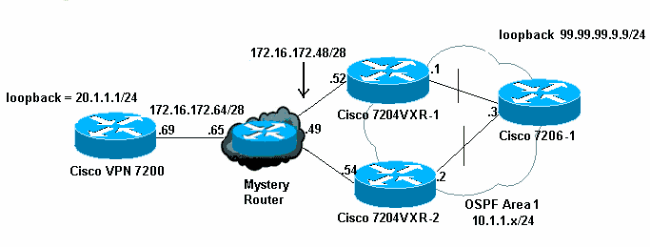
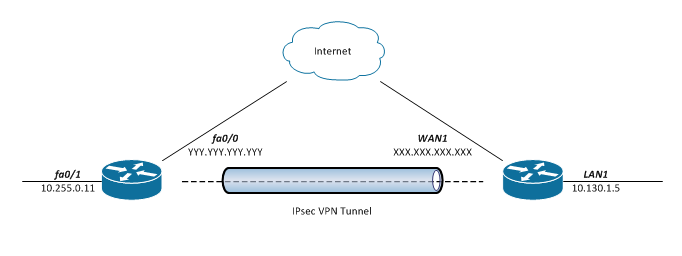
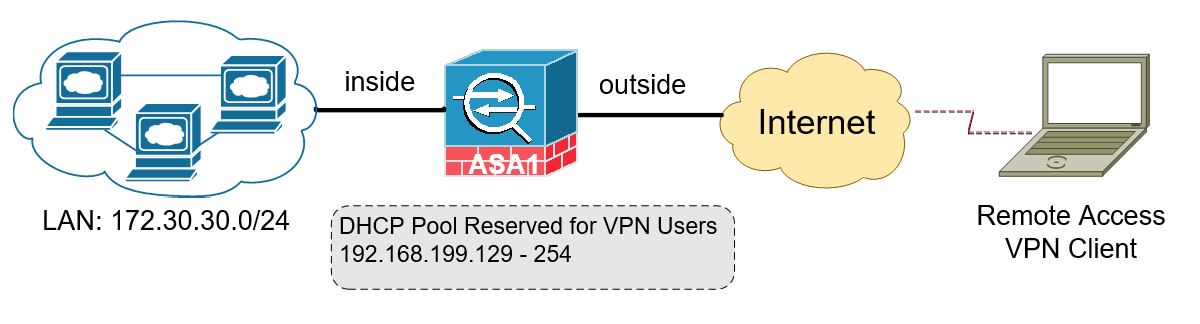
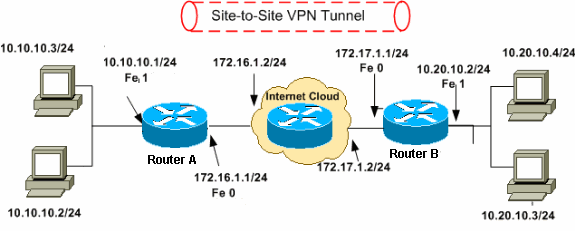
Cisco Ipsec Vpn
Anyconnect based on SSL protocol is called Anyconnect SSL VPN and if you deploy Anyconnect with IPSec protocol ,it is called IKev2 Anyconnect (using IKEv2 or SSLVPN) doesn't use a presharedkey to authenticate the user.

Cisco ipsec vpn. IPsec Diagnostic Tools within Cisco IOS In order to confirm that IKE proposal mismatches have occurred in an IPsec VPN tunnel negotiation, we will inspect the output of the ISAKMP SA. Provide Support for the Cisco VPN Client In most cases, IPSec VPN traffic does not pass through ISA Server 00 However, Cisco Concentrator 3300, with the latest firmware updates, uses "transparent tunneling" that uses User Datagram Protocol (UDP) ports 500, 4500, and to communicate securely between VPN clients and concentrators. Cisco Router command to disable IPSec VPN tunnel Hello Experts, Can anybody help me to know the command to disable IPSec VPN tunnel?.
IPSec IPSec acts at the network layer, protecting and authenticating IP packets between participating IPSec devices (peers), such as PIX Firewalls, Cisco routers, Cisco VPN 3000 Concentrators, Cisco VPN Clients, and other IPSeccompliant products. Like authentication, encryption and confidentialityVPN can be implemented using IPSEC, L2TP Layer Two Tunneling Protocol is a tunneling protocol (VPN) used to transport in L2 traffic over an IP Network ( Internet). Cisco Meraki’s unique auto provisioning sitetosite VPN connects branches securely with complete simplicity Using IPsec over any wide area network, the MX links your branches to headquarters as well as to one another as if connected with a virtual Ethernet cable.
Hi, I need to reach a secondary router internal subnet which is at the end of an ASA ipsec tunnel (see attached) For clients on Router A (/24) to reach clients on Router B (/24), would it just be a case of entering a static route eg Router A ip route 192. Set vpn ipsec espgroup FOO0 lifetime 3600 set vpn ipsec espgroup FOO0 pfs disable set vpn ipsec espgroup FOO0 proposal 1 encryption aes128 set vpn ipsec espgroup FOO0 proposal 1 hash sha1 5 Define the remote peering address (replace with your desired passphrase) set vpn ipsec sitetosite peer 1921 authentication mode pre. Threats can occur through a variety of attack vectors You need secure connectivity and alwayson protection for your endpoints Deploy Cisco endpoint security clients on Mac, PC, Linux, or mobile devices to give your employees protection on wired, wireless, or VPN.
IPSec IPSec acts at the network layer, protecting and authenticating IP packets between participating IPSec devices (peers), such as PIX Firewalls, Cisco routers, Cisco VPN 3000 Concentrators, Cisco VPN Clients, and other IPSeccompliant products. With the Cisco Secure VPN Client, you use menu windows to select connections to be secured by IPSec When interesting traffic is generated or transits the IPSec client, the client initiates the next step in the process, negotiating an IKE phase one exchange Step 1 is shown in Figure 116 Figure 116 Defining Interesting Traffic. The Cisco router is an old Cisco 2621 with IOS 123(26) and image “c2600ik9o3s3mzbin” Laboratory The following figure depicts my test laboratory Palo Alto The configuration steps for the Palo Alto Networks firewall are the following IKE and IPSec Crypto profiles, eg, aes256, sha1, pfs group 5, lifetime 8h/1h.
The Cisco router is an old Cisco 2621 with IOS 123(26) and image “c2600ik9o3s3mzbin” Laboratory The following figure depicts my test laboratory Palo Alto The configuration steps for the Palo Alto Networks firewall are the following IKE and IPSec Crypto profiles, eg, aes256, sha1, pfs group 5, lifetime 8h/1h. With the Cisco Secure VPN Client, you use menu windows to select connections to be secured by IPSec When interesting traffic is generated or transits the IPSec client, the client initiates the next step in the process, negotiating an IKE phase one exchange. I agree with ron;.
IPSec Phase 2 2 Create IPSec Transform Set – Need to define Encryption method and Hashing Algorithm Its Used to Secure Data in Transit SiteA(config)#crypto ipsec transformset MAAHI esp3des espmd5hmac Where “MAAHI” name of the transform set 3 Create Extended ACL – Need to Define Which traffic will be pass through IPSec VPN. Under Additional VPN Templates, located to the right of the screen, click VPN Interface IPsec From the VPN Interface IPsec dropdown, click Create Template The VPNInterfaceIPsec template form is displayed The top of the form contains fields for naming the template, and the bottom contains fields for defining VPN Interface IPsec parameters. Cisco Meraki uses IPSec for Sitetosite and Client VPN IPSec is a framework for securing the IP layer In this suite, modes and protocols are combined to tailor fit the security methods to the intended use Cisco Meraki VPNs use the following modeprotocol for SitetoSite VPN communication.
Crypto isakmp key ipsec address 0000 0000 !. Under Additional VPN Templates, located to the right of the screen, click VPN Interface IPsec From the VPN Interface IPsec dropdown, click Create Template The VPNInterfaceIPsec template form is displayed The top of the form contains fields for naming the template, and the bottom contains fields for defining VPN Interface IPsec parameters. Odd that IPSec with group authentication VPN works on Apple devices, not Microsoft If the Cisco IPSec client does not work in Windows 10 and the native Windows 10 IP sec connection also does not work for group authentication, what is Cisco's response to people who want to connect their users to the ASA using IPSec with group authentication?.
SitetoSite IPsec VPN Deployments and GRE (IPsecGRE) Path MTU discovery can be deployed in conjunction with the Cisco IOS IPsec prefragmentation, enabling the encrypting router to dynamically determine the smallest MTU of the path between VPN endpoints The encrypting VPN router is then capable of fragmenting to the appropriate MTU for. Crypto ipsec transformset vpn esp3des espmd5hmac mode transport !. Rightclick the IPSec policy that you just created, and then click Assign Setp 4 Connect VPN Now you should be able to connect to Cisco ASA VPN Other Resources L2TP Over IPsec Between Windows 00/XP PC and PIX/ASA 72 Using Preshared Key Configuration Example;.
4 DEPLOYING VPN IPSEC TUNNELS WITH CISCO ASA/ASAV VTI ON ORACLE CLOUD INFRASTRUCTURE Overview This guide provides stepbystep instructions for configuring VPN IPSec tunnels on Oracle Cloud Infrastructure It is helpful to know the basics of networking before following the steps outlined in this solution guide. Cisco ASA IPsec IKEV1 SitetoSite VPN In the first lesson you will learn how to build a CA with OpenSSL, the second lesson explains how to configure IPsec sitetosite VPNs with preshared keys Having said that, let’s get to work!. It gets increasing tricky to configure the correct IP addresses for authentication, and forward correct ports on protocols As I recently.
The final component of the IPseccompliant secure VPN is the Certification Authority (CA) Certification Authority interoperability is provided in support of the IPsec standard It permits Cisco IOS devices and CAs to communicate so that your Cisco IOS device can obtain and use digital certificates from the CA. Crypto ipsec transformset SHAAES256 espaes 256 espshahmac crypto map VPN 90 ipsecisakmp set peer set transformset SHAAES256 set pfs group5 match address I also test with Iperf as well In my situation, it is the 1841 that is the limitation factor On the 2811, I enabled the onboard AIM encryption card. Crypto isakmp policy 1 encr 3des hash md5 authentication preshare group 2 !.
Not long ago I wrote an article on how to configure an IPsec VPN using Mikrotik and Linux devices For today, I will replace the Linux device with a Cisco I did test the entire construct in GNS3 integrated with Mikrotik The topology looks like this The red line represent the IPsec VPN tunnel. The Cisco Secure VPN Client uses the concept of security policies to specify the same parameters Transforms, transform sets, and the corresponding security policies of the Cisco Secure VPN Client are explained in detail in Chapter 12, "Scaling Cisco IPSecBased VPNs". IPSec VPNs or really any sitetosite VPN works best when at least one of the sides or better yet both have Public IP addresses But what if one is behind NAT, or even both?.
This article shows how to configure, setup and verify sitetosite Crypto IPSec VPN tunnel between Cisco routers Understand IPSec VPNs, including ISAKMP Phase, parameters, Transform sets, data encryption, crypto IPSec map, check VPN Tunnel crypto status and much more Full set of commands and diagrams included. Not long ago I wrote an article on how to configure an IPsec VPN using Mikrotik and Linux devices For today, I will replace the Linux device with a Cisco I did test the entire construct in GNS3 integrated with Mikrotik The topology looks like this The red line represent the IPsec VPN tunnel. While VPN clients come from many vendors, Cisco's venerable Cisco VPN Client v5 was commonly used to communicate with Cisco routers and provide onestop connectivity to company resources However,.
IPsec Diagnostic Tools within Cisco IOS In order to confirm that IKE proposal mismatches have occurred in an IPsec VPN tunnel negotiation, we will inspect the output of the ISAKMP SA. Thanks, 6 years later still relevant Think this was a product of connecting my AnyConnect to many locations, one of which downloaded a profile, than affected my connection to another VPN Just deleted everything in that folder (C\ProgramData\Cisco\Cisco AnyConnect Secure Mobility Client\Profile), and was on Windows 10. If the following example does not help, there are several examples that turn up in a Google search for “cisco ios nonat ipsec” ip nat inside source route map NONAT interface FastEthernet0 / 0 overload access list 110 deny ip 50 00 0255 110 00 0255 access list 110 permit ip 50 00 0255 any.
For Cisco ASA, i wrote an article of IPSEC VPN with presharedkey authentication IPSECwithCiscoASApdf This does also explain the possibilities for IPSEC VPN with ASA and one end with dynamic ip address Juergen, Correct, ASA doesn't support DMVPN, hence why I mentioned using different hardware As for GRE over IPSEC, you do have the. I want to disable VPN tunnel without removing the configuration either Phase 1 or Phase 2 Thanks a lot in advance Regards, TK Expand Post. VPN tunnels are used to connect physically isolated networks that are more often than not separated by nonsecure internetworks To protect these connections, we employ the IP Security (IPSec) protocol to make secure the transmission of data, voice, and video between sites.
Cisco ASA IPsec VPN Troubleshooting Command In this post, we are providing insight on Cisco ASA Firewall command which would help to troubleshoot IPsec vpn issue and how to gather relevant details about IPsec tunnel This document describes common Cisco ASA commands used to troubleshoot IPsec issueThis document assumes you have configured IPsec tunnel on ASA. Configuring an IPSEC VPN using the MAC Built in Client to RV32x Series Router Step 1 Log in to the router using valid credentials Step 2 Step 3 Step 4 Step 5. This article serves as an extension to our popular Cisco VPN topics covered here on Firewallcx While we’ve covered Site to Site IPSec VPN Tunnel Between Cisco Routers (using static public IP addresses), we will now take a look on how to configure our headquarter Cisco router to support remote Cisco routers with dynamic IP addresses One important note to keep in mind when it comes to this.
Cisco Meraki uses IPSec for Sitetosite and Client VPN IPSec is a framework for securing the IP layer In this suite, modes and protocols are combined to tailor fit the security methods to the intended use Cisco Meraki VPNs use the following modeprotocol for SitetoSite VPN communication. The other way of doing IPSeC VPN is with VTI (tunnel interface) but the other end must support it as there is no more crypto ACL but all traffic routed through the tunnel is going through the VPN. LantoLan IPSEC VPN between two Cisco Routers January 26, 18 With IPSEC VPNs, businesses can connect together remote office LANs over the Internet with the strong encryption and security offered by the IPSEC protocol IPSEC is an IETF security standard It is basically a suit of several protocols that offer secure communication over.
Cisco Meraki’s unique auto provisioning sitetosite VPN connects branches securely with complete simplicity Using IPsec over any wide area network, the MX links your branches to headquarters as well as to one another as if connected with a virtual Ethernet cable. In this article, we configured IPSec VPN on Cisco Routers We discussed the requirements for the IPSec VPN After, we configure Phase1 and Phase2 on Cisco Router R1 The same configuration is done on the Cisco Router R2 You must need the static routable IP address to establish an IPSec Tunnel between both the routers. Cisco ipsec vpn client download Most people looking for Cisco ipsec vpn client downloaded Cisco VPN Client Download 35 on 190 votes The Cisco VPN Client is a software that enables customers to establish secure, endtoend encrypted tunnels to any Cisco Easy VPN server.
IPSec can be used to protect one or more data flows between a pair of hosts, between a pair of security Cisco 70 series routers, or between a security Cisco 70 series router and a host IKE is a hybrid security protocol that implements Oakley and SKEME key exchanges inside the Internet Security Association and Key Management Protocol (ISAKMP) framework. IPsec provides security for transmission of sensitive information over unprotected networks such as the Internet IPsec services are similar to those provided by Cisco Encryption Technology (CET), a proprietary security solution introduced in Cisco IOS Software Release 112. Cisco ASA IPsec IKEV1 SitetoSite VPN In the first lesson you will learn how to build a CA with OpenSSL, the second lesson explains how to configure IPsec sitetosite VPNs with preshared keys Having said that, let’s get to work!.
IPSEC is a standardized protocol (IETF standard) which means that it is supported by many different vendors Therefore if you want to create a VPN between different vendor devices, then IPSEC VPN is the way to go In this article we will see a sitetosite VPN using the IPSEC protocol between a Cisco ASA and a pfSense firewall. How to configure an L2TP/IPSec connection by using Preshared Key Authentication. How to configure an L2TP/IPSec connection by using Preshared Key Authentication.
IPSec Phase 2 2 Create IPSec Transform Set – Need to define Encryption method and Hashing Algorithm Its Used to Secure Data in Transit SiteA(config)#crypto ipsec transformset MAAHI esp3des espmd5hmac Where “MAAHI” name of the transform set 3 Create Extended ACL – Need to Define Which traffic will be pass through IPSec VPN. Crypto ipsec securityassociation idletime 600 !. How to get Cisco VPN IPsec Client to install on Windows 10 Pro 1) Download SonicWall 64 Bit VPN Client 2) Download Cisco IPSec VPN Client (Version ) 3) Install SonicWall VPN Client do not configure This is just so you can have the DNE Driver 4) Install Cisco IPSec VPN Client with Configuration file 5) Reboot computer 6) Go to.
This article seems to be the reference for IPsec SitetoSite (routebased) VPN between FortiGate and Cisco Router This helped me greatly to get a VPN tunnel up between my 2 devices (Fortigate 60C and Cisco 1W) I can ping from the Fortigate LAN to the Cisco LAN however I cannot ping from the Cisco to the Fortigate. IPSEC The Internet Protocol Security is a set of protocols that provides security features to IP;. Having been discontinued back in 11, it shouldn’t come as a shock that the Cisco VPN client isn’t supported by Windows 10In fact, you would be lucky to get it working with Windows 81 since.
Rightclick the IPSec policy that you just created, and then click Assign Setp 4 Connect VPN Now you should be able to connect to Cisco ASA VPN Other Resources L2TP Over IPsec Between Windows 00/XP PC and PIX/ASA 72 Using Preshared Key Configuration Example;. We would like to inform our readers that we have updated our download section to include Cisco's popular Windows VPN Client The Cisco VPN Client is available for both 32bit and 64bit Windows operating systems To download the latest Cisco VPN Client, simply visit our download section and look for our new Cisco Tools category!. IPSec Phase 2 2 Create IPSec Transform Set – Need to define Encryption method and Hashing Algorithm Its Used to Secure Data in Transit SiteA(config)#crypto ipsec transformset MAAHI esp3des espmd5hmac Where “MAAHI” name of the transform set 3 Create Extended ACL – Need to Define Which traffic will be pass through IPSec VPN.
IPsec Diagnostic Tools within Cisco IOS In order to confirm that IKE proposal mismatches have occurred in an IPsec VPN tunnel negotiation, we will inspect the output of the ISAKMP SA. IPSec and Crypto setup in Cisco, also here trasnport mode of IPSec should be setup !. This article shows how to configure, setup and verify sitetosite Crypto IPSec VPN tunnel between Cisco routers Understand IPSec VPNs, including ISAKMP Phase, parameters, Transform sets, data encryption, crypto IPSec map, check VPN Tunnel crypto status and much more Full set of commands and diagrams included.
Fullcrypto Cisco IPsec VPN gateway with software client Learn how to build an IPsec VPN gateway with a Cisco router and software client using a fullcrypto traffic model in which all traffic is either encrypted or processed by an internal firewall. Hi, If you login to the CLI of the ASA and run the command "show run crypto" this will list all the crypto configuration on the ASA You will be looking for an ikev1 policy eg "crypto ikev1 policy 10" and the ipsec transformset eg "crypto ipsec ikev1 transformset VPNTRANSFORM espaes256 espshahmac" and the "crypto map" configuration. For Cisco ASA, i wrote an article of IPSEC VPN with presharedkey authentication IPSECwithCiscoASApdf This does also explain the possibilities for IPSEC VPN with ASA and one end with dynamic ip address Juergen, Correct, ASA doesn't support DMVPN, hence why I mentioned using different hardware As for GRE over IPSEC, you do have the.

How To Configure Ipsec Vpn Between Cisco Asa And Palo Alto Firewall

Ipsec Vpn Between Srx And Cisco Rtodto Net

Cisco Ipsec Tunnel Mode Configuration
Cisco Ipsec Vpn のギャラリー
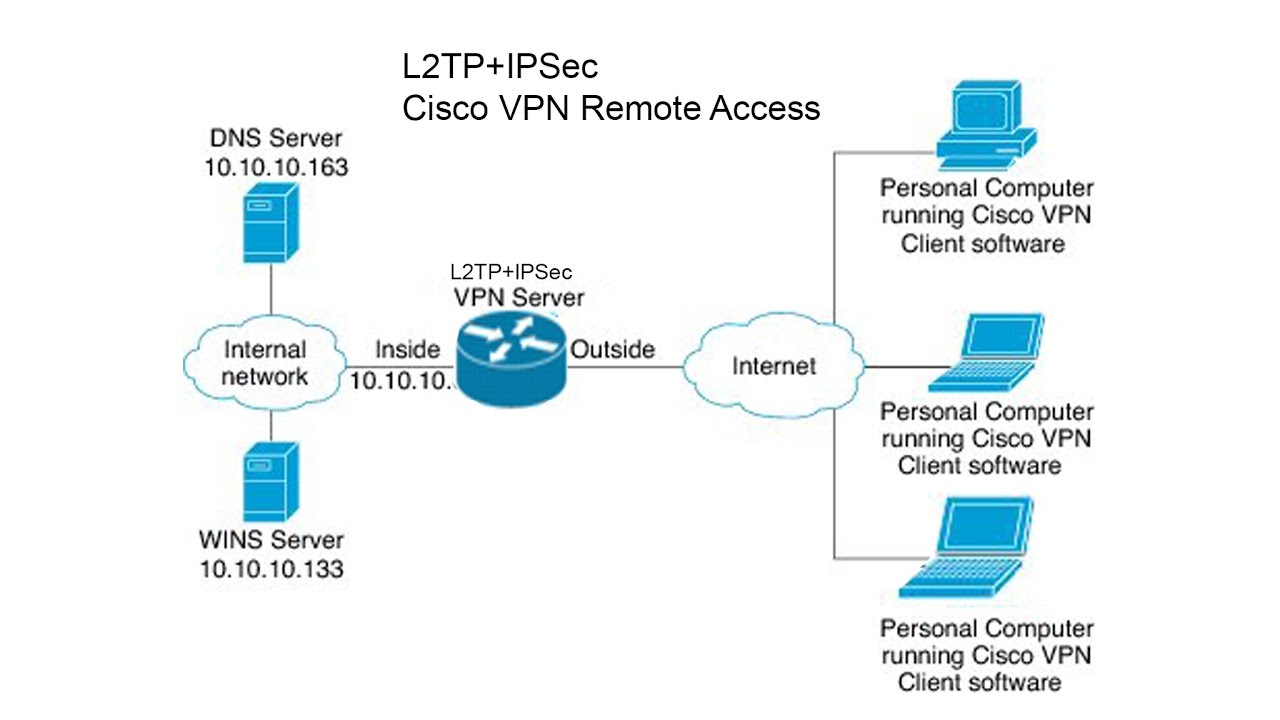
L2tp Ipsec Vpn Remote Access On Cisco Router P01 Youtube

Ipsec Direct Encapsulation Vpn Design Guide Cisco
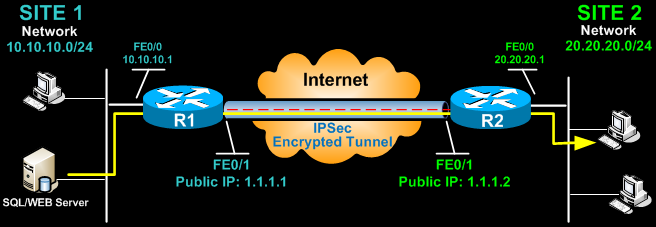
Configuring Site To Site Ipsec Vpn Tunnel Between Cisco Routers

Linux Ipsec Site To Site Vpn Aws Vpc Cisco Router Lazy Geek

Cisco Asa Ipsec Vpn With Ios Ca Cisco Pocket Guides Book 3 Asa 8 4 Ios 15 1 Wilson Grant Ebook Amazon Com

Ipsec Vpn Wan Design Overview Cisco
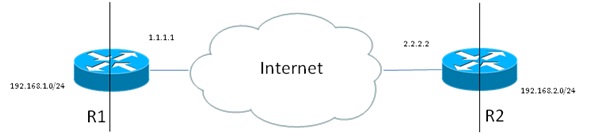
Create A Site To Site Ipsec Vpn Between Two Cisco Routers

Configure Site To Site Ipsec Vpn Tunnel In Cisco Ios Router
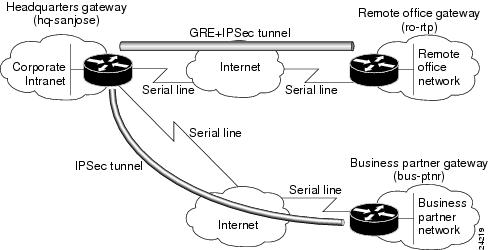
Cisco Ios Vpn Configuration Guide Site To Site And Extranet Vpn Business Scenarios Cisco 70 Series Routers Cisco
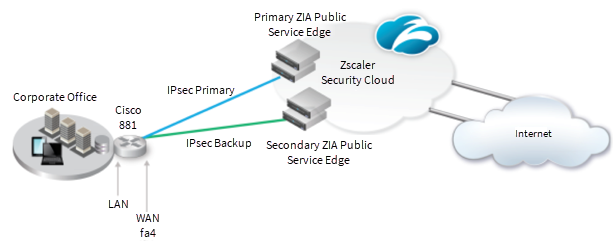
Ipsec Vpn Configuration Guide For Cisco 1 Isr Zscaler
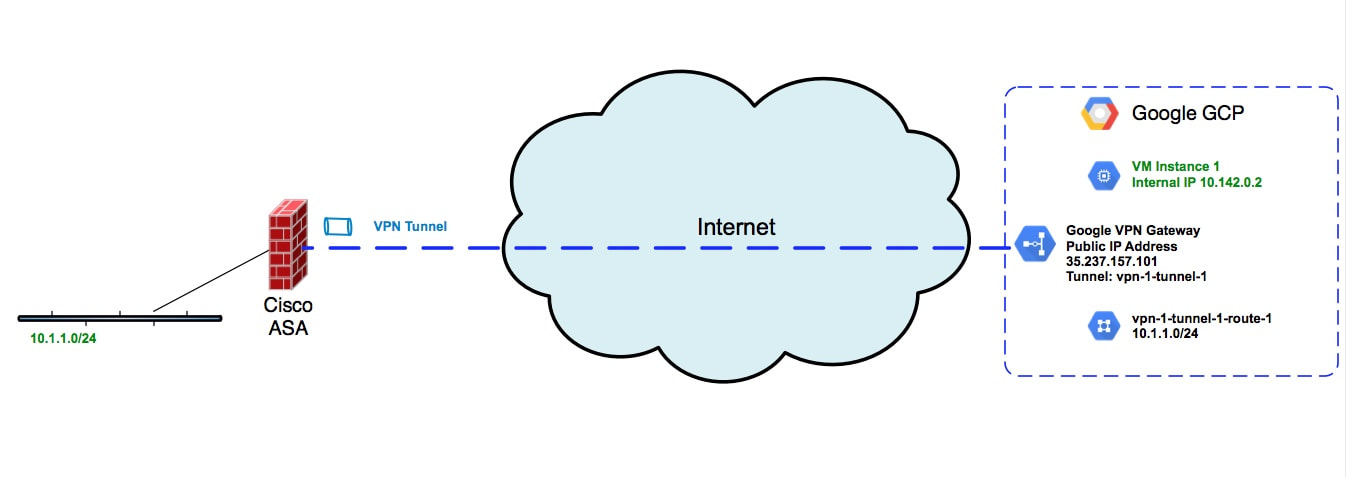
Configuring Route Based Vpns Between Google Gcp And Cisco Asa Firewalls Keith O Brien Blog Information And Cyber Security

Mo S Ccie Blog Cisco Asa Site To Site Ikev2 Ipsec Vpn
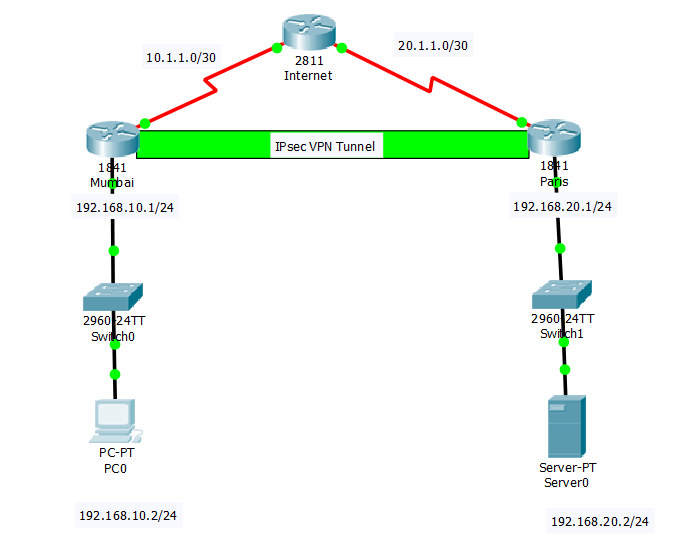
How To Configure Site To Site Ipsec Vpn Using Cisco Packet Tracer

Learn Easy Steps To Build And Configure Vpn Tunnel Between Openswan Linux To Cisco Asa Ver 9 1
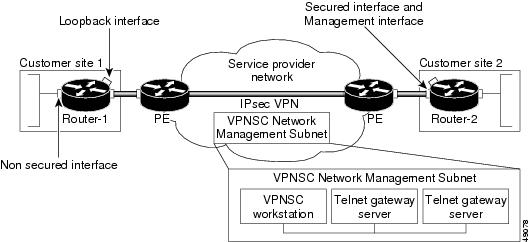
Introduction To Cisco Ipsec Technology Cisco

Troubleshooting Cisco Ipsec Site To Site Vpn Qm Rejected Cyber Security Memo

Ipsec Vpn Lab 13 1 Basic Site To Site Ipsec Vpn Cisco Press

Mikrotik Router To Cisco Pix Firewall Ipsec Mikrotik Wiki
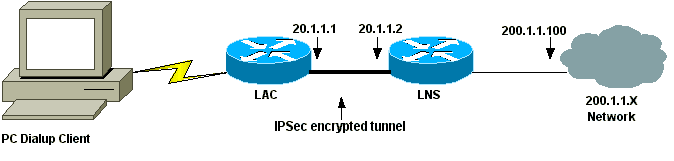
Configuring Layer 2 Tunneling Protocol L2tp Over Ipsec Cisco

Network Extension Mode
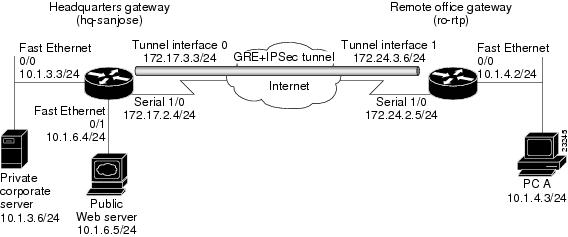
Cisco Ios Vpn Configuration Guide Site To Site And Extranet Vpn Business Scenarios Cisco 70 Series Routers Cisco
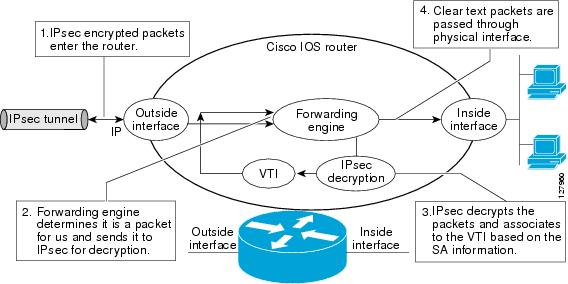
Security For Vpns With Ipsec Configuration Guide Cisco Ios Xe Release 3s Ipsec Virtual Tunnel Interfaces Support Cisco
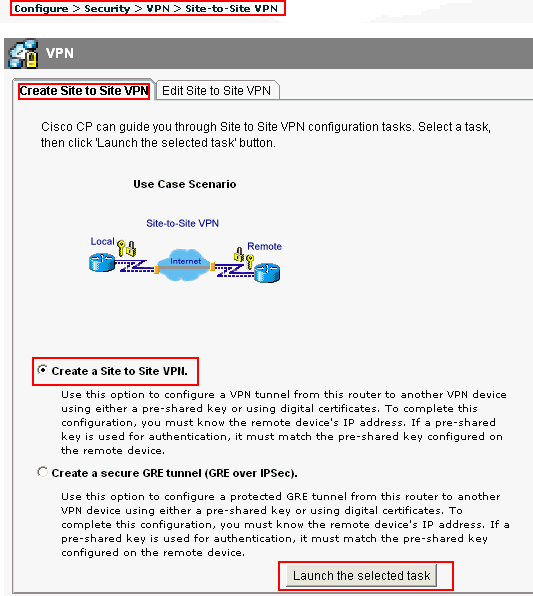
Configuration Professional Site To Site Ipsec Vpn Between Two Ios Routers Configuration Example Cisco

Basic Ipsec Vpn Site To Site On Cisco Router Step By Step 02 Youtube

Handbook Fortigate Fortios 6 0 0 Fortinet Documentation Library
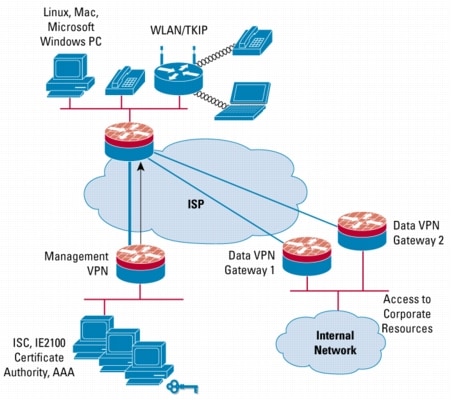
Cisco Ios Ipsec High Availability Ipsec Negotiation Ike Protocols Cisco Systems
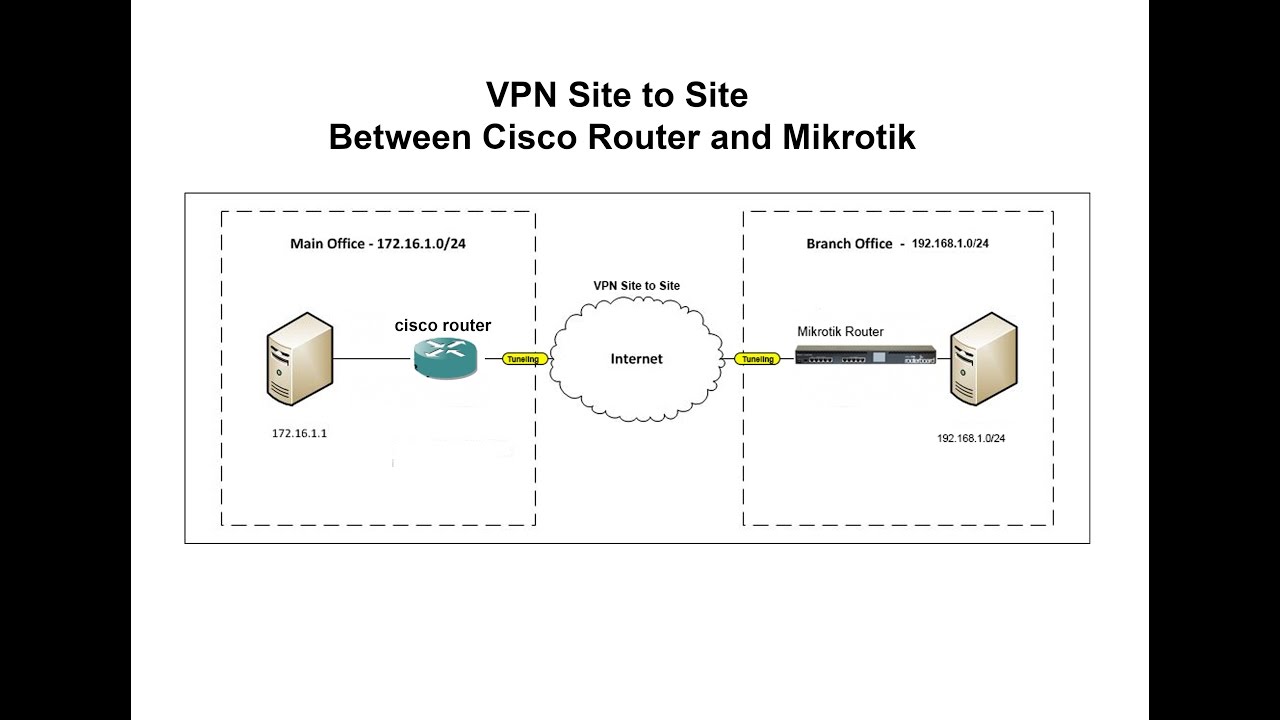
Mikrotik Vpn Site To Site Ipsec Between Cisco Router And Mikrotik Youtube
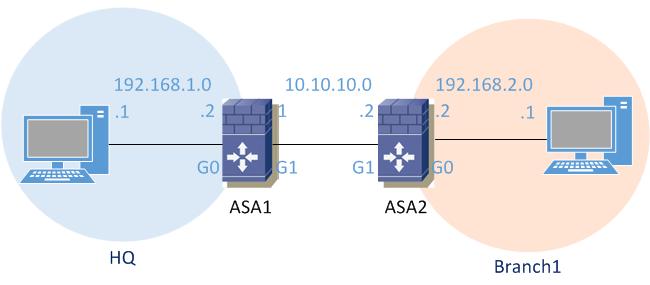
How To Configure Site To Site Ipsec Vpn On Cisco Asa Using Ikev2 Router Switch Blog
Configure Cisco Ipsec And Anyconnect Vpn By Shahzadmalik 01

Site To Site Ipsec Vpn Through Nat Packet Pushers

Using A Cisco Ipsec Vpn On Your Iphone Os X 10 6 Server Density Blog

Site To Site Ipsec Vpn Between Cisco Asa And Pfsense
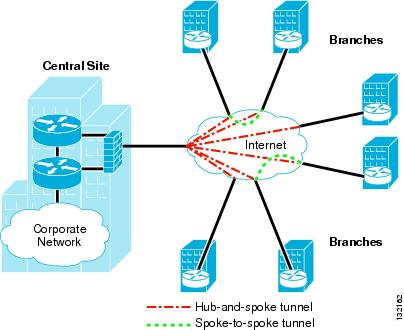
Ipsec Vpn Wan Design Overview Cisco

Cisco Asa Setting Up Anyconnect Vpn With Ssl And Ipsec Cyruslab
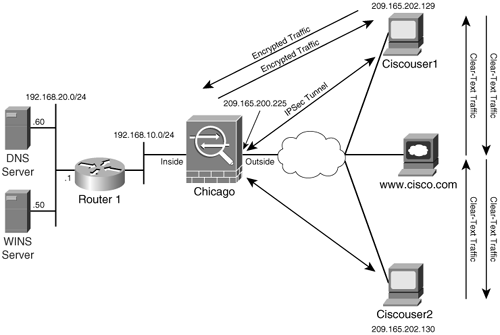
Cisco Remote Access Ipsec Vpn Setup Vpn Management Using Asdm

Ipsec Direct Encapsulation Vpn Design Guide Cisco
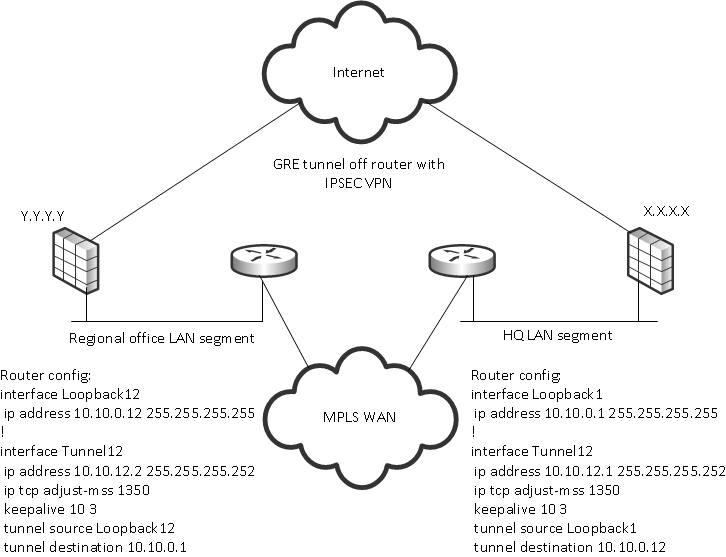
Ipsec Vpn Connection To Cisco Asa With Loopback Interfaces On Internal Gre Routers Discussions Xg Firewall Sophos Community
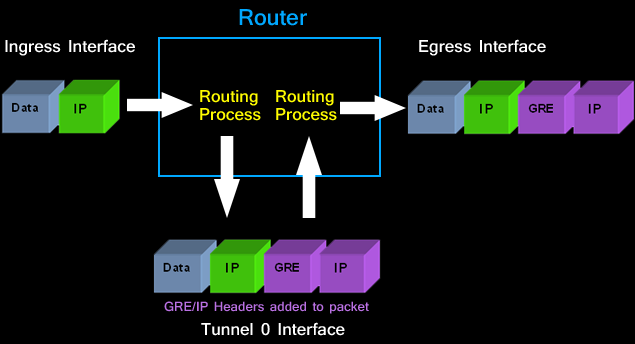
Configuring Point To Point Gre Vpn Tunnels Unprotected Gre Protected Gre Over Ipsec Tunnels
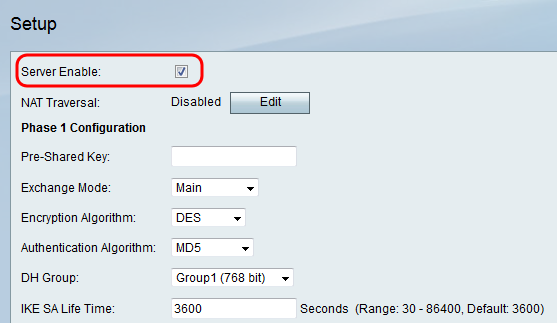
Configuration Of An Ipsec Vpn Server On Rv130 And Rv130w Cisco

Configure Site To Site Ipsec Vpn Huawei Routers Tech Space Kh

How To Set Up A Site To Site Ipsec Connection From A Ubiquiti Edgerouter Behind Nat To Cisco Asa Sebastiaan Dammann
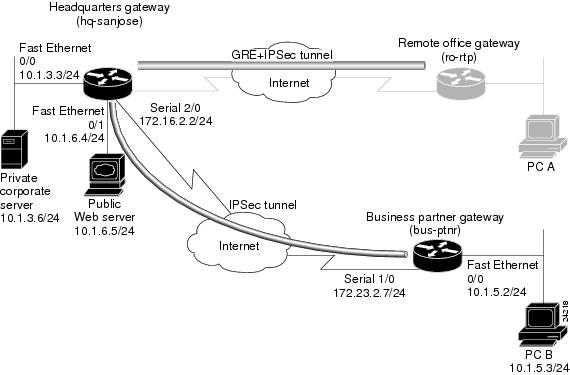
Cisco Ios Vpn Configuration Guide Site To Site And Extranet Vpn Business Scenarios Cisco 70 Series Routers Cisco
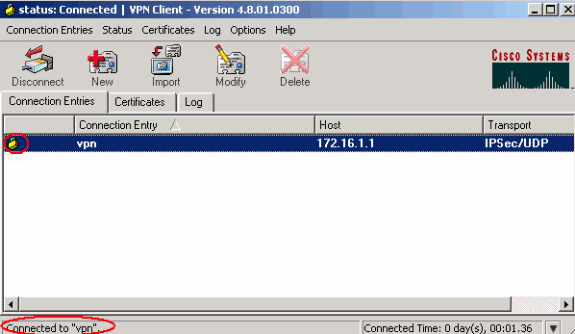
Router Allows Vpn Clients To Connect Ipsec And Internet Using Split Tunneling Configuration Example Cisco
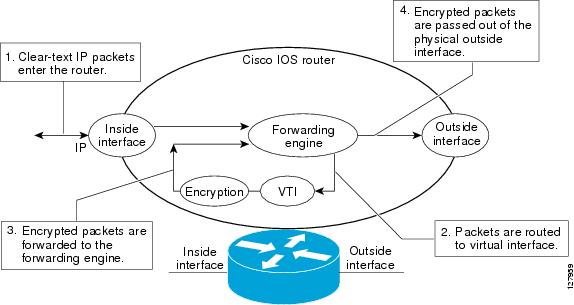
Security For Vpns With Ipsec Configuration Guide Cisco Ios Xe Release 3s Ipsec Virtual Tunnel Interfaces Support Cisco

How To Set Up Vpn Between Cisco Asr And Cloud Vpn

Cisco Asa Site To Site Ikev1 Ipsec Vpn

How To Configure Site To Site Ipsec Vpn Tunnel In Cisco Ios Router Tech Support Says
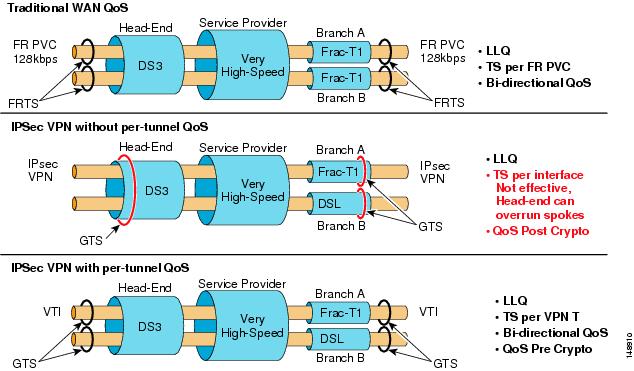
Ipsec Vpn Wan Design Overview Cisco

Configuring Ipsec Remote Access
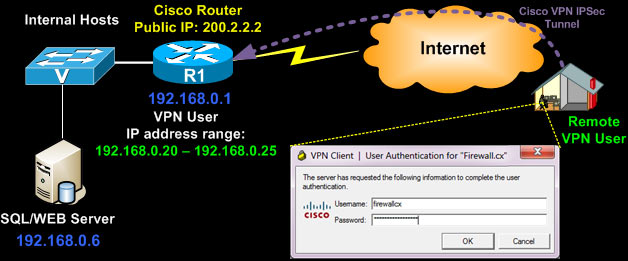
Cisco Vpn Client Configuration Setup For Ios Router
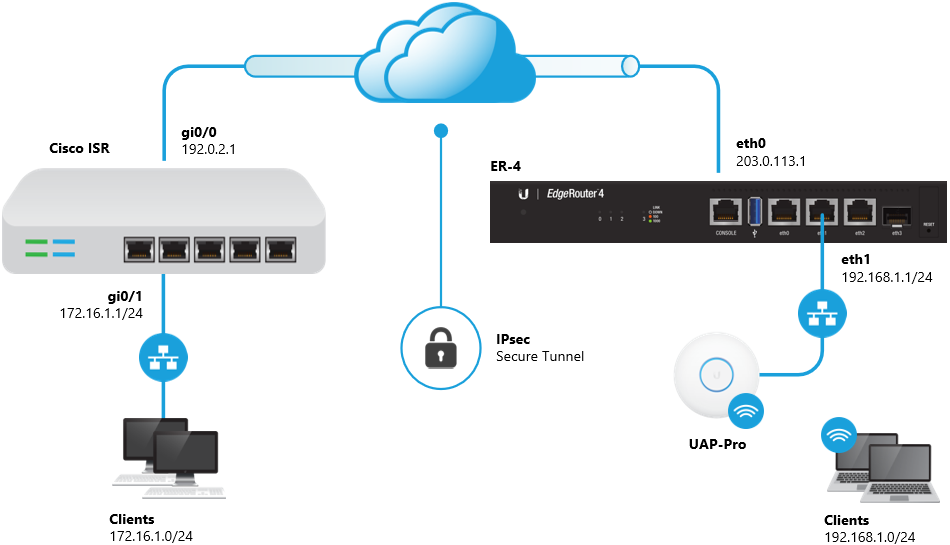
Edgerouter Site To Site Ipsec Vpn To Cisco Isr Ubiquiti Support And Help Center
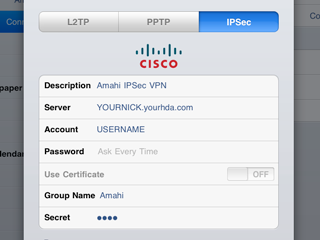
Ipsec Vpn For Amahi
Configuring High Availability Features For Site To Site Ipsec Vpns Cisco
How To L2l Ipsec Vpn Between Cisco Isr 2811 And Draytek Vigor 2850n Sk Scratchpad
Configuring L2tp Over Ipsec Vpn On Cisco Asa It Network Consulting Design Deploy And Support San Diego

Cisco Asa Spoke To Spoke Ipsec Vpn Strike One Popravak

Configure Site To Site Vpn With Ipsec In Cisco Networking And Wireless Training Courses

How To Failover Static Ipsec Vpn Tunnels Network Engineering Stack Exchange

Learn How To Configure Ipsec Site To Site Vpn On Cisco Router Using Cisco Packet Tracer Learn Linux Ccna Ceh Ccnp Ipv6 Cyber Security Python

Asa Anyconnect Ikev2 Ipsec Vpn Integrating It

Configure Site To Site Ipsec Vpn Cisco Asa 9 X Tech Space Kh
Configuration Professional Site To Site Ipsec Vpn Between Two Ios Routers Configuration Example Cisco
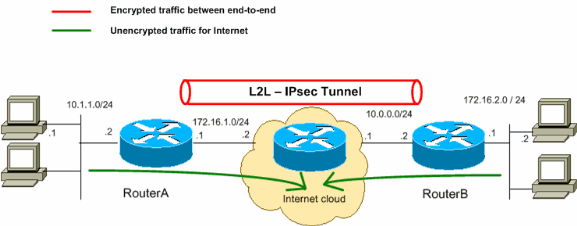
Lan To Lan Ipsec Tunnel Between Two Routers Configuration Example Cisco
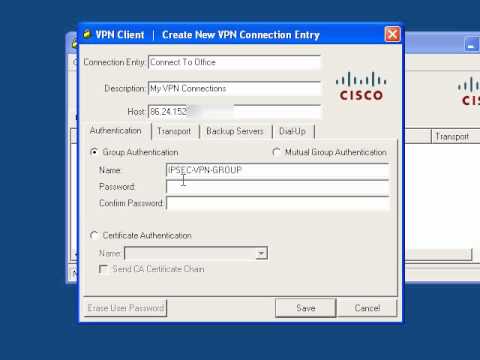
Working With The Cisco Vpn Client Ipsec Youtube

Implementing And Verifying An Ipsec Site To Site Vpn In Cisco Asa Santos Ccna Sec 210 260 Ocg Book
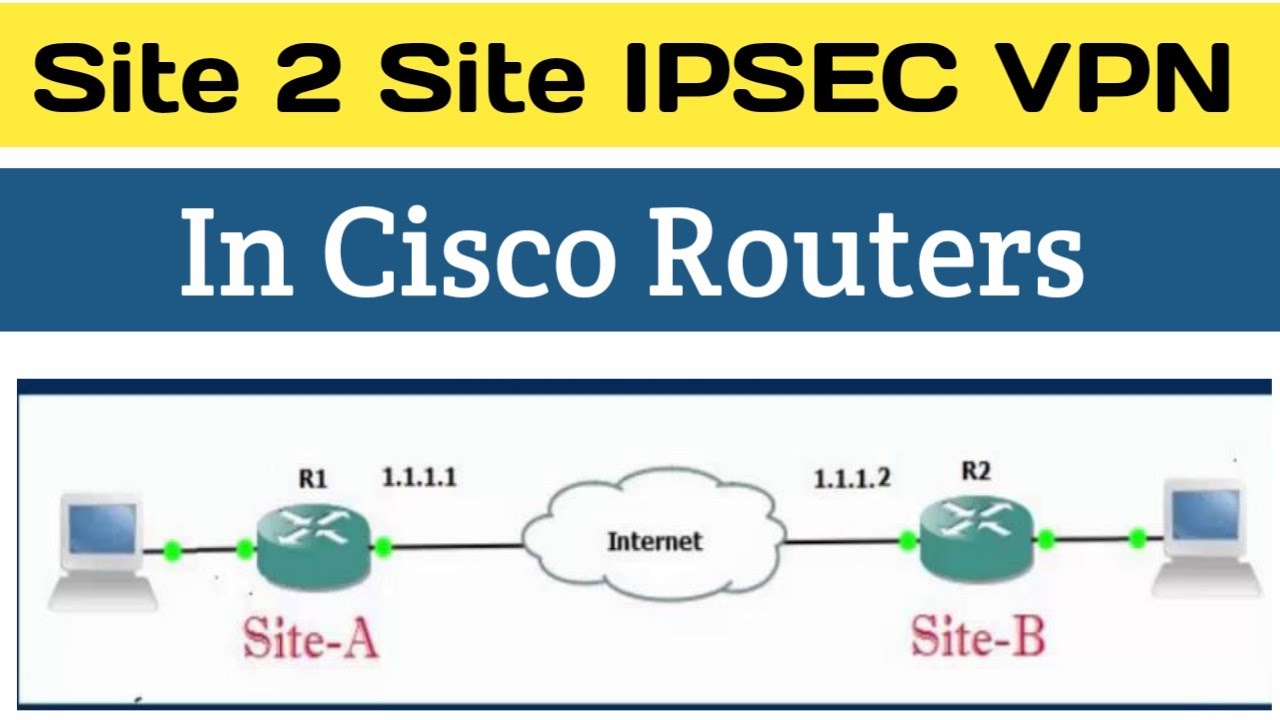
How To Configure Site To Site Ipsec Vpn Between Two Cisco Router Youtube

Site To Site Ipsec Vpn Between Two Cisco Asa One With Dynamic Ip

Implementation Of Ipsec Vpn On Cisco Routers And Configuring It On Is

Cisco Ipsec Vpn
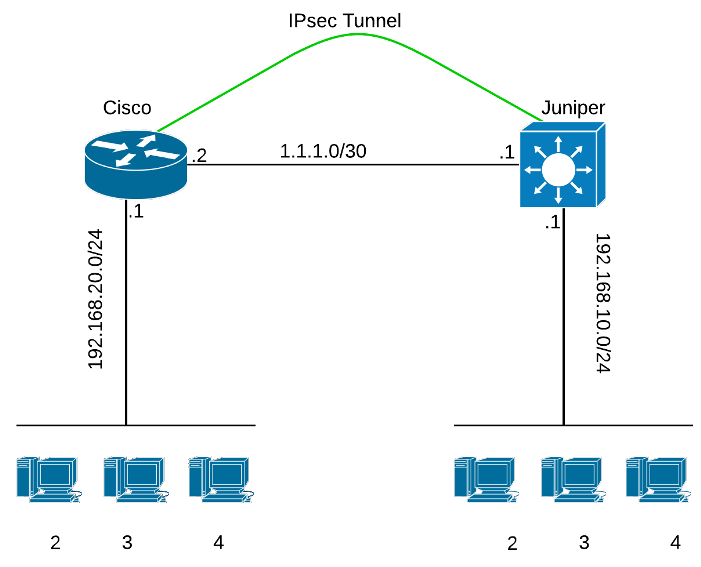
Site To Site Ipsec Vpn Between Cisco Router And Juniper Security Gateway
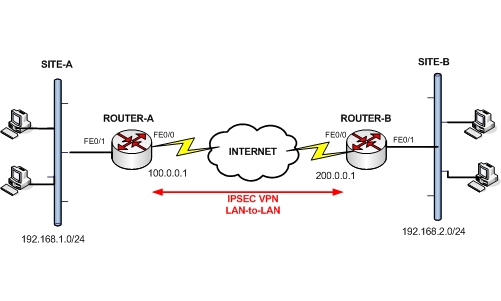
Lan To Lan Ipsec Vpn Between Cisco Routers Configuration Example
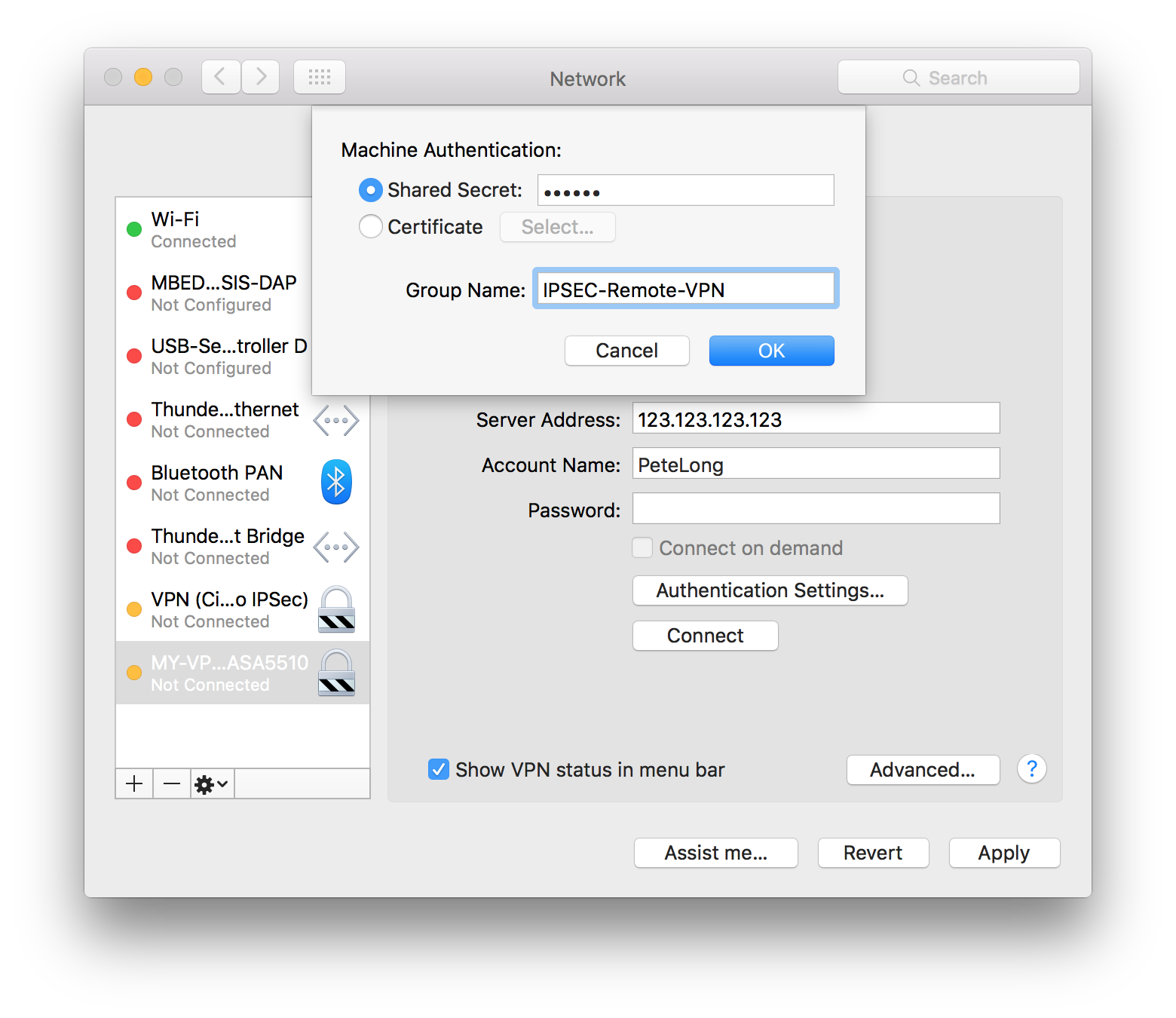
Mac Osx Connecting To Cisco Ipsec Vpn Petenetlive
It Blogtorials Configuring Ipsec Vpn Between Linux And Cisco

Configuring Ipsec Vpn On Cisco Ios Techrepublic

Add More Peer Ipsec Vpn Site To Site Cisco Routers Tech Space Kh

How To Set Up Vpn Between Cisco Asr And Cloud Vpn
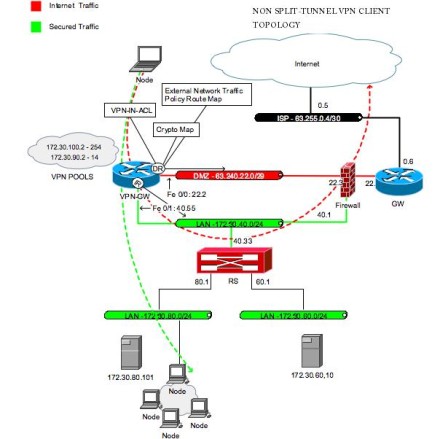
Full Crypto Cisco Ipsec Vpn Gateway With Software Client

Site To Site Ipsec Vpn Between Cisco Asa And Pfsense
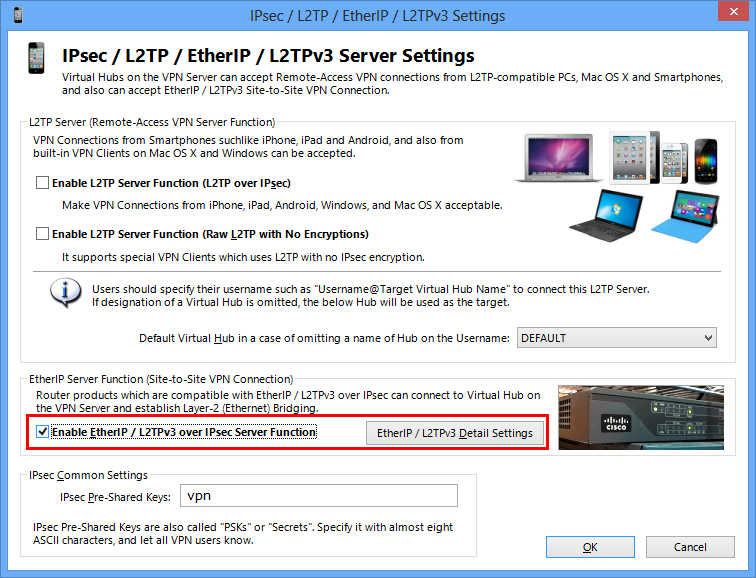
Cisco L2tpv3 Ipsec Edge Vpn Router Setup Softether Vpn Project

Ipsec Direct Encapsulation Vpn Design Guide Cisco
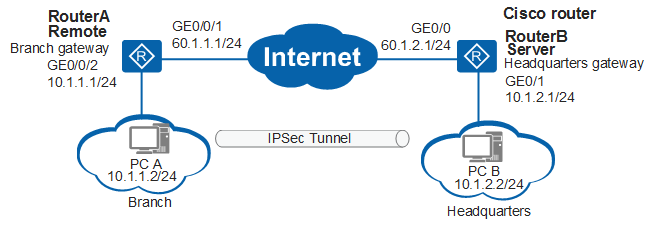
Example For Configuring The Headquarters Cisco Router To Manage Branches Using Efficient Vpn And Establishing Ipsec Tunnels Ar100 Ar1 Ar150 Ar160 Ar0 Ar10 Ar20 Ar30 And Ar3600 Cli Based Typical Configuration Examples
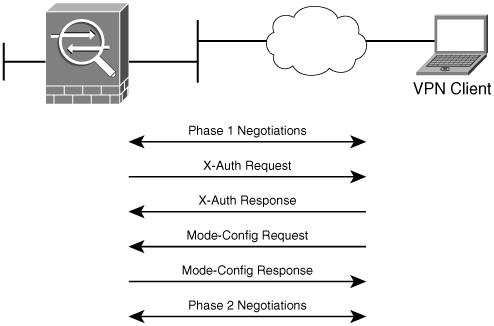
Cisco Ipsec Remote Access Vpn Solution Remote Access Vpn

Cisco Router Ipsec Vpn Tunnel Lab With Video The Routing Table
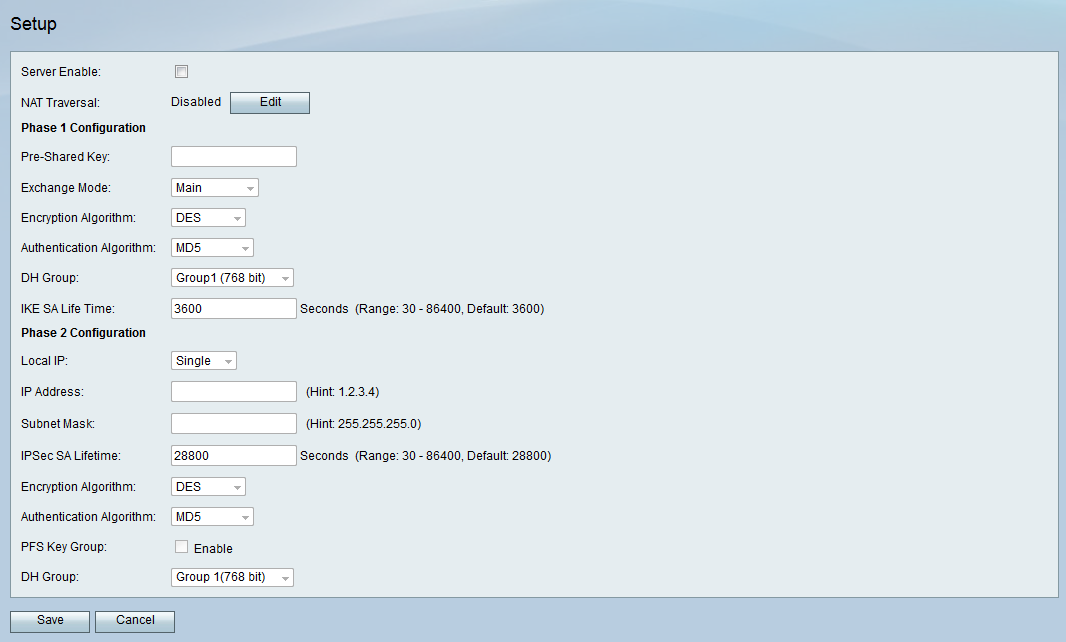
Configuration Of An Ipsec Vpn Server On Rv130 And Rv130w Cisco

Configure Site To Site Ipsec Vpn Cisco Routers Tech Space Kh

Administration Guide Fortigate Fortios 6 4 4 Fortinet Documentation Library

Cisco Ipsec Vpn Ccie Or Null
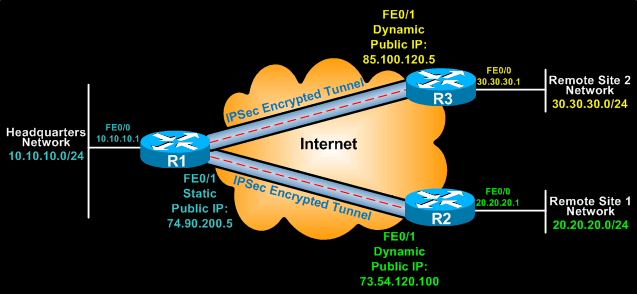
Configuring Cisco Site To Site Ipsec Vpn With Dynamic Ip Endpoint Cisco Routers

Ipsec Tunnel Between Cisco Routers Site To Site Vpn Between Cisco Routers

Ipsec Over Gre Tunnel On Ios How To Configure Two Cisco Routers To Create Site To Site Vpn Tunnel Uninets Blog
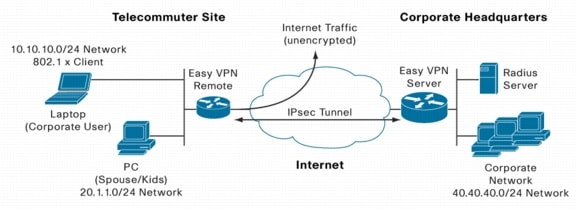
Configuring Cisco Ios Easy Vpn Remote With 802 1x Authentication Ipsec Negotiation Ike Protocols Cisco Systems
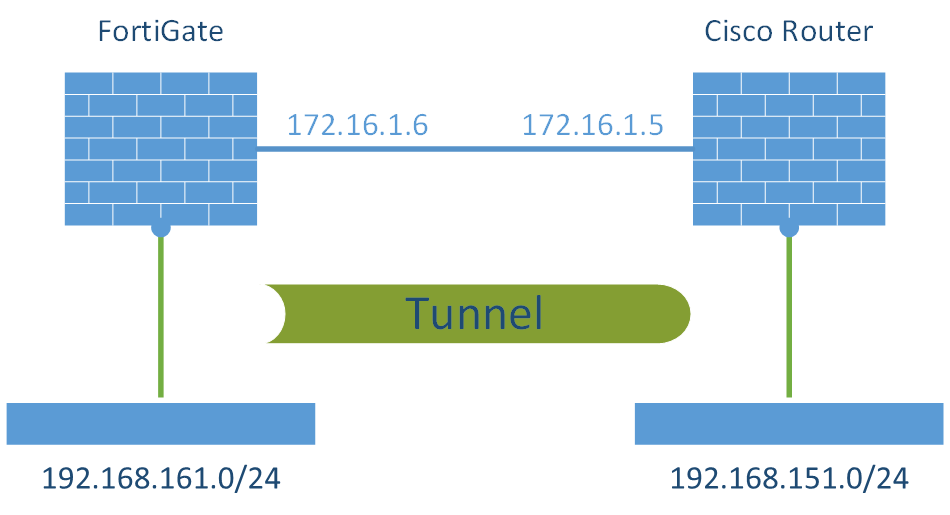
Ipsec Site To Site Vpn Fortigate Cisco Router Weberblog Net
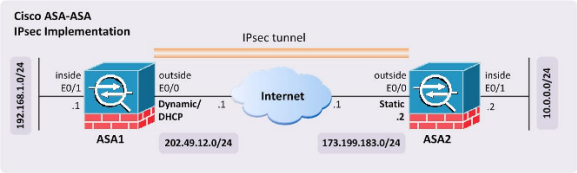
Site To Site Ipsec Vpn Between Two Cisco Asa 55 Router Switch Blog
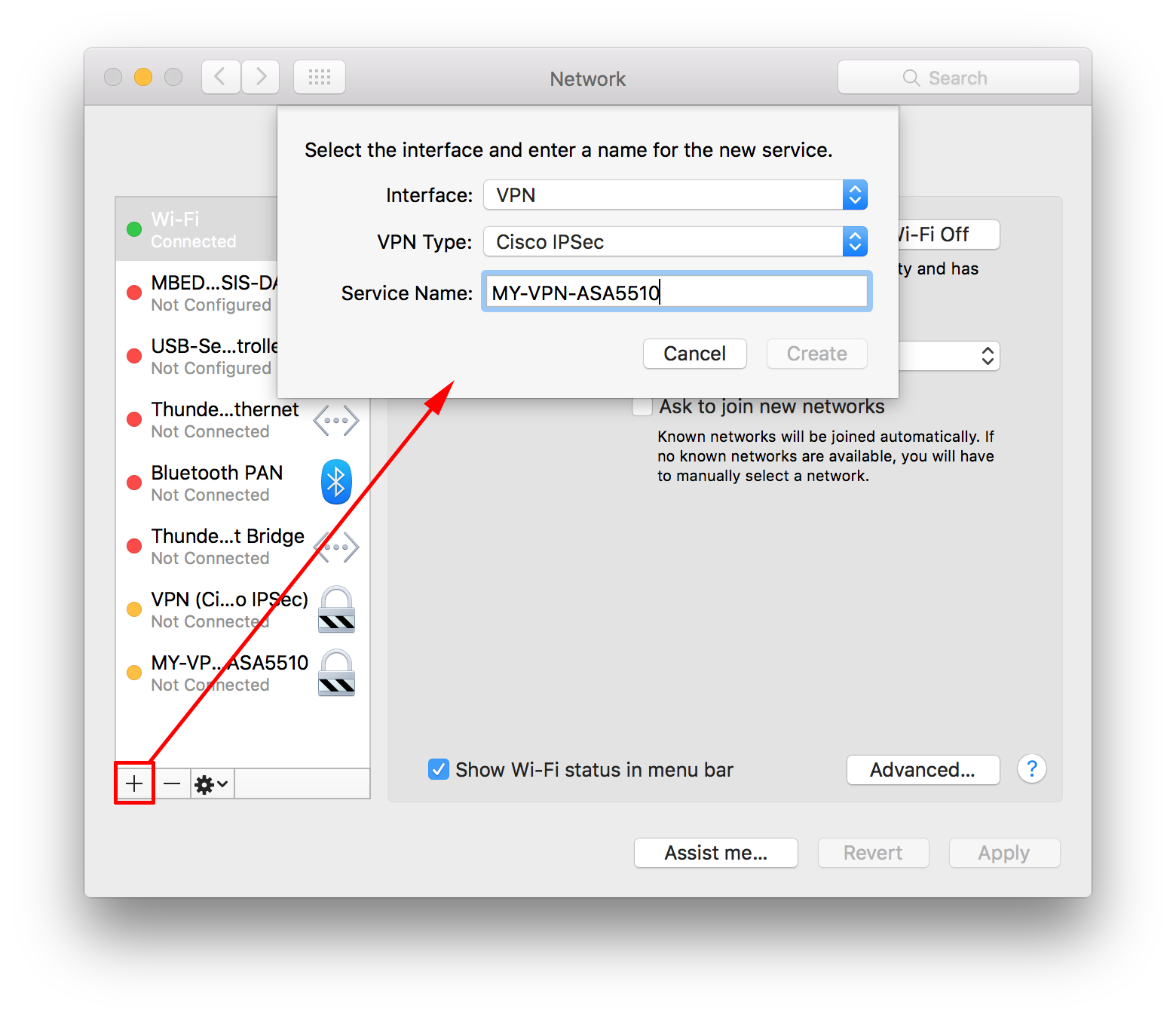
Mac Osx Connecting To Cisco Ipsec Vpn Petenetlive
Mikrotik Router Configuration Mikrotik To Cisco Asa Ipsec Site To Site Vpn Tunnel Configuration

Deploying The Cisco Asa Firepower Services In Vpn Scenarios Introduction To And Design Of Cisco Asa With Firepower Services Cisco Press

Site To Site Ikev2 Ipsec Vpn Between Sophos Xg And Cisco Router Route Xp Private Network Services



