Check Point Endpoint Security
Check Point is an AmericanIsraeli multinational provider of software and combined hardware and software products for IT security, including network security, endpoint security, cloud security, mobile security, data security and security management As of 19, the company has approximately 5,000 employees worldwide Headquartered in Tel Aviv, Israel and San Carlos, California, the company.
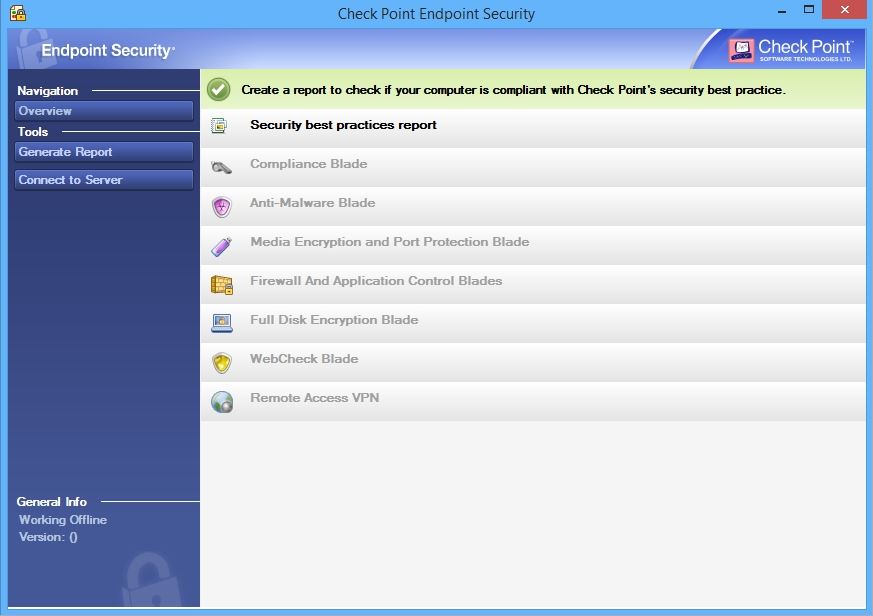
Check point endpoint security. Check Point Integrity is an endpoint security software product developed by Check Point Software TechnologiesIt is designed to protect personal computers and the networks they connect to from computer worms, Trojan horses, spyware, and intrusion attempts by hackersThe software aims to stop new PC threats and attacks before signature updates have been installed on the PC. Download checkpoint client for free Security tools downloads Check Point Endpoint Security by Checkpoint Software Inc and many more programs are available for instant and free download. Endpoint Security Homepage is now available Important Enterprise Endpoint Security E00 macOS Clients (Limited Availability) is now available This release provides initial support for the Endpoint Security Clients on macOS Catalina (1015) Notes The relevant links to downloads are located in the relevant section, ie Standalone Clients, Utilities/Services.
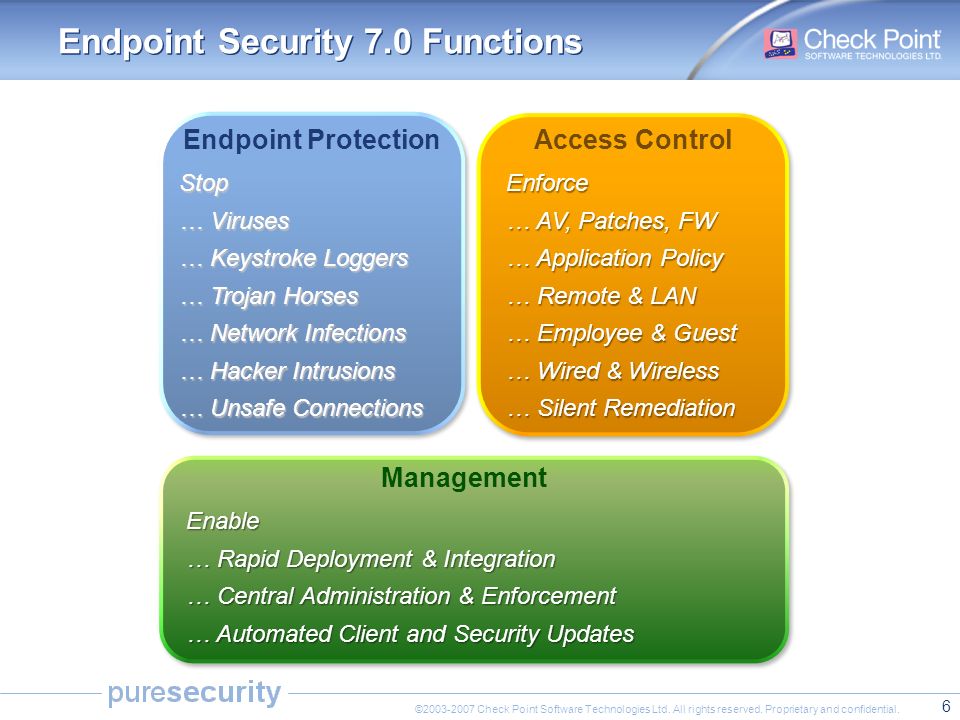
To take your endpoint security to the whole other level and the third capability is of course behavior analysis The ideal behavior analysis engine collects indicators from endpoint devices and correlate them with behavioral logistics and of course, machine learning models with such a multi layered approach to endpoint protection. A hardlink created from log file archive of Check Point ZoneAlarm up to or Check Point Endpoint Security client for Windows before E8096 to any file on the system will get its permission changed so that all users can access that linked file Doing this on files with limited access gains the local attacker higher privileges to the file. The cornerstones of the modern endpoint security To help you choose a solution that can secure your organization’s endpoint devices from all imminent threats without impacting business continuity, we have outlined the core principles that make endpoint security truly effective these days Principle #1 a preventionfirst approach.
Navigate the list of applications until you locate Check Point Endpoint Security or simply click the Search feature and type in "Check Point Endpoint Security" If it is installed on your PC the Check Point Endpoint Security program will be found automatically. Trusted Windows (PC) download Check Point Endpoint Security 862 Virusfree and 100% clean download Get Check Point Endpoint Security alternative downloads. Endpoint Protection Buyer’s Guide by Check Point Buyer's Guide to Endpoint Security.
Check Point Endpoint Security — System Specialist in the Transportation Industry We use Check Point Endpoint Security at the company for about 600 computers for endpoint security It has made us very comfortable on the part of the user, who keeps the security level up Read Full Review. File Name E40_CheckPointVPNmsi Product SecuRemote, Check Point Mobile, Endpoint Security VPN Version E Minor Version E40 OS Windows Build Number. Check Point Endpoint Security was added by westcoastoffense in Aug 12 and the latest update was made in Jun 19 The list of alternatives was updated Sep It's possible to update the information on Check Point Endpoint Security or report it as discontinued, duplicated or spam.
Management Console for Endpoint Security Server The SmartConsole for Endpoint Security Server allows the Administrator to connect to the Endpoint Security Server and to manage the new Endpoint Security Software Blades Note If you have an old SmartConsole of version R7730 already installed, you need to uninstall and install the new one. About Check Point Advanced Endpoint Security Check Point Advanced Endpoint Security is an endtoend security solution for network, data, forensics, advanced threat and EDR It enables its users to manage the entire security suite from a single platform. Check Point Endpoint Security は、PCのハードディスク・外部記憶メディアの暗号化、ウイルス・マルウェア対策、ゼロデイ攻撃をブロックする仮想Webブラウザで、エンドポイントを守るセキュリティ対策ソフトウェアです。.
Check Point Endpoint Security versions / release schedules Sergey_Popov inside Endpoint Security Products 1349 1 Secure Workspace problem on Windows 10 Tom_Heesmans inside Endpoint Security Products 1111 1348 6 2 Smartcard FDE preboot authentication. A hardlink created from log file archive of Check Point ZoneAlarm up to or Check Point Endpoint Security client for Windows before E8096 to any file on the system will get its permission changed so that all users can access that linked file Doing this on files with limited access gains the local attacker higher privileges to the file. Check Point is an AmericanIsraeli multinational provider of software and combined hardware and software products for IT security, including network security, endpoint security, cloud security, mobile security, data security and security management As of 19, the company has approximately 5,000 employees worldwide Headquartered in Tel Aviv, Israel and San Carlos, California, the company.
Check Point Endpoint Security は、PCのハードディスク・外部記憶メディアの暗号化、ウイルス・マルウェア対策、ゼロデイ攻撃をブロックする仮想Webブラウザで、エンドポイントを守るセキュリティ対策ソフトウェアです。. Check Point Endpoint Security E00 Client introduces BitLocker Management as an option in the Full Disk Encryption Blade BitLocker is an integrated part of Windows The Check Point BitLocker Management feature uses the Endpoint Security Server, Client Agent and Management UI to manage BitLocker BitLocker Management is Windows 10 only. The place to discuss all of Check Point's Remote Access VPN solutions, including Mobile Access Software Blade, Endpoint Remote Access VPN, SNX, Capsule Connect, and more!.
Check Point Endpoint Security's main file takes about KB (4084 bytes) and is called epab_svcexe Check Point Endpoint Security contains of the executables below They take 6121 MB ( bytes) on disk. Deploying Endpoint Security Clients This chapter contains information and procedures for deploying Endpoint Security clients to endpoint computers Before deploying the clients, you must add packages to the Repository on the Endpoint Security Management ServerSee Uploading Client Packages to the Repository For clients on Windows, you can use one of these deployment strategies. Hear firsthand insights on choosing the right endpoint security and the key considerations customers have when choosing the endpoint solution Watch our ondemand webinar Choosing Optimal Endpoint Security in the New Normal Check Point Software.
Check Point SandBlast Agent is a complete endpoint security solution offering a fleet of advanced endpoint threat prevention capabilities so you can safely navigate today’s menacing threat landscapeIt provides a comprehensive system to proactively prevent, detect, and remediate evasive malware attacks. Check Point endpoint security solutions include data security, network security, advanced threat prevention, forensics and remote access VPN for complete endpoint protection To simplify security administration, our endpoint suite products can be managed using a single console. Endpoint Security is a Management Software Blade in a Check Point Security Management Server SmartEndpoint is the management console for Endpoint Security clients and their features Endpoint Security Features One management console for endpoint security management;.
Monitor your security status with a customizable, ataglance dashboard. Monitor your security status with a customizable, ataglance dashboard. Endpoint Security is a Management Software Blade in a Check Point Security Management Server SmartEndpoint is the management console for Endpoint Security clients and their features Endpoint Security Features One management console for endpoint security management;.
Management Console for Endpoint Security Server The SmartConsole for Endpoint Security Server allows the Administrator to connect to the Endpoint Security Server and to manage the new Endpoint Security Software Blades Note If you have an old SmartConsole of version R7730 already installed, you need to uninstall and install the new one. Check Point Endpoint Security™ is the first and only single agent that combines all essential components for total security on the endpoint highestrated firewall, Antivirus, Antispyware, Full Disk Encryption, Endpoint Security Media Encryption with port protection, network access control (NAC), program control and VPN. Check Point Endpoint Security is the first single agent for total endpoint security that combines the highestrated firewall, network access control (NAC), program control, antivirus, antispyware, data security, and remote access It protects PCs and eliminates the need to deploy and manage multiple agents, reducing total cost of ownership.
Check Point Endpoint Security™ is the first and only single agent that combines all essential components for total security on the endpoint highestrated firewall, Antivirus, Antispyware, Full Disk Encryption, Endpoint Security Media Encryption with port protection, network access control (NAC), program control and VPN. Check Point Capsule Docs, Endpoint Security and Remote Access VPN E8062 / R 2 E8062 / R SmartConsole for Endpoint Security Server 3 E8062 / R77 SmartConsole for Endpoint Security Server 4 E8062 Check Point Endpoint Security Clients for Windows OS (ZIP) 5. Check Point endpoint security solutions provide data security, network security, advanced threat prevention, forensics and remote access VPN for complete endpoint protection Check Point AntiMalware and Application Control further help to efficiently detect malware with a single scan and make sure only approved software programs are running on.
Check Point endpoint security includes data security, network security, advanced threat prevention, forensics, endpoint detection and response (EDR), and remote access VPN solutions To offer simple and flexible security administration, Check Point’s entire endpoint security suite can be managed centrally using a single management console. Endpoint antivirus software only safeguards your data against viruses—it does not safeguard the data itself Unless your business still relies on couriers and filing cabinets, an endpoint antivirusbased security approach will leave your enterprise open to data loss. Check Point Endpoint Security is the first and only single agent that combines all critical components for total security on the endpoint while maintaining a transparent user experience Marketleading data security prevents corporate data loss, while collaborative endpoint and network protections reduce complexity and cost.
Hear firsthand insights on choosing the right endpoint security and the key considerations customers have when choosing the endpoint solution Watch our ondemand webinar Choosing Optimal Endpoint Security in the New Normal Check Point Software. Check Point Endpoint Security Check Point Endpoint Security includes data security, network security, advanced threat prevention, forensics, and remote access VPN solutions Some parts of the software run as a Windows service executed as “NT AUTHORITY\SYSTEM,” which provides it with very powerful permissions. Check Point Capsule Docs, Endpoint Security and Remote Access VPN E8062 / R 2 E8060 / E8061 / E8062 Endpoint Security VPN for Mac OS X Administration Guide I have a couple issues with the Checkpoint Endpoint Security VPN software on my Mac I need to use Netscaler Gateway software.
Join the Discussion Handson Labs Remote Access VPN Tools. Check Point Endpoint Security 862 is free to download from our software library This PC software is suitable for 32bit and 64bit versions of Windows XP/Vista/7/8/10 The software lies within Security Tools, more precisely Antivirus The actual developer of the program is Checkpoint Software Inc. About Check Point Advanced Endpoint Security Check Point Advanced Endpoint Security is an endtoend security solution for network, data, forensics, advanced threat and EDR It enables its users to manage the entire security suite from a single platform.
Installed with Check Point's Endpoint Security, this file displays the General User Interface for this VPN program Unnecessary to run at startup as it will start when you launch the software. Check Point Endpoint Security A way to uninstall Check Point Endpoint Security from your system Check Point Endpoint Security is a software application This page holds details on how to remove it from your PC The Windows release was created by Check Point Software Technologies Ltd. Check Point Endpoint Security is a software program developed by Check Point, Inc During setup, the program creates a startup registration point in Windows in order to automatically start when any user boots the PC Upon being installed, the software adds a Windows Service which is designed to run continuously in the background.
Endpoint Security Homepage is now available Notes To support SmartLog or SmartView Tracker reporting with Endpoint Security Clients for all supported servers (except R80 and higher), you must update the log schema. Introduction to Endpoint Security Client Check Point Endpoint Security™ is the first and only single agent that combines all essential components for total security on the endpoint highestrated firewall, Antivirus, Antispyware, full disk encryption, media encryption with port protection, network access control (NAC), program control and VPN. Check Point Endpoint Security Check Point Endpoint Security includes data security, network security, advanced threat prevention, forensics, and remote access VPN solutions Some parts of the software run as a Windows service executed as “NT AUTHORITY\SYSTEM,” which provides it with very powerful permissions.
Check Point is a wellknown name in the cybersecurity space They have a wide range of solutions for cloud security, network security, mobile security, threat prevention, and more SandBlast Agent from Check Point is a complete endpoint security system. The Check Point advantages include preventing known and unknown zero day network attacks, easily expanding threat prevention capacity in minutes to provide cloud level expansion and resiliency, and providing a quantum leap in security performance from the branch office to the data center. Check Point’s mission is to provide industryleading security solutions that redefine the security landscape We achieve our mission by constantly developing innovative and cutting edge technology solutions focused on real customer needs while challenging ourselves to grow and excel.
Under Security at the bottom of the General tab check the Unblock option and then okay Now run the installer and it should bypass that screen When the Check Point Endpoint Security VPN Installer Wizard start press Next. Introduction to Endpoint Security Client Check Point Endpoint Security™ is the first and only single agent that combines all essential components for total security on the endpoint highestrated firewall, Antivirus, Antispyware, full disk encryption, media encryption with port protection, network access control (NAC), program control and VPN. Come join a dynamic cyber security “internal startup” group in Check Point researching, inventing and developing new ways to discover and analyze cyberattacks We are looking for a star security oriented software level architect, to join our endpoint Advanced Threat Prevention Innovation and development area.
Check Point Endpoint Security is the first and only single agent that combines all critical components for total security on the endpoint while maintaining a transparent user experience Marketleading data security prevents corporate data loss, while collaborative endpoint and network protections reduce complexity and cost.

Install Endpoint Security Management Server E80 70 On Gaia R77 30 03 Qos Technology

Endpoint Security Vpn Check Point Software Manualzz

Check Point Endpoint Integrity Solutions
Check Point Endpoint Security のギャラリー

Check Point Endpoint Remote Access Vpn Reviews 21 Details Pricing Features G2

Check Point Endpoint Security How To Prevent Data Loss Youtube

4 Check Point Sandblast Agent Management Platform Data Protection Policy Deployment And Global Policy Settings Prog World
Check Point Software Technologies Ltd All Rights Reserved Proprietary And Confidential Introducing Check Point Endpoint Security J E John Ppt Download

Check Point Patches Privilege Escalation Flaw In Endpoint Client
Http Downloads Checkpoint Com Dc Download Htm Id
Endpoint Vpn Software Installation For Windows Oist Groups

Check Point Sandblast Agent Reviews Ratings Alternatives Gartner 21
Check Point Endpoint Security Client E80 For Ma Check Point Checkmates

Check Point Endpoint Security Complete Windows And Mac Os X Security Tarsus Today
Cpl Thalesgroup Com Sites Default Files Integration Guide 007 0121 001 Sac Integrationguide Check Point Endpoint Security Fde Cba Reva Pdf

Check Point Endpoint Policy Management Checkfirewalls Com

Checkpoint End Security Virtual Private Network Authentication
Connection Failed Enforce Firewall Policy Failed On Win 7 64bit Crazy It Professionals

Solved How To Test The Checkpoint Endpoint Security Agent Smartbear Community

2 2 Checkpoint Vpn Install Documentation Raileurope Downloads Download Euronet
Http Www Checkfirewalls Com Datasheets Disk Encryption Datasheet Pdf

Fujitsu Tds Gmbh

Endpoint Security E80 90 Reconnected Immediately Check Point Checkmates
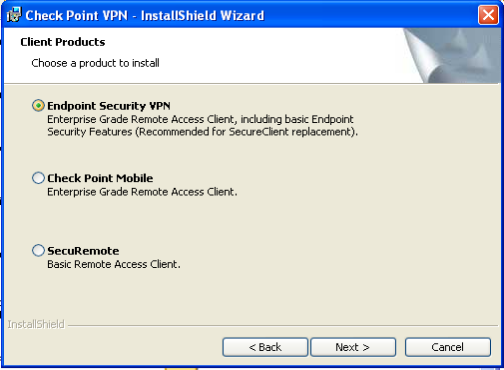
Checkpoint Endpoint Security Vpn Client Download Mac Peatix
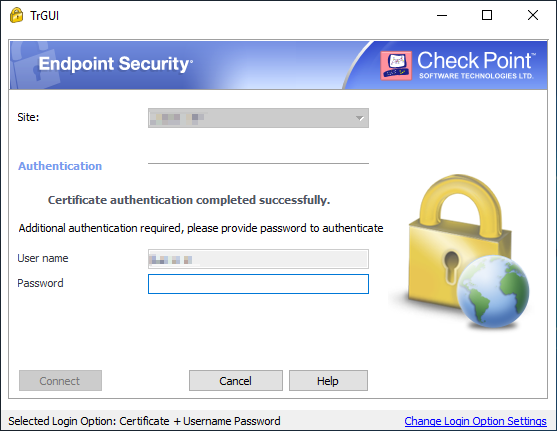
Check Point Endpoint Security Client E80 For Ma Check Point Checkmates

Check Point Endpoint Security Reviews And Pricing It Central Station

Test Check Point Endpoint Security 81 10 For Windows 10 1935 Av Test
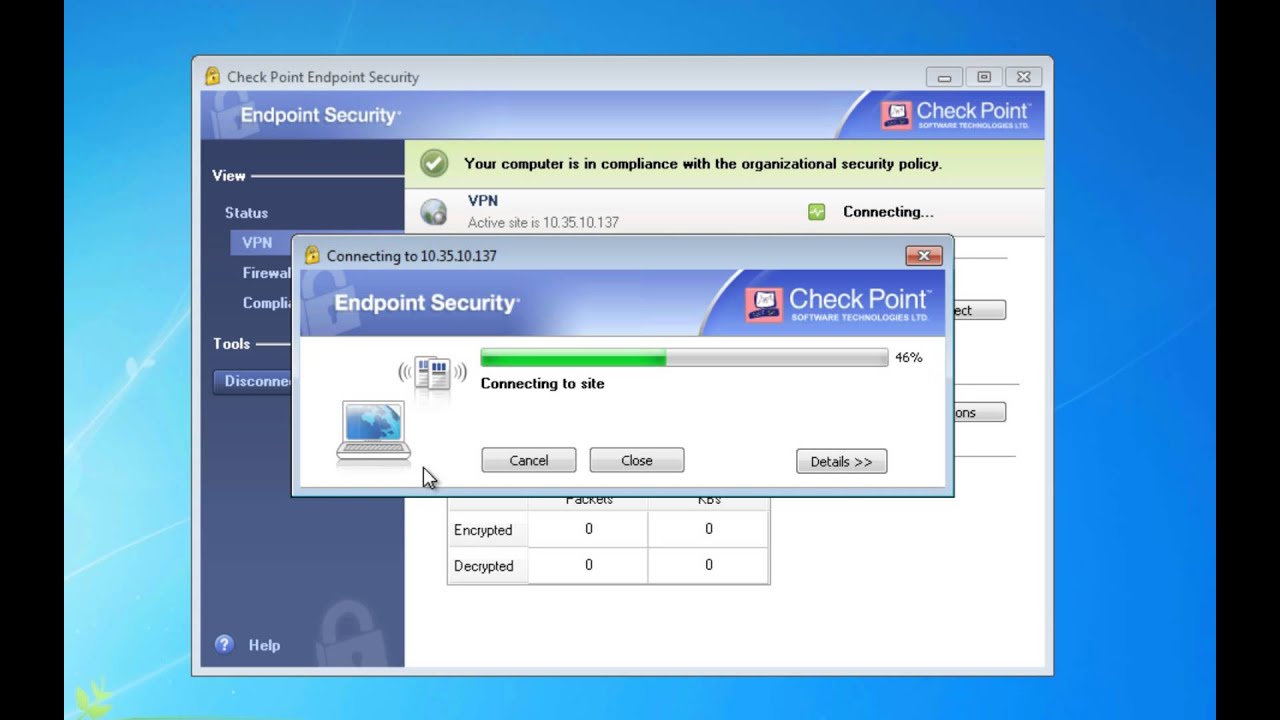
Check Point End Point Security Client Protected With Sms Passcode Youtube

Check Point Endpoint Security Vpn For Macos 10 14 Check Point Endpoint Security Vpn For Mac Os X
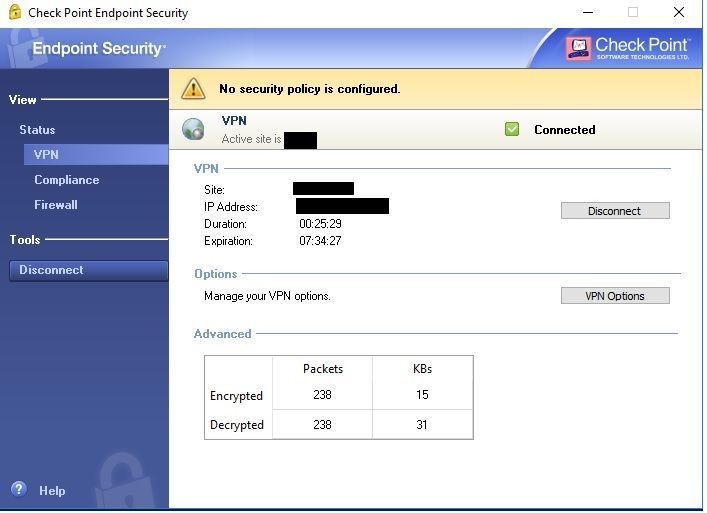
Connecting Checkpoint Vpn From Powershell Check Point Checkmates
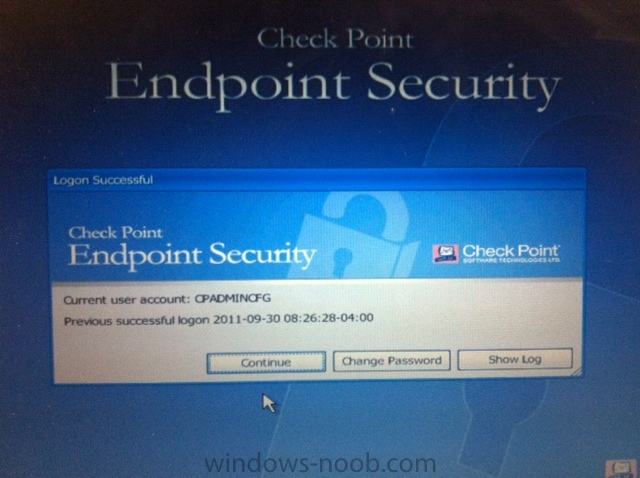
Issue With Checkpoint Encryption On Refresh Wipe Load Scenarios Unable To Read Task Sequence Configuration Disk Deploy 7 Www Windows Noob Com
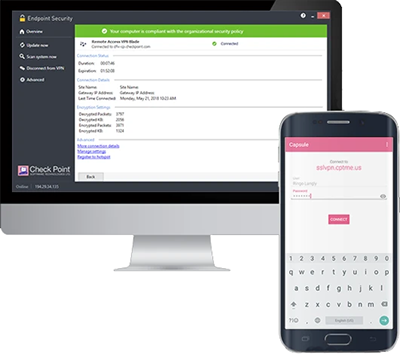
Check Point Endpoint Remote Access Vpn Software Checkfirewalls Com

Check Point Wikipedia
The Site S Security Certificate Is Not Trusted
Why Is Passcode Authentication To My Check Point Mobile Access Vpn Failing

Remote Secure Access Vpn Check Point Software
Www Uclahealth Org Compliance Workfiles Encryption Check Point Pdf

Getting And Installing Dph Vpn

Check Point Endpoint Security Download The Software Provides Data And Network Security Advanced Threat Prevention
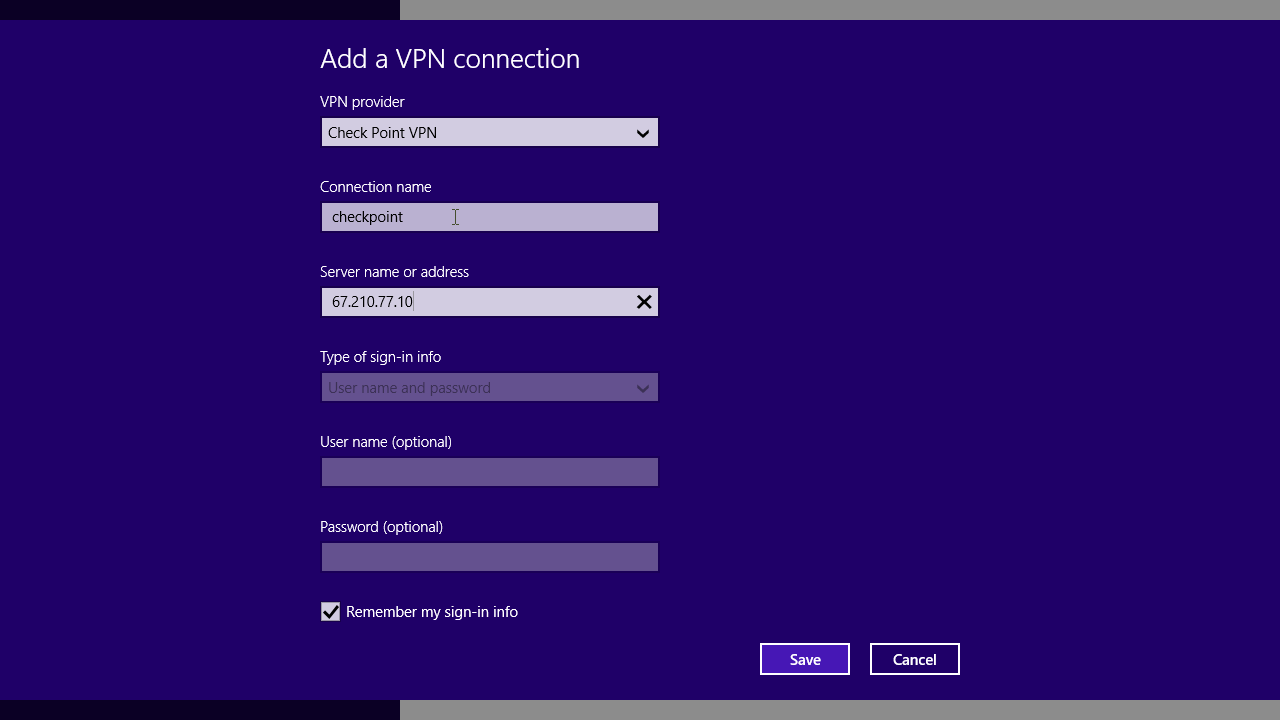
Checkpoint Vpn Client For Mac
Q Tbn And9gcsybgj2bhsvb0lieoj Ah Ecp4bgvfbjyyakhhbmqk55yed C74 Usqp Cau

Cisco Adds Check Point Next Gen Security Gateway To Growing List Of Strategic Aci Partners Cisco Blogs
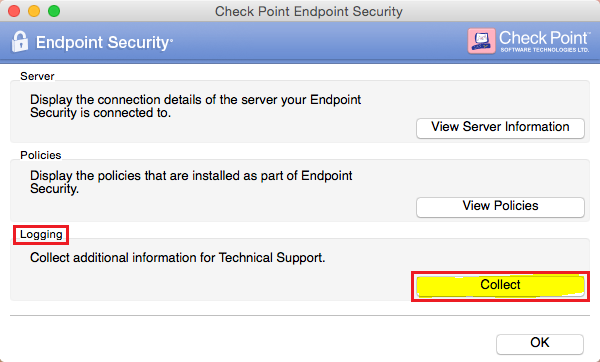
Endpoint Security Vpn For Mac 10 11 Lasopawelove

Checkpoint Portals My Internets Not Working
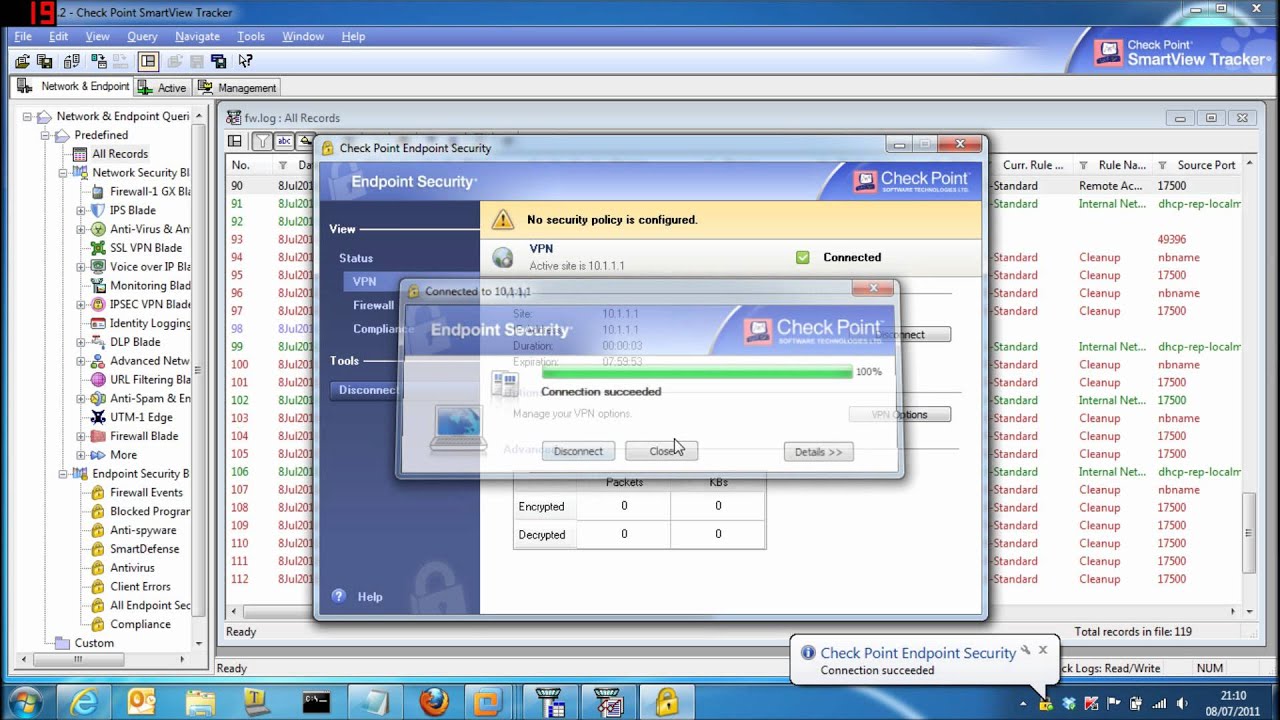
Checkpoint Vpn Software For Mac Lasopajackson

Check Point Endpoint Remote Access Vpn Software Checkfirewalls Com
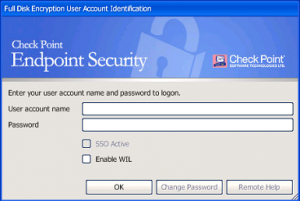
Recovering Check Point Endpoint Fde Encrypted Hard Drives

New Single Agent For Endpoint Security Help Net Security

Check Point Software Asa Computers

Getting And Installing Dph Vpn
Www Techmaxkenya Com Resources Checkpoint Endpoint Security Datasheet Pdf

How To Activate Split Tunneling In Check Point Endpoint Security Vpn Client Super User
Can T Connect Because 404 Not Found Issue 7 Schlatterbeck Snxvpn Github

Install Endpoint Security Management Server E80 70 On Gaia R77 30 03 Qos Technology

Endpoint Policy Management Checkpoint

How To Install Vpn Client On Mac Osx Information Technology Elearning
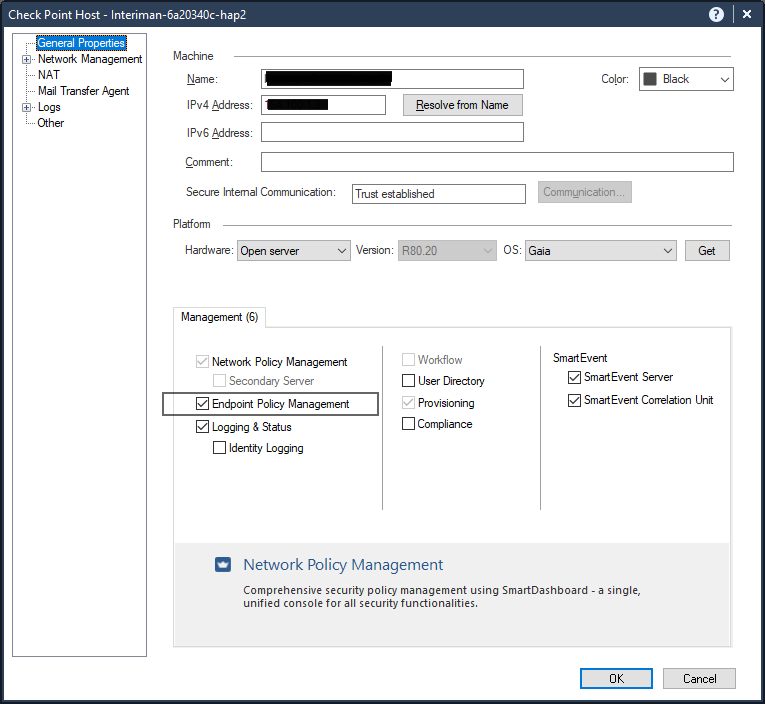
How To Deploy A Check Point Endpoint Security Management Server In Aws
1

Synergy Check Point

Can T Connect Because 404 Not Found Issue 7 Schlatterbeck Snxvpn Github
Q Tbn And9gctjt8qfiisou3jme3dkznczleu6gwybkmmksquh6mlgvxguagog Usqp Cau

Endpoint Security From Check Point Help Net Security

Check Point Security Management Server Installation Youtube
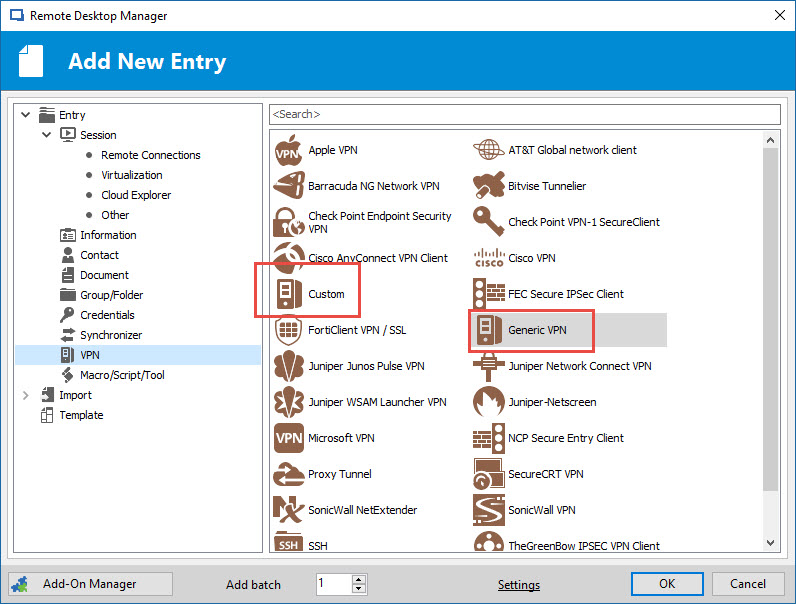
How To Setup A Custom Command Line For Vpn Devolutions Forum

2 2 Checkpoint Vpn Install Documentation Raileurope Downloads Download Euronet
Check Point Endpoint Security Alternatives And Similar Software Alternativeto Net
1
Community Rsa Com Api Core V3 Contents Data V 1

Fix Check Point Endpoint Security Unable To Connect Mikesel Hosting Ltd Downloads How To S News Reviews Rumours
Www Checkfirewalls Com Datasheets Endpoint Security Datasheet Pdf

A Privilege Escalation Vulnerability Existed In Check Point Software

Fixing A Check Point Vpn Error One Method To Resolve The Dreaded By Mark Macdonald Medium

Endpoint Connect Installation Troubleshooting Guide

Checkpoint Endpoint Connect Download For Mac Peatix
Www Polyu Edu Hk Its Remote Access Vpn New Site Pdf
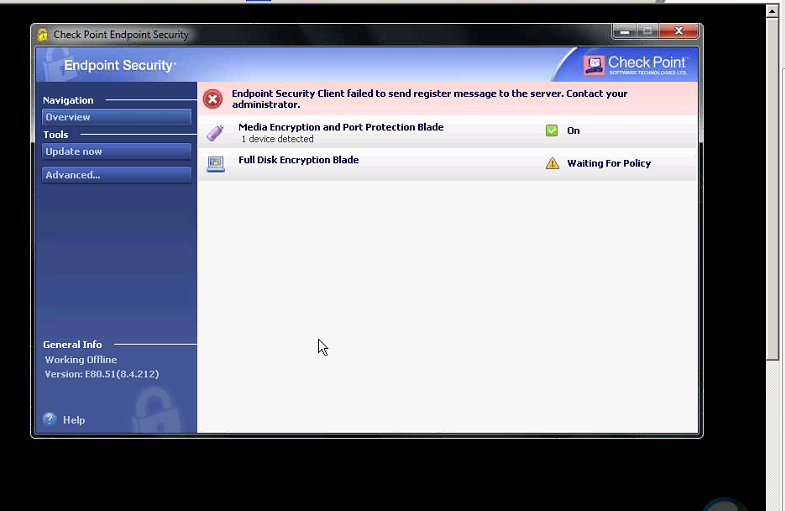
Check Point Endpoint Security Client For Mac Peatix

2 2 Checkpoint Vpn Install Documentation Raileurope Downloads Download Euronet

Check Point Encryption Solution
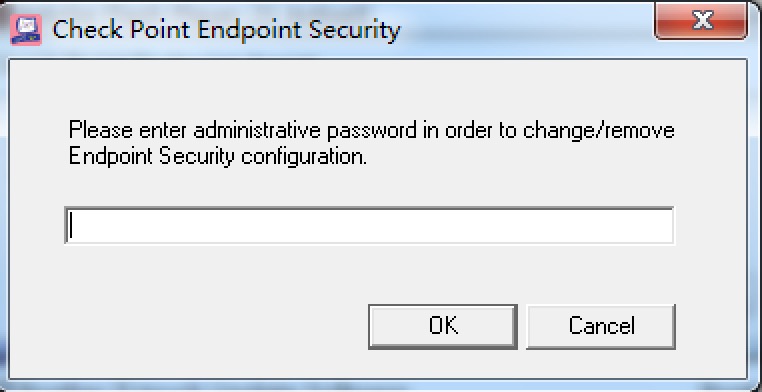
How Uninstall Endpoint Client Check Point Checkmates
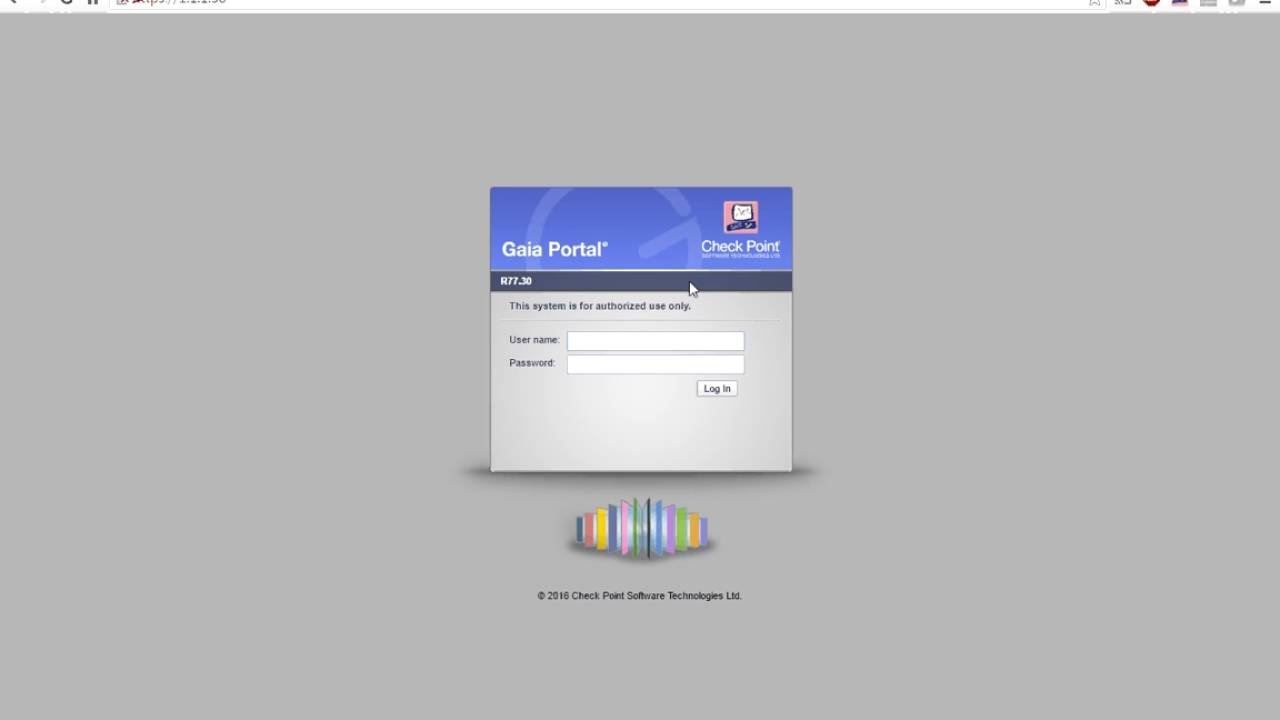
Fast Track Check Point Enterprise Endpoint Security E80 64 R77 30 02 Youtube

Check Point Endpoint Security Product Review Sc Media

Review Check Point Endpoint Security Security Itnews

Endpoint Security E80 90 Reconnected Immediately Check Point Checkmates

Confluence Mobile Technical Support

Unable To Repaire And Uninstall Checkpoint Could Check Point Checkmates

Checkpoint Endpoint Vpn Client For Mac

Check Point Endpoint Security On Demand

Check Point Data Security Jumpstart

Best Endpoint Security Software Compared And Reviewed
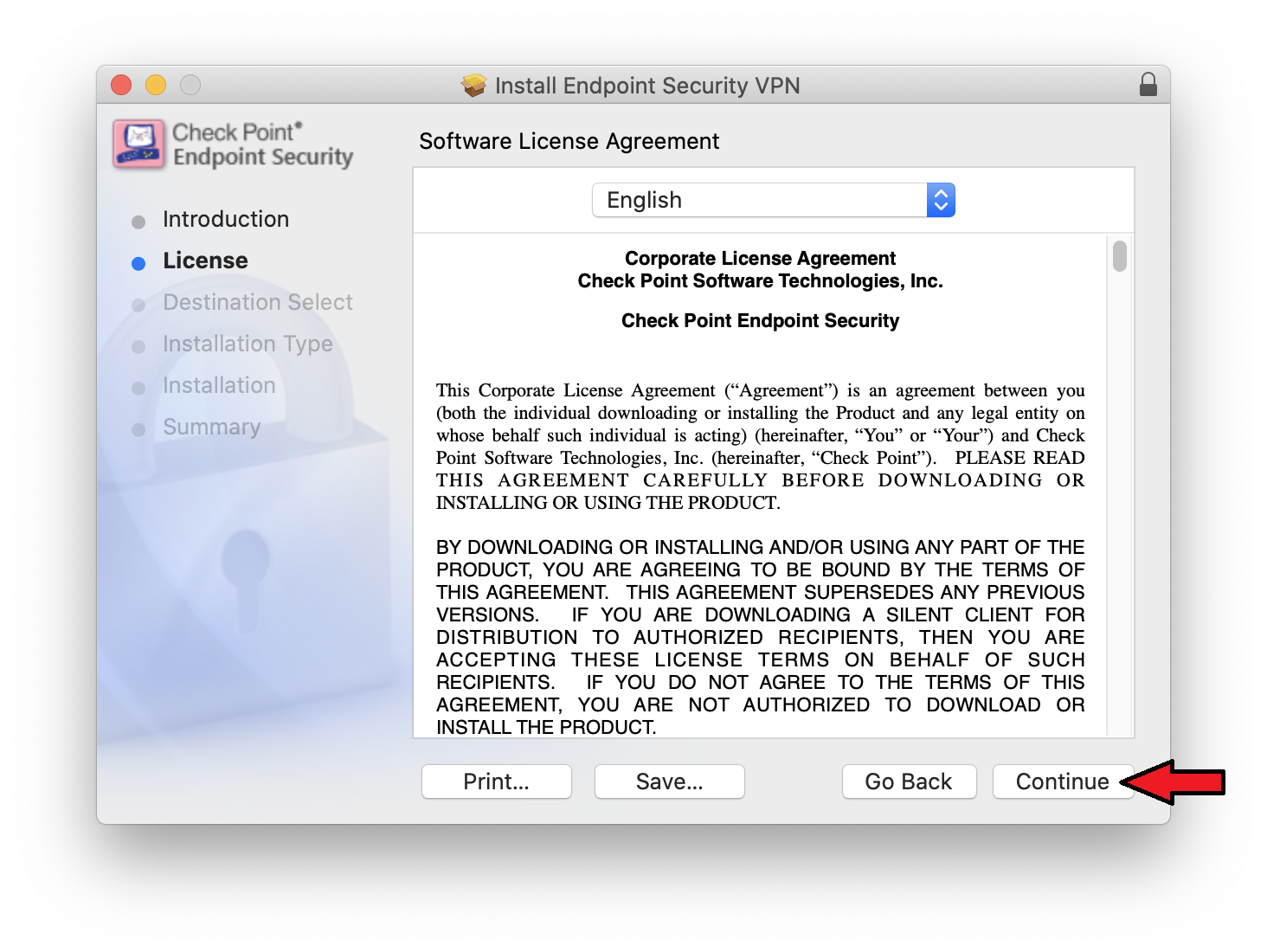
How To Install Vpn Client On Mac Osx Information Technology Elearning
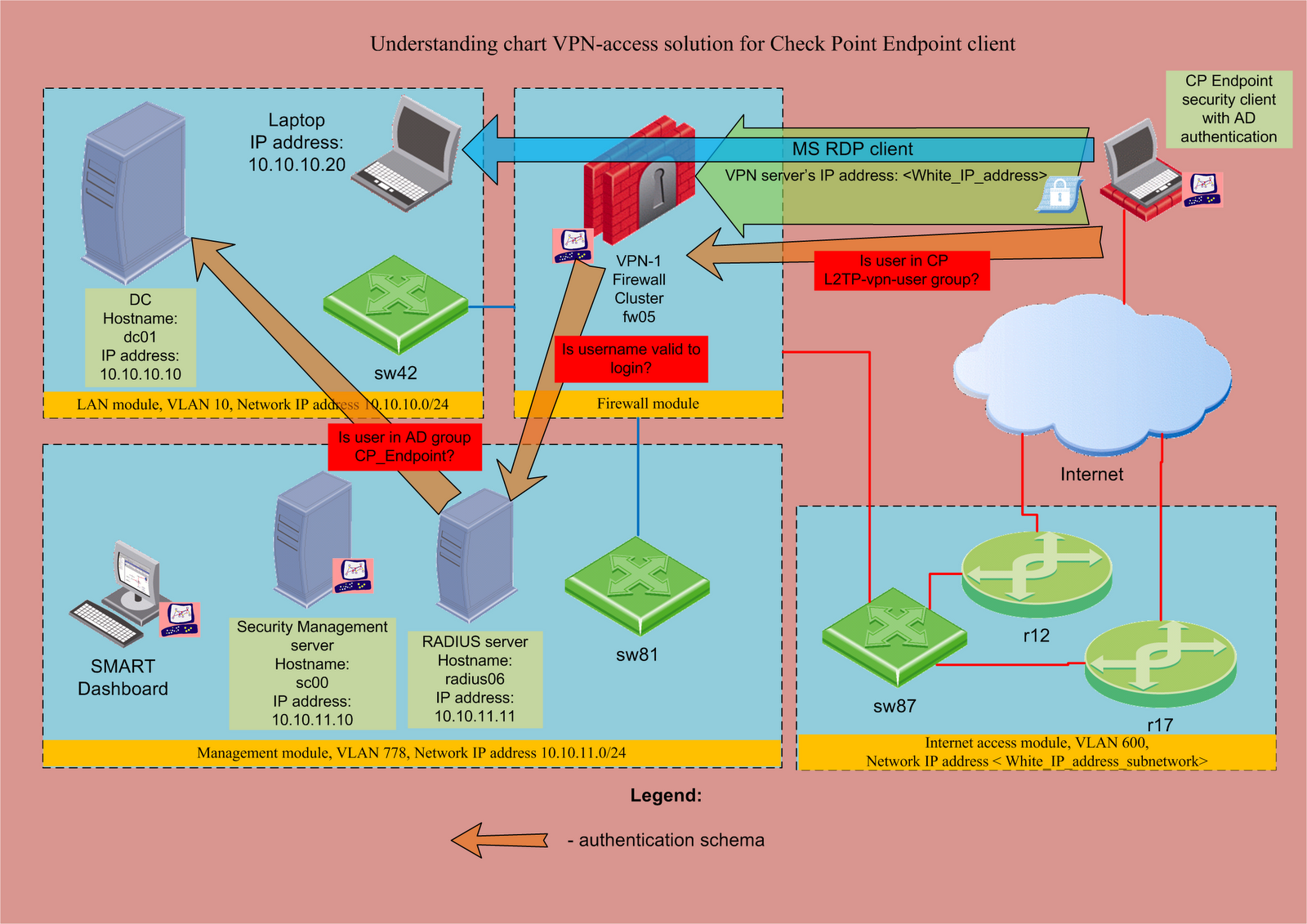
Kreyda Creating Check Point Vpn Tunnel For Remote Access Users
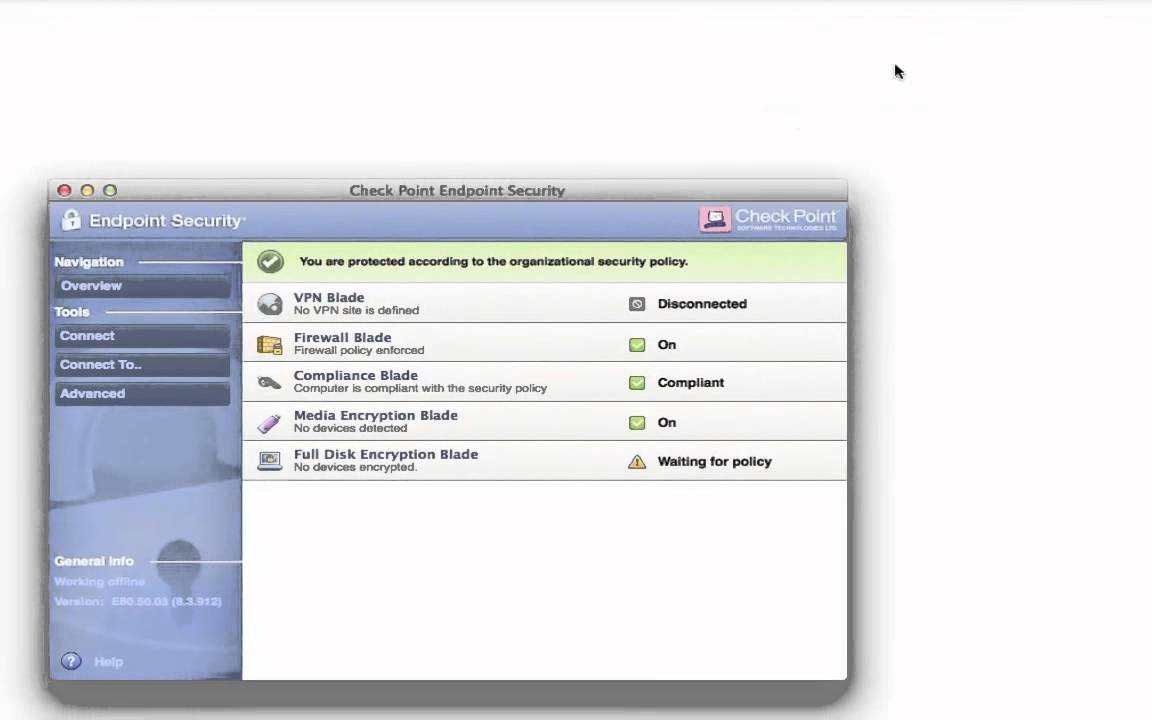
Endpoint Security Vpn For Mac Sierra Mostfasr
Cpl Thalesgroup Com Sites Default Files Integration Guide 007 0125 001 Sac Integrationguide Check Point Security gateway Cba Reva Pdf

Checkpoint Remote Access Vpn Caveats Layer 77
Www Uclahealth Org Compliance Workfiles Encryption Check Point Pdf

Endpoint Security E80 90 Reconnected Immediately Check Point Checkmates
Check Point Endpoint Security Vpn Free Download

Check Point Endpoint Security E80 40 Youtube

Getting And Installing Dph Vpn
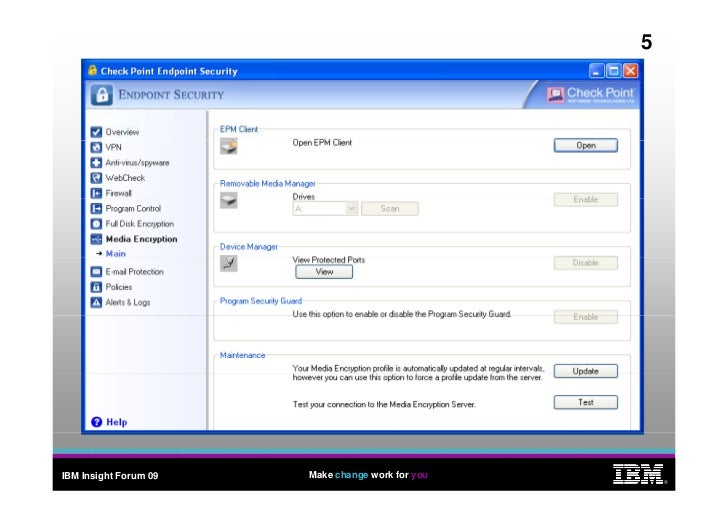
Checkpoint A Practical Demonstration Of Endpoint Security
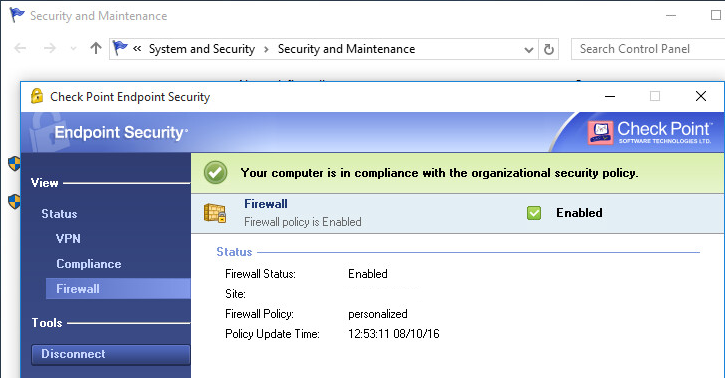
Checkpoint Endpoint Connect Download For Mac Peatix
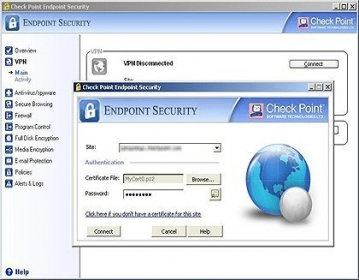
Check Point Endpoint Security On Demand Greenwaycpa
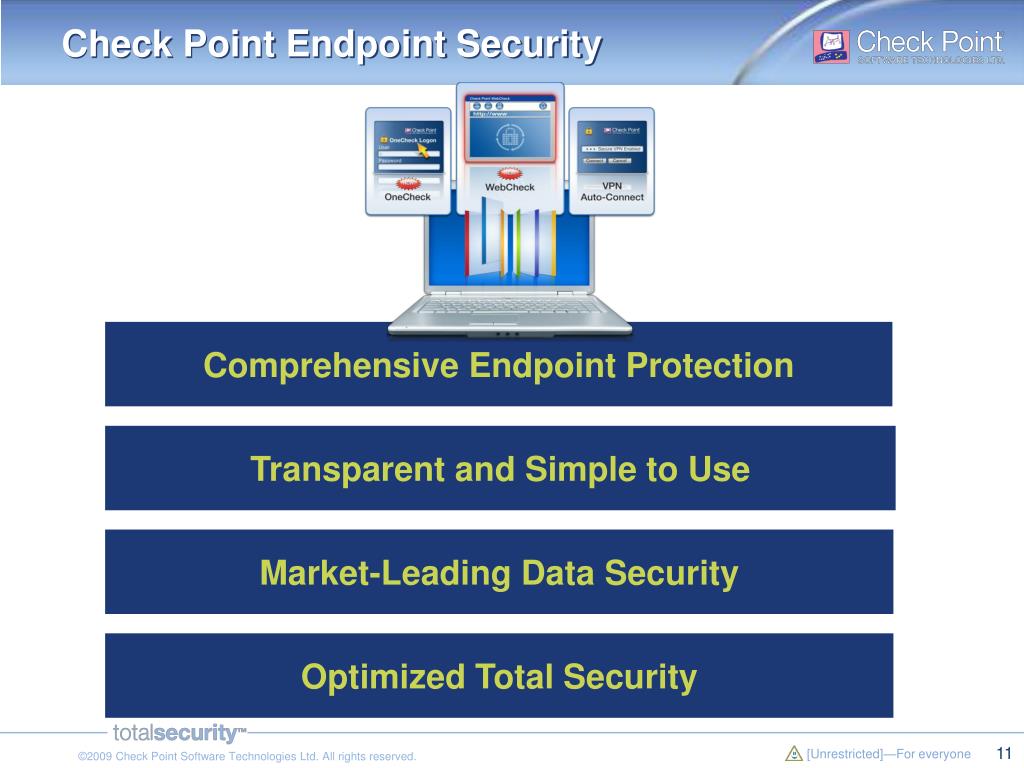
Ppt Check Point Endpoint Security Secure Fast Simple Powerpoint Presentation Id
Cpl Thalesgroup Com Sites Default Files Integration Guide 007 0125 001 Sac Integrationguide Check Point Security gateway Cba Reva Pdf
Www Insight Com Content Dam Insight En Us Pdfs Check Point Check Point Endpoint Policy Management Datasheet Pdf



