Arbor Networks Ddos Attack Map
“Today, DDoS is a complex threat that mixes flood, application and infrastructure attacks in a single, blended attack” “The people at Google Ideas have really done an amazing job bringing Arbor’s global DDoS attack data to life,” said Arbor Networks President Colin Doherty.
Arbor networks ddos attack map. According to Arbor, "The Digital Attack Map utilizes anonymous traffic data from our ATLAS threat monitoring systemto create a data visualization that allows users to explore historical trends in. Arbor conducts ongoing, Internetwide research on today’s most critical network security and management challenges Arbor Networks has collaborated with Google Ideas to create a data visualization that shows what a global problem distributed denial of service (DDoS) attacks have become Google Ideas used anonymous data from Arbor Networks’ ATLAS global threat monitoring system to build a. Arbor Networks registers more than 00 DDoS daily attacks worldwide There’s even a Digital Attack Map tool, which allows you to see where in the world DDoS attacks are occurring in realtime!.
Distributed denialofservice (DDoS) attacks are getting more frequent and harder to detect To help companies keep up with daily threat levels, Arbor Networks has collaborated with Google Ideas to create a data visualization map of global attacks. Arbor Networks,a leading provider of DDoS and advanced threat protection solutions for enterprise and service provider networks, has released its Q1 15 global DDoS attack data that shows a. You need to enable JavaScript to run this app.
Mar 2, , 11 am* Crime Eric Geller We hear about distributed denialofservice attacks all the time Now, thanks to a new. Google Ideas – which bills itself a ‘think/do’ tank – used anonymous data from Arbor Networks’ ATLAS global threat monitoring system to build the Digital Attack Map, which is a data visualization topology that allows users to explore historical trends in DDoS attacks, and make the connection to related news events on any given day. Average attack size in 1H 16 was 986Mbps, a 30 percent increase over 15 Average attack size is projected to be 115Gbps by end of 16 “The data demonstrates the need for hybrid, or multilayer DDoS defense,” said Darren Anstee, Arbor Networks Chief Security Technologist “High bandwidth attacks can only be mitigated in the cloud.
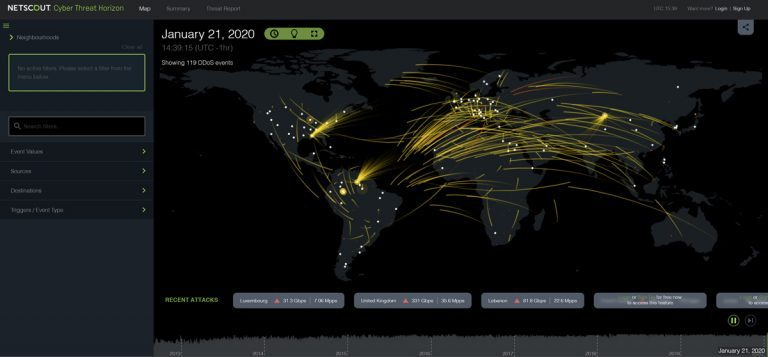
Here’s the bottom line. Arbor conducts ongoing, Internetwide research on today’s most critical network security and management challenges Arbor Networks has collaborated with Google Ideas to create a data visualization that shows what a global problem distributed denial of service (DDoS) attacks have become Google Ideas used anonymous data from Arbor Networks’ ATLAS global threat monitoring system to build a. NETSCOUT Cyber Threat Horizon provides a highly contextualized and customizable realtime view into the global cyber threat landscape.
Arbor Networks,a leading provider of DDoS and advanced threat protection solutions for enterprise and service provider networks, has released its Q1 15 global DDoS attack data that shows a continuation of extremely high volume attacks, including the largest attack ever recorded by Arbor’s ATLAS threat intelligence infrastructure, a 334Gbps attack targeting a network operator Asia. A 5Gbps DDoS attack can render most sites useless unless they have DDoS protections digitalattackmapcom Digital Attack Map, a service from Arbor Networks and Google Ideas, shows DDoS attacks. The cyber attack map from Arbor Networks is a hybrid map that was created in part with Google Ideas The Digital Attack Map tracks DDoS attacks with data from Arbor's ATLAS threat intelligence.
Today, DDoS is a complex threat that mixes flood, application and infrastructure attacks in a single, blended attack "The people at Google Ideas have really done an amazing job bringing Arbor's global DDoS attack data to life," said Arbor Networks president Colin Doherty. Thwart Hackers, and Keep Your Network Up and Running DDoS attacks remain a popular method for hackers to disrupt network operations According to Arbor Network’s research, the size of DDoS attacks has grown 4,900 percent in the past 10 years, peaking at 400 Gbps last year This growing threat can disrupt and take down websites and block traffic. Check out the Digital Attack Map It was produced in a collaborative effort by Google Ideas and Arbor Networks to raise awareness about distributed denial of service attacks In computing, a denialofservice attack (DoS attack) or distributed denialofservice attack (DDoS attack) is an attempt to make a machine or network resource unavailable.
Arbor has a long history in botnet research and DDoS mitigation However, as DDoS has moved from just a diversion to be a feature of malware and botnets used in cybercrime and APT attacks, NETSCOUT has expanded Arbor's research team and research capabilities to tackle additional threat types. MAP Find out if you are under cyberattack here. This interesting tidbit comes from Google’s new “Digital Attack Map,” a collaboration between the company’s Internetthemed think tank and the threatmonitoring service Arbor Networks The.
Digital Attack Map is a live data visualization of DDoS attacks around the globe, built through a collaboration between Google Ideas and Arbor Networks The tool surfaces anonymous attack traffic data to let users explore historic trends and find reports of outages happening on a given day. The attack map shared by Anonymous, Hutchins said, shows a "random sample of global DDoS traffic badly plotted on a world map" and does not indicate an actual attack. Check out the Digital Attack Map It was produced in a collaborative effort by Google Ideas and Arbor Networks to raise awareness about distributed denial of service attacks In computing, a denialofservice attack (DoS attack) or distributed denialofservice attack (DDoS attack) is an attempt to make a machine or network resource unavailable.
This map lets you watch DDoS attacks in real time So much DDoS!. Arbor Networks announced an enhanced version of the Digital Attack Map, a live data visualization of distributed denialofservice (DDoS) attacks around the globe The Digital Attack Map uses data from Arbor Networks’ Active Threat Level Analysis System (ATLAS), a globally scoped threat monitoring network that currently collects 140Tbps of. Arbor Networks announced an enhanced version of the Digital Attack Map, a live data visualization of distributed denialofservice (DDoS) attacks around the globe The Digital Attack Map uses data from Arbor Networks’ Active Threat Level Analysis System (ATLAS), a globally scoped threat monitoring network that currently collects 140Tbps of.
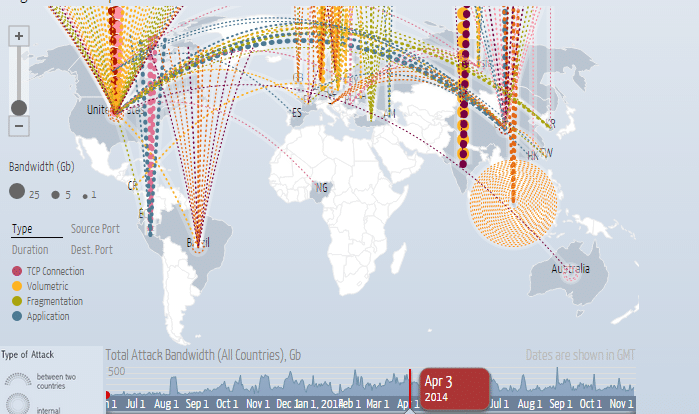
A service to automatically detect threats and proactively resolve DDoS attacks Shield your applications and systems from DDoS attacks with our cloudbased DDoS Protection This subscriptionbased service protects your network against volumetric attacks by automatically identifying and mitigating threats. Digital Attack Map DDoS attacks around the globe Type Source Port Duration Dest Port Map Table A DDoS attack is an attempt to make an online service unavailable to users Large Shows the top reported attacks by size for a given day DDoS data ©, Arbor Networks, Inc. In spite of mounting evidence in support of Prince’s theory, the @YourAnonCentral Twitter account doubled down on its claims that the outages were linked to a DDoS attack, reportedly posting screenshots of a DDoS digital attack map belonging to the cybersecurity firm Arbor Networks The DDoS cyber attack theory was later debunked officially.
Centralized Management and Enhanced Cloud Signaling Provides Automated Protection Against Known and Emerging Threats from the Data Center to the Cloud Jun 6, 17 Arbor Networks Inc, the security division of NETSCOUT (NASDAQ NTCT), announced a new version of its onpremise, alwayson, inline distributed denialofservice (DDoS) detection and mitigation platform for enterprise customers. Arbor Networks brings you one of today’s most popular attack maps This map is dedicated to tracking down incidents related to DDoS attacks around the globe The data is gathered by the Arbor Networks ATLAS® global threat intelligence system, coming from a worldwide analysis of 300 ISPs with over 130 Tbps of live traffic. The Digital Attack Map, created by Google Ideas and Arbor Networks, is a live data visualization of Distributed Denial of Service (DDoS) attacks that take down websites and people's access to information and businesses around the globe.
Arbor Networks is one of the most popular attack maps This map is devoted to tracking down attack episodes related to DDoS attacks around the world Arbor Networks ATLAS® global threat intelligence system has gathered and presented the data, which comes from a worldwide analysis of 300 ISPs with over 130 Tbps of live traffic. “Today, DDoS is a complex threat that mixes flood, application and infrastructure attacks in a single, blended attack” “The people at Google Ideas have really done an amazing job bringing Arbor’s global DDoS attack data to life,” said Arbor Networks President Colin Doherty. Arbor conducts ongoing, Internetwide research on today’s most critical network security and management challenges Arbor Networks has collaborated with Google Ideas to create a data visualization that shows what a global problem distributed denial of service (DDoS) attacks have become Google Ideas used anonymous data from Arbor Networks’ ATLAS global threat monitoring system to build a.
Arbor Networks DDoS Attack Map The Arbor Networks map is dedicated to recording DDoS attacks worldwide DDoS stands for Distributed Denial of Service It’s a virulent attempt to disturb the usual internet traffic of a specific server by flooding it with traffic from a variety of sources. Arbor Networks has published the statistics of the DDoS attacks in the first half of 16 The largest one went up to 579Gbps An interactive map shows the DDoS attacks made on a global level. Arbor Networks Inc today released global distributed denialofservice attack data for the first six months of 16, which shows a continuing escalation in both the size and frequency of attacks.
Average attack size in 1H 16 was 986Mbps, a 30 percent increase over 15 Average attack size is projected to be 115Gbps by end of 16 “The data demonstrates the need for hybrid, or multilayer DDoS defense,” said Darren Anstee, Arbor Networks Chief Security Technologist “High bandwidth attacks can only be mitigated in the cloud. Every day, thousands of digital attacks are happening around the globe The site Digital Attack Maps shows the leading Distributed Denial of Service (DDoS) attacks happening at the moment The data is consolidated from more than 270 ISP customers who have agreed to anonymously share their network traffic and attack statistics. Digital Attack Map is a live data visualization of DDoS attacks around the globe, built through a collaboration between Google Ideas and Arbor Networks The tool surfaces anonymous attack traffic data to let users explore historic trends and find reports of outages happening on a given day.
DDoS visualization The Digital Attack Map is a free service from Arbor Networks and Jigsaw It combines both daily and historic details to display a global map with DDoS attacks. Arbor Networks DDoS Attack Map (Click Link) https Cyber Security Architecture Prepare a baseline diagram of your computer systems and network and make recommendations to enhance the security associated with applications, databases, POS systems, and connecting devices A review of your cloud services and business continuity / incident. The Digital Attack Map, Arbor’s live DDoS and cyberattack map, provides a live visualization of DDoS attacks throughout the world, offering a stunning visualization of how pervasive DDoS threats have become.
Arbor Networks has partnered with Google Ideas to create the Digital Attack Map, a LIVE data visualization of DDoS and cyber attacks throughout the world Click to View the Map. DDoS Attacks Increase in Size, Frequency, and Complexity According to Arbor Networks 14 10th Annual Worldwide Infrastructure Security Report, 73 percent of service provider customers experienced a DDoS attack and 55 percent of service providers experienced a DDoS attack against their infrastructure. Arbor Networks APS provides proven, onpremise DDoS protection for the world's most critical enterprise and government networks Enhanced by integrated DDoS detection and DDoS mitigation capabilities, together with automatic security updates delivered by Arbor's Security Engineering and Response Team (ASERT), APS delivers DDoS mitigation against both known and emerging availability threats so.
Arbor Networks Inc, a leading provider of DDoS and advanced threat protection solutions for enterprise and service provider networks, has released Q1 DDoS attack data showing that DDoS attack activity in Australia is shorter in duration, but still just as dangerous Attackers in Australia are also continuing to gravitate towards reflection/amplification attacks as their threat vector of. Arbor Networks has partnered with Google Ideas to create the Digital Attack Map, a LIVE data visualization of DDoS and cyber attacks throughout the world Click to View the Map. The Digital Attack Map, created by Google Ideas and Arbor Networks, is a live data visualization of Distributed Denial of Service (DDoS) attacks that take down websites and people's access to information and businesses around the globe.
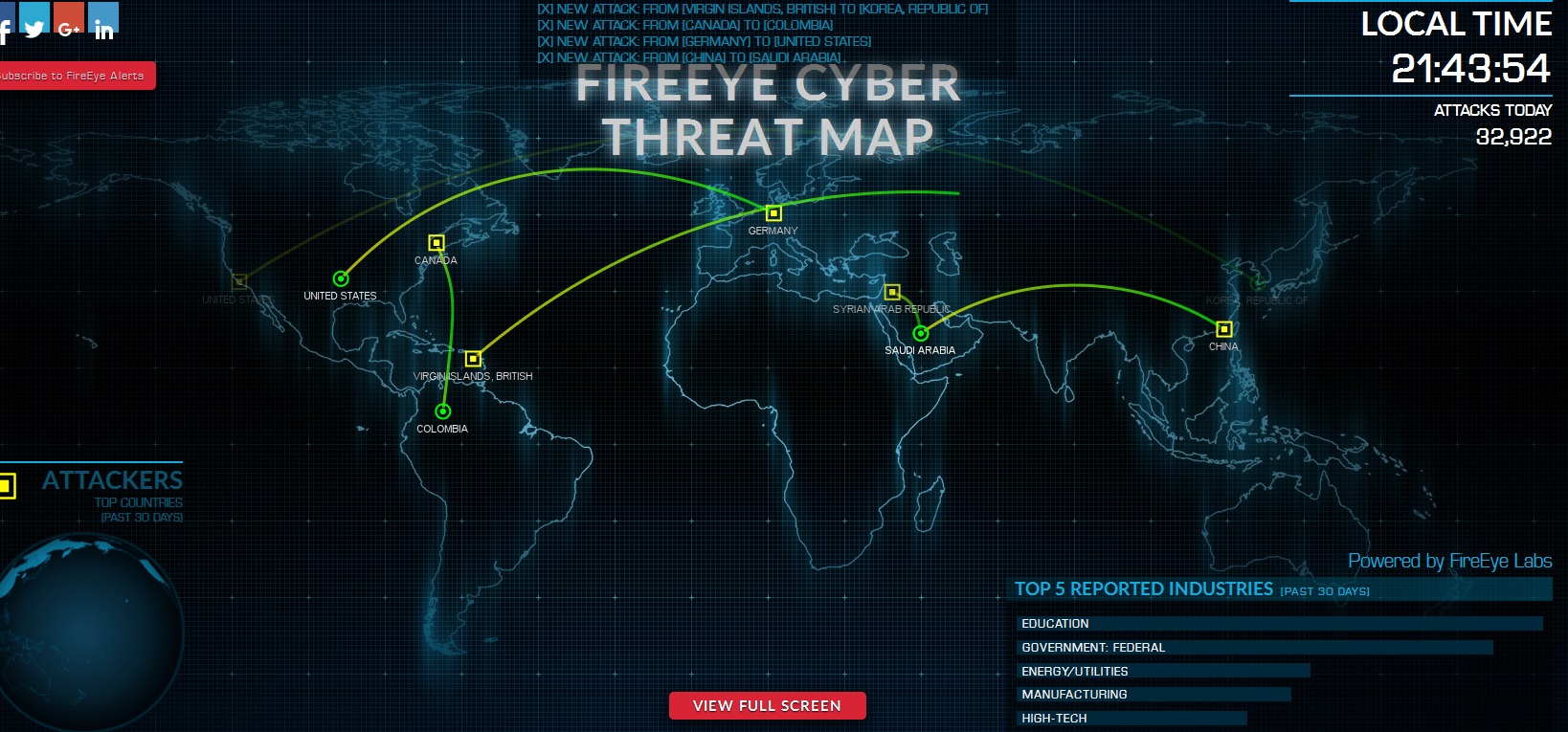
Today, DDoS is a complex threat that mixes flood, application and infrastructure attacks in a single, blended attack "The people at Google Ideas have really done an amazing job bringing Arbor's global DDoS attack data to life," said Arbor Networks president Colin Doherty. Here’s a few cyber threat maps showing attacks live FireEye Kaspersky Norse Arbor Networks DDoS Attacks Honeynetorg Anubisnetworks Security Wizardry Alien Vault FSecure TrendMicro Global Sp. DDoS protection – protection solutions that are proven in the world’s most demanding networks Advanced threats – for networkwide situational awareness, broad and deep traffic visibility and dynamic security intelligence Network visibility – intelligent analysis of data from across the network allows organisations to detect threats, improve traffic engineering, provide business.
Arbor Networks Inc , a leading provider of DDoS and advanced threat protection solutions for enterprise and service provider networks, has released Q2, 15 global DDoS attack data that shows strong growth in the average size of DDoS attacks, from both a bitspersecond and packetspersecond perspective The largest attack monitored in Q2 was a 196GB/sec UDP flood, a large, but no longer. Arbor Networks has collaborated with Google Ideas to create a data visualization that shows what a global problem distributed denial of service (DDoS) attacks have become Google Ideas used anonymous data from Arbor Networks’ DDoS attacks to build a data visualization that allows users to explore historical trends in, and make the connection to related news events on any given day. In a bid to highlight what a threat DDoS attacks are, Google Ideas has teamed up with Arbor Networks to bring the data to life Then Digital Attack Map is a live data visualisation of Distributed.
Digital Attack Map — a DDOS attack map built through a collaboration between Google Ideas and Arbor Networks — enables users to track DDoS attacks by size or type Attacks are visualized as an arc that travels from the source of the attack to its target The map is very simple to use, which makes it the perfect choice for business owners or. Arbor Networks has published the statistics of the DDoS attacks in the first half of 16 The largest one went up to 579Gbps An interactive map shows the DDoS attacks made on a global level. Haritası Ddos & Cyber Attack Map Netscout Cyber Threat Horizon Ddos Saldırı Haritası Ddos Saldırı Haritası Arbor Networks Ddos Saldırı Haritası Ddos Atak Haritası Ddos Saldırısı Haritası Ddos Saldırı Haritası Ddos Saldırı Map Ddos Attack Haritası.
Google Ideas used anonymous data from Arbor Networks' ATLAS® global threat monitoring system to build a data visualization that allows users to explore historical trends in DDoS attacks, and make.

Mapping Global Ddos Attacks Center For Data Innovation

Top 10 Cyber Attack Maps To See Digital Threats For

Track Cyber Attacks Happening All Over The World Using These Maps
Arbor Networks Ddos Attack Map のギャラリー
2

Are You Vulnerable To A Ddos Attack Netscout
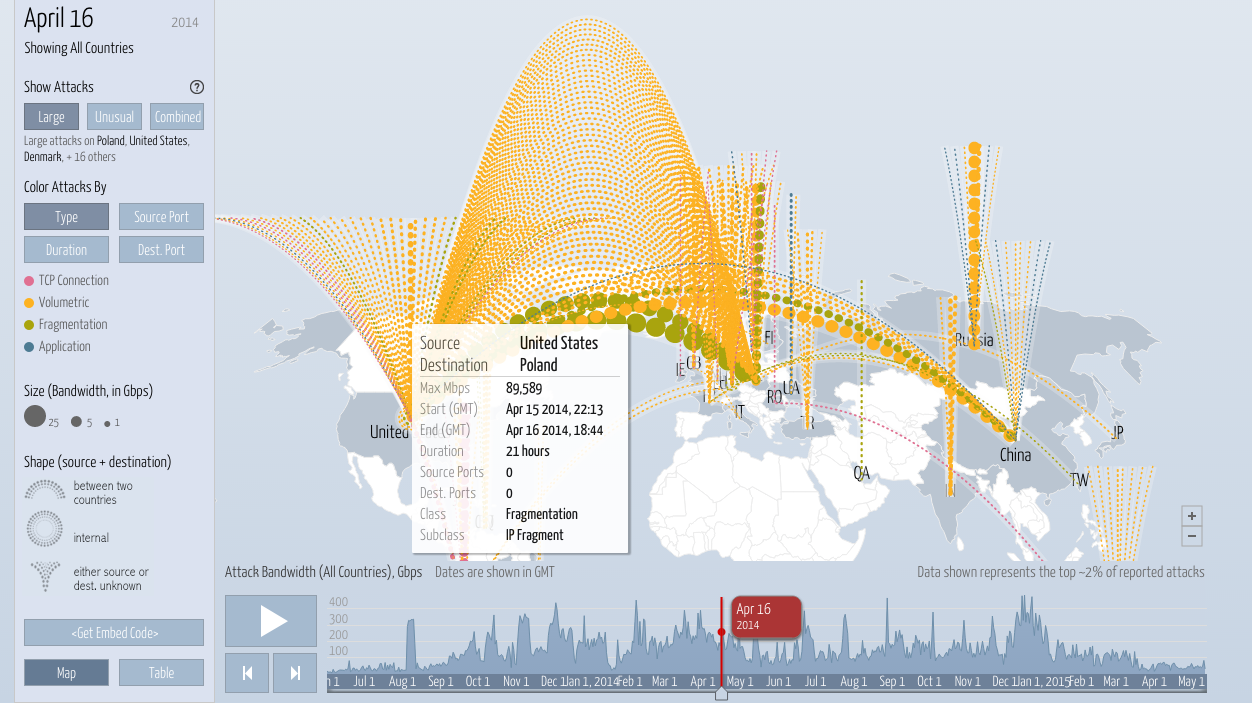
Ddos And You

Mapping Cybersecurity Mayhem Strategic Finance
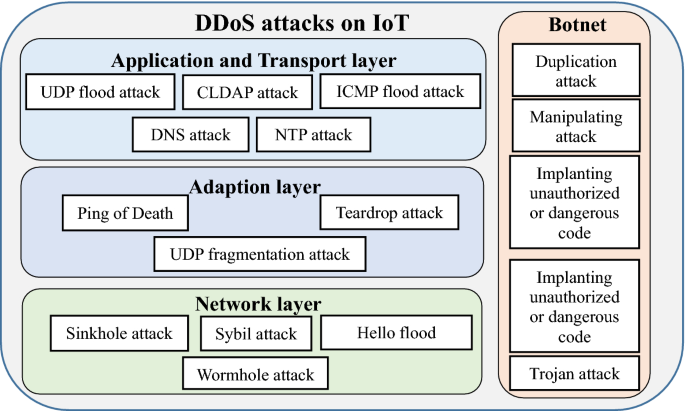
Distributed Denial Of Service Attacks And Its Defenses In Iot A Survey Springerlink

Live Map For Cyber Attacks Shahrukh A Siddiqui
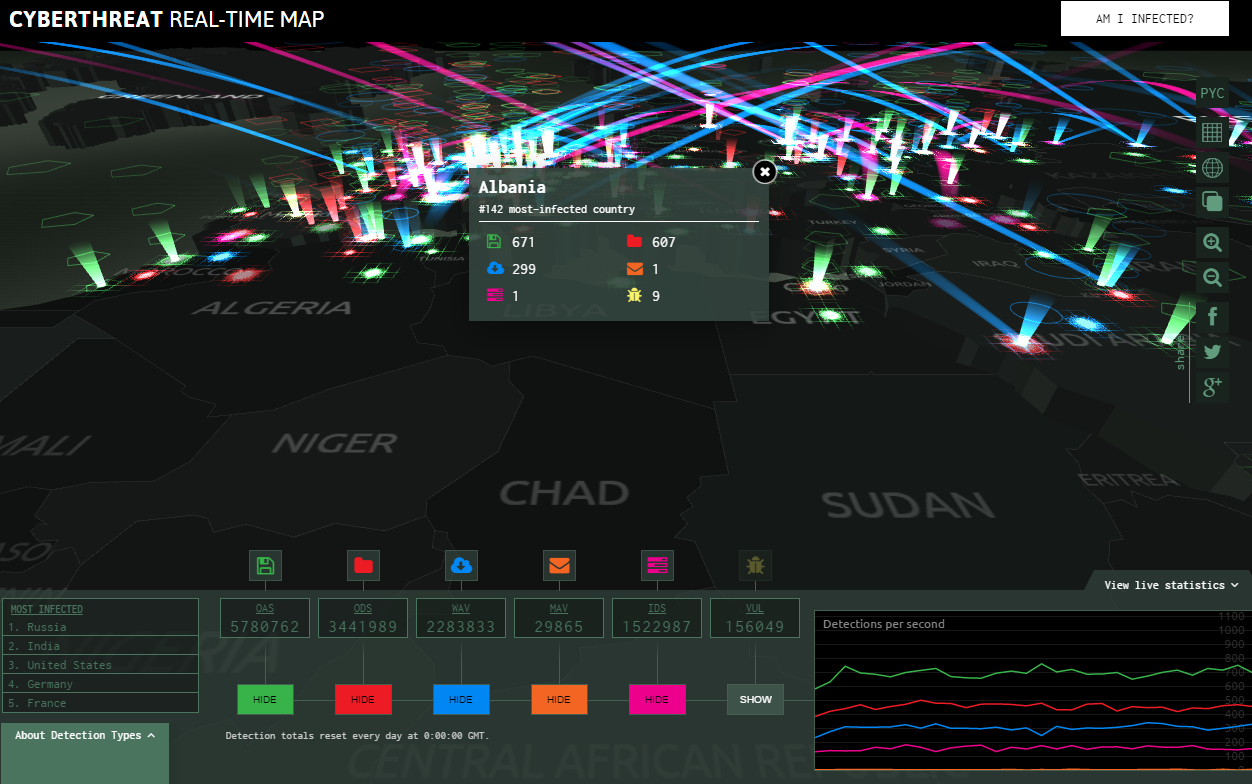
Who S Attacking Whom Realtime Attack Trackers Krebs On Security
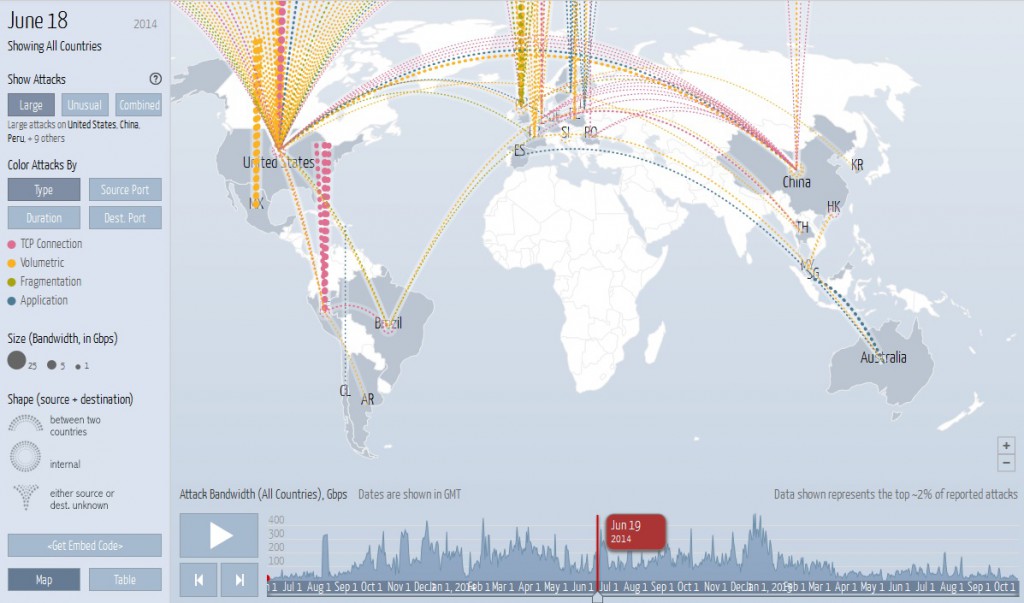
Top 7 Cyber Attack Maps Hacking News
Q Tbn And9gcq1c8lw9pnae0y 7btxyy4o92buavegkd2hoc93flkfzi1dk6u5 Usqp Cau

Arbor Networks Records Largest Ever Ddos Attack In Q1 15 Ddos Report Business Wire

What Is A Ddos Attack All Things Internet Informatics Inc

What Is Real Time Cyber Attack Map Logsign
Top 15 Cyber Attack Maps For Visualizing Incidents
Top 7 Cyber Attack Maps Hacking News

11 Interesting Ways To Watch Cyberattack In Real Time Worldwide

Ddos Cyber Attack Map Today Netscout Cyber Threat Horizon
Watch Realtime Cyber Attacks With Ddos Attack Map

Google Ideas Arbor S Digital Attack Map
8 Top Cyber Attack Maps And How To Use Them Cso Online
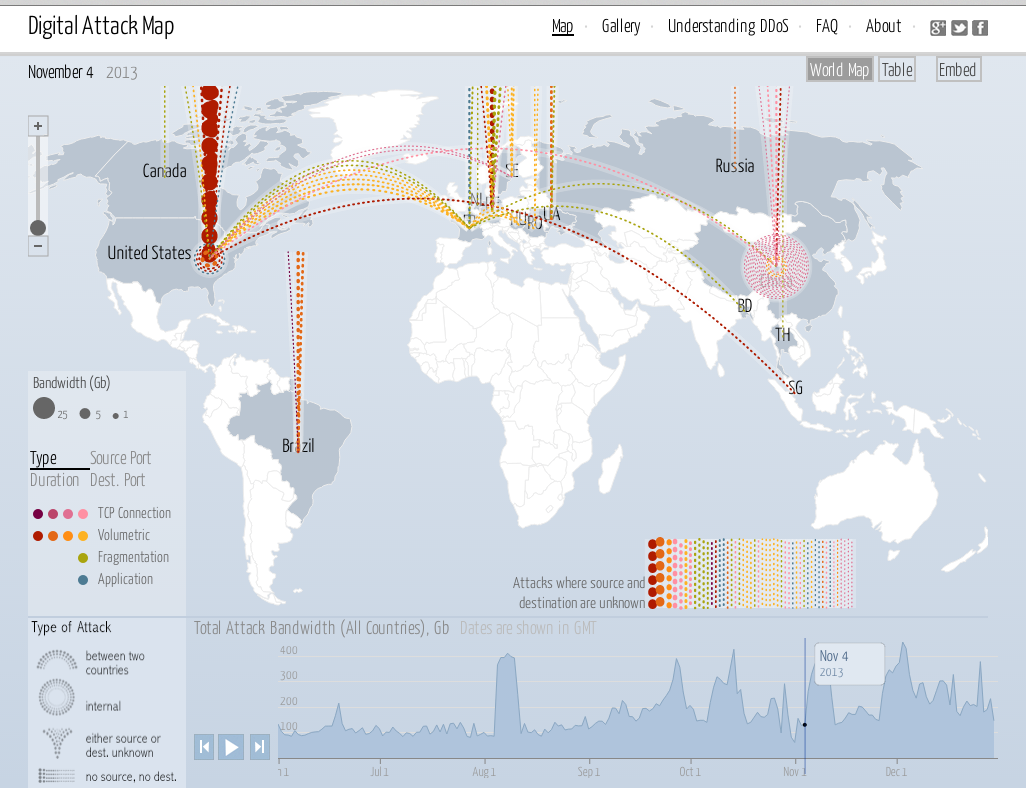
Digital Attack Map

Who S Attacking Whom Realtime Attack Trackers Krebs On Security
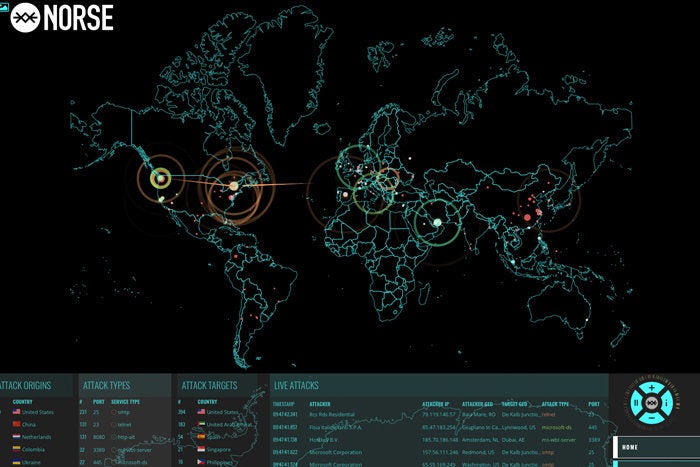
8 Top Cyber Attack Maps And How To Use Them Cso Online

Shadowserver Foundation Stats Ddoshistorical
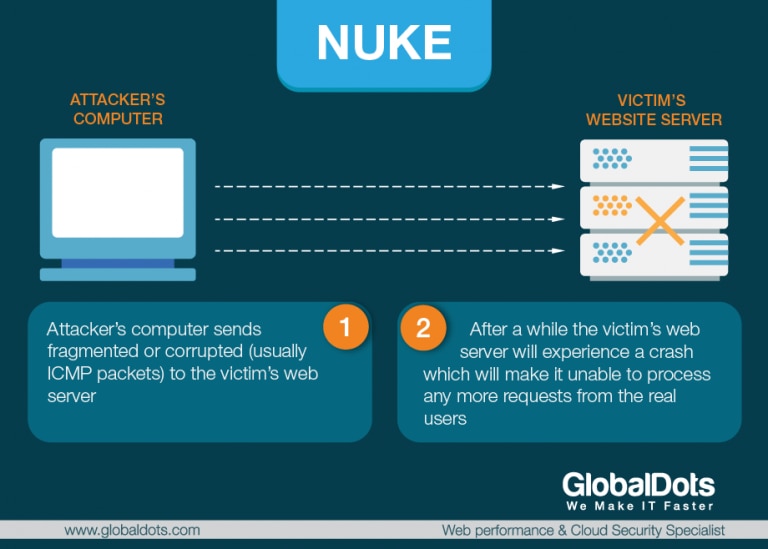
Ddos Protection Mitigation Distributed Denial Of Service Explained
Http Dcnds Asia Wp Content Uploads 19 12 Dr Anbar Mirai Botnet Pdf

Is Ddos Attack Illegal Know About Ddos Attack In Detail

Top 10 Cyber Attack Maps To Track Cybersecurity Incidents

Real Time Threat Maps Controltrends

Real Time Threat Maps Controltrends

Top 15 Live Cyber Attack Maps For Visualizing Digital Threat Incidents Norse Corp Com
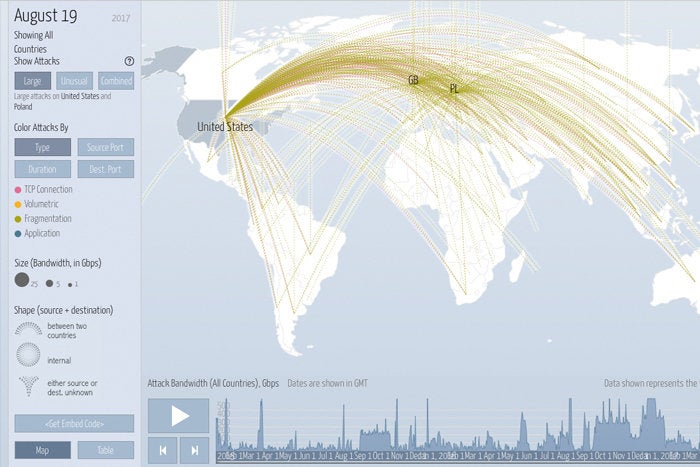
8 Top Cyber Attack Maps And How To Use Them Cso Online

Top 8 Cyber Threat Maps To Track Cyber Attacks

Ddos Attack World Map Infradata

Top 10 Cyber Attack Maps To See Digital Threats For

Arbor Networks Google Draw Digital Attack Map Zdnet
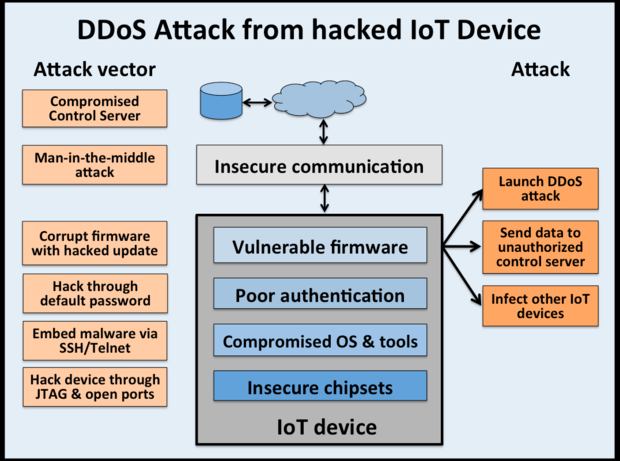
Ddos Attacks Using Iot Devices Follow The Manchurian Candidate Model Network World
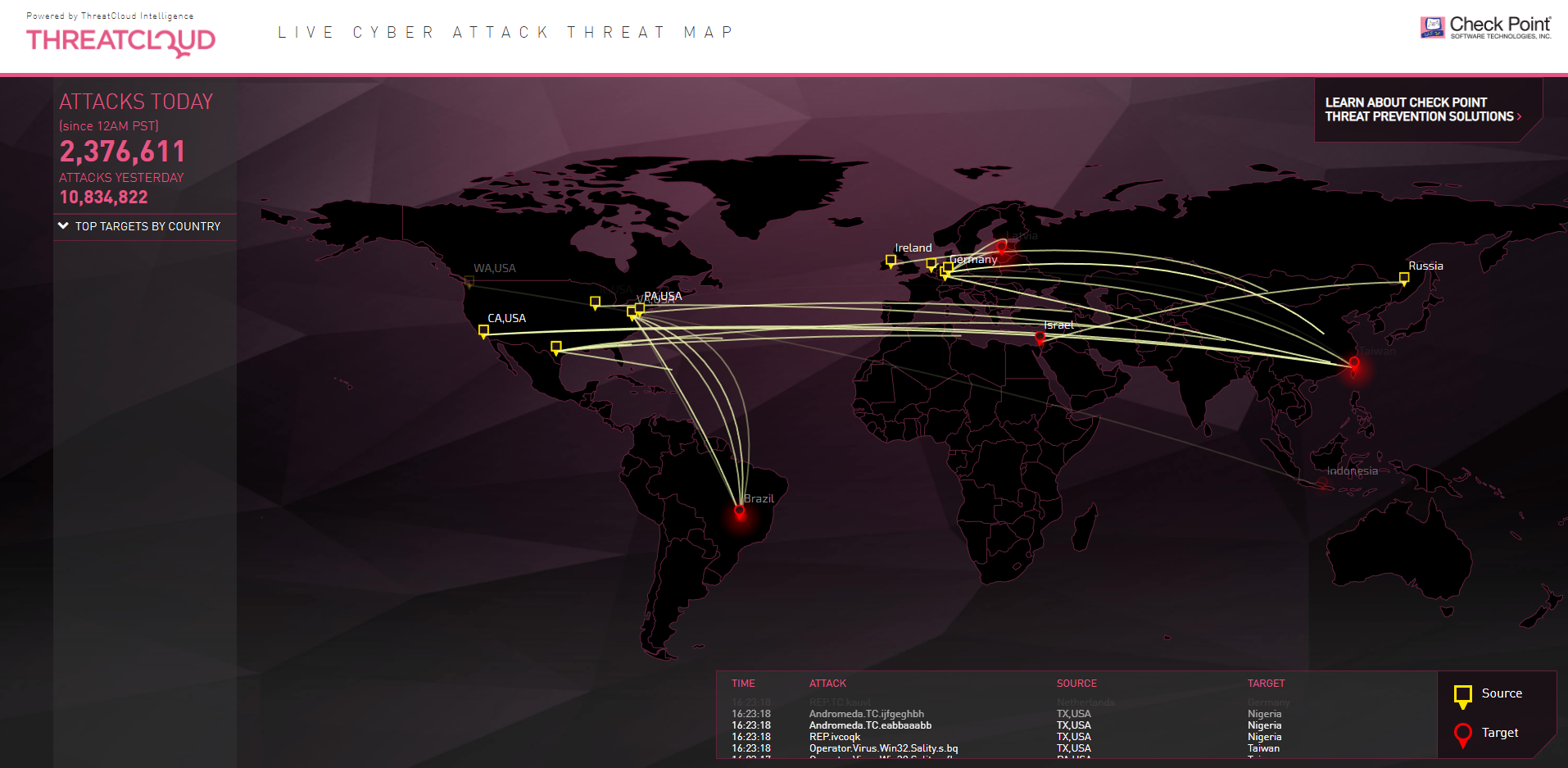
Top Ten Hacking Attack Maps And How They Can Help You
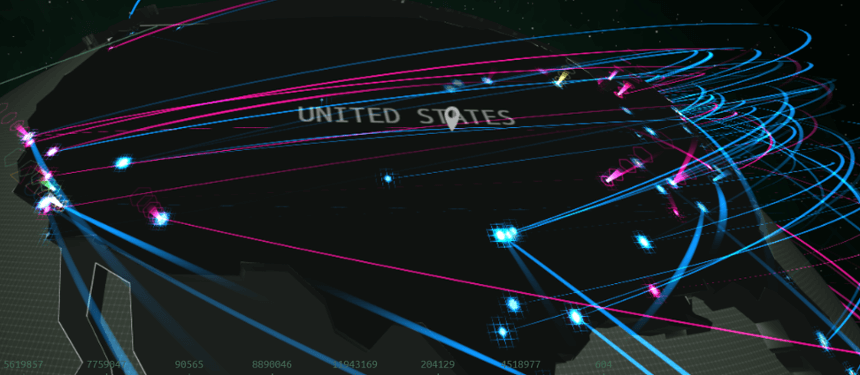
7 Live Cyber Attack Maps
Converge Network Digest Arbor Networks Updates Ddos Digital Attack Map With Jigsaw
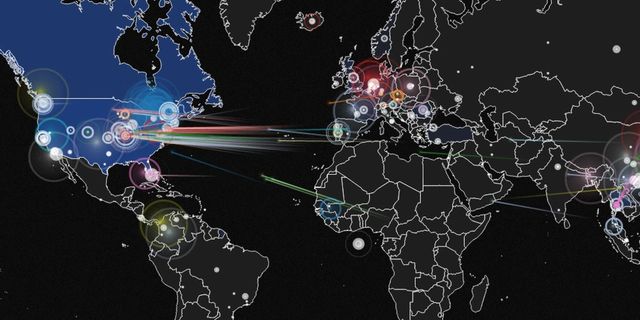
8 Top Cyber Attack Maps And How To Use Them

Report Fueled By Iot Devices Ddos Attacks Rising In Size Frequency Cyberscoop

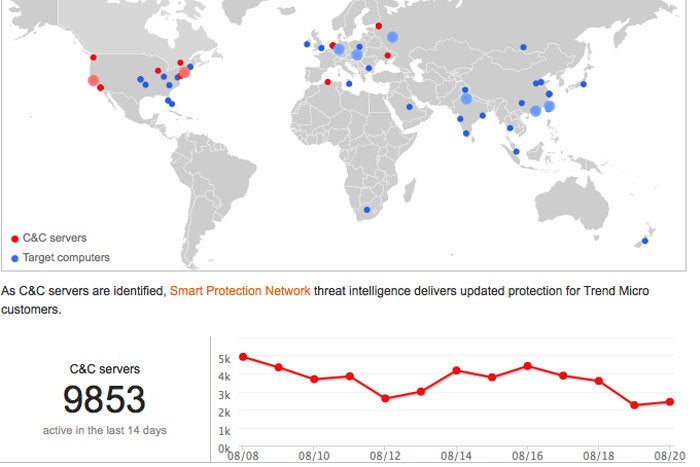
Data Visualization Of Global Ddos Attacks Help Net Security

Digitalattackmap
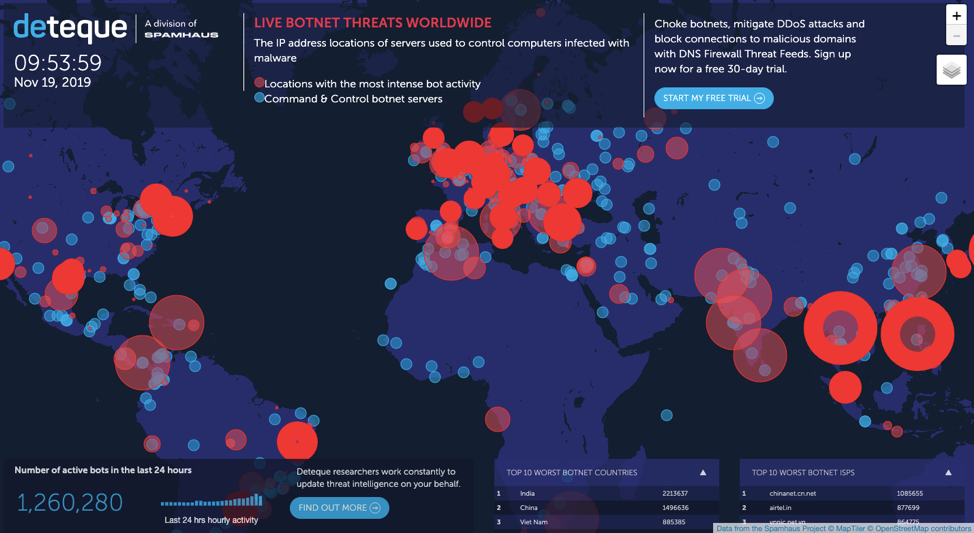
Top 8 Cyber Threat Maps To Track Cyber Attacks
Map Shows Global Denial Of Service Attack Business Insider
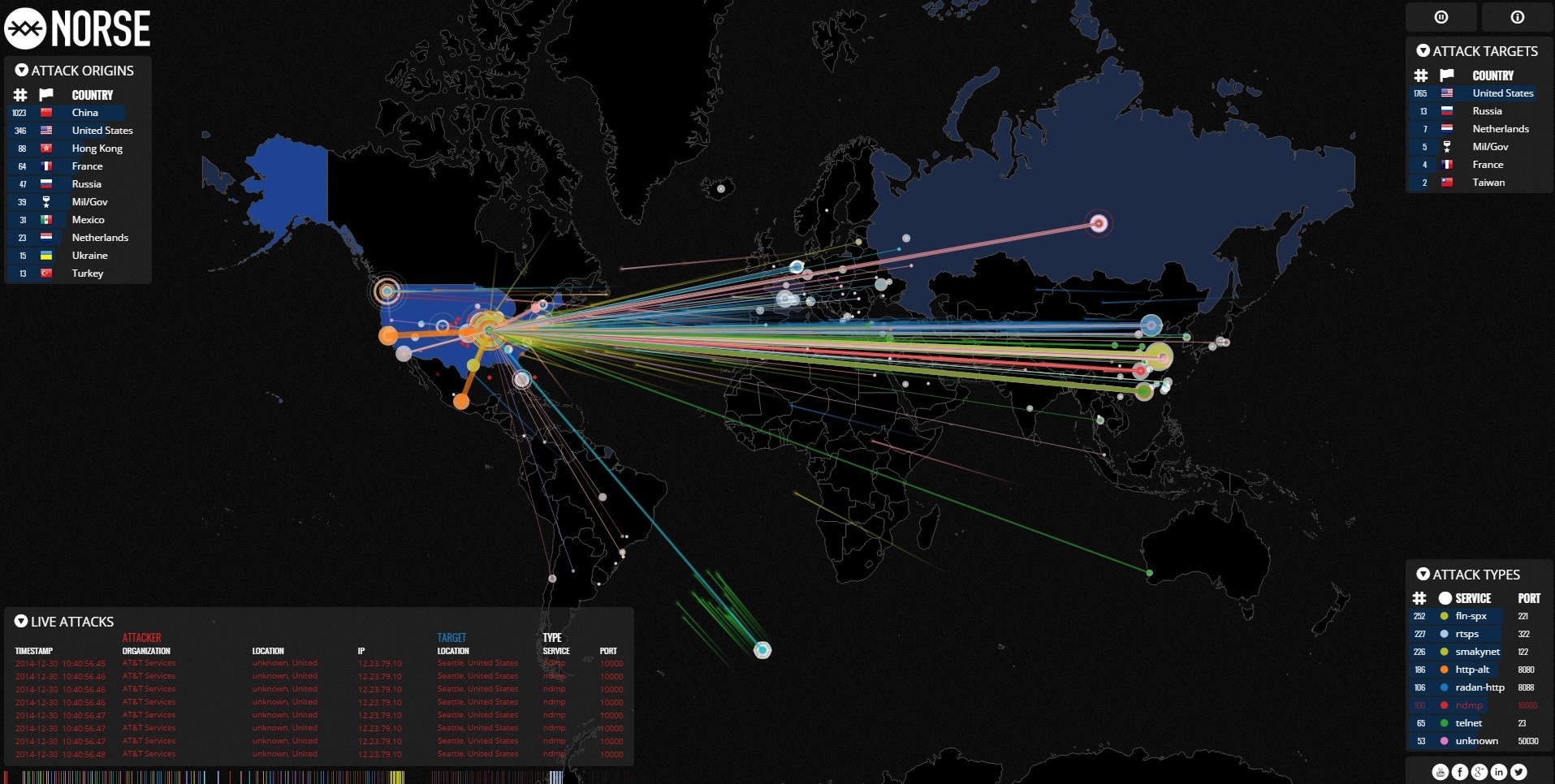
Cyber Attack Maps Are A Trove Of Information
Q Tbn And9gcrdu7zc7fqh8i8d5yw 4ubmzb3dos4kyv6ssyrjdlqnajz3zgy4 Usqp Cau
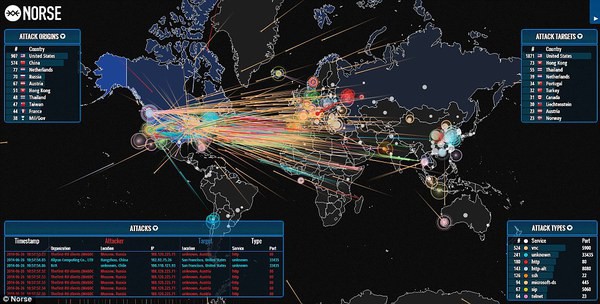
World Live Ddos Attack Maps Live Ddos Monitoring Blackmore Ops

What Is Your Actual Risk Of A Ddos Attack Aberdeen

7 Live Cyber Attack Maps
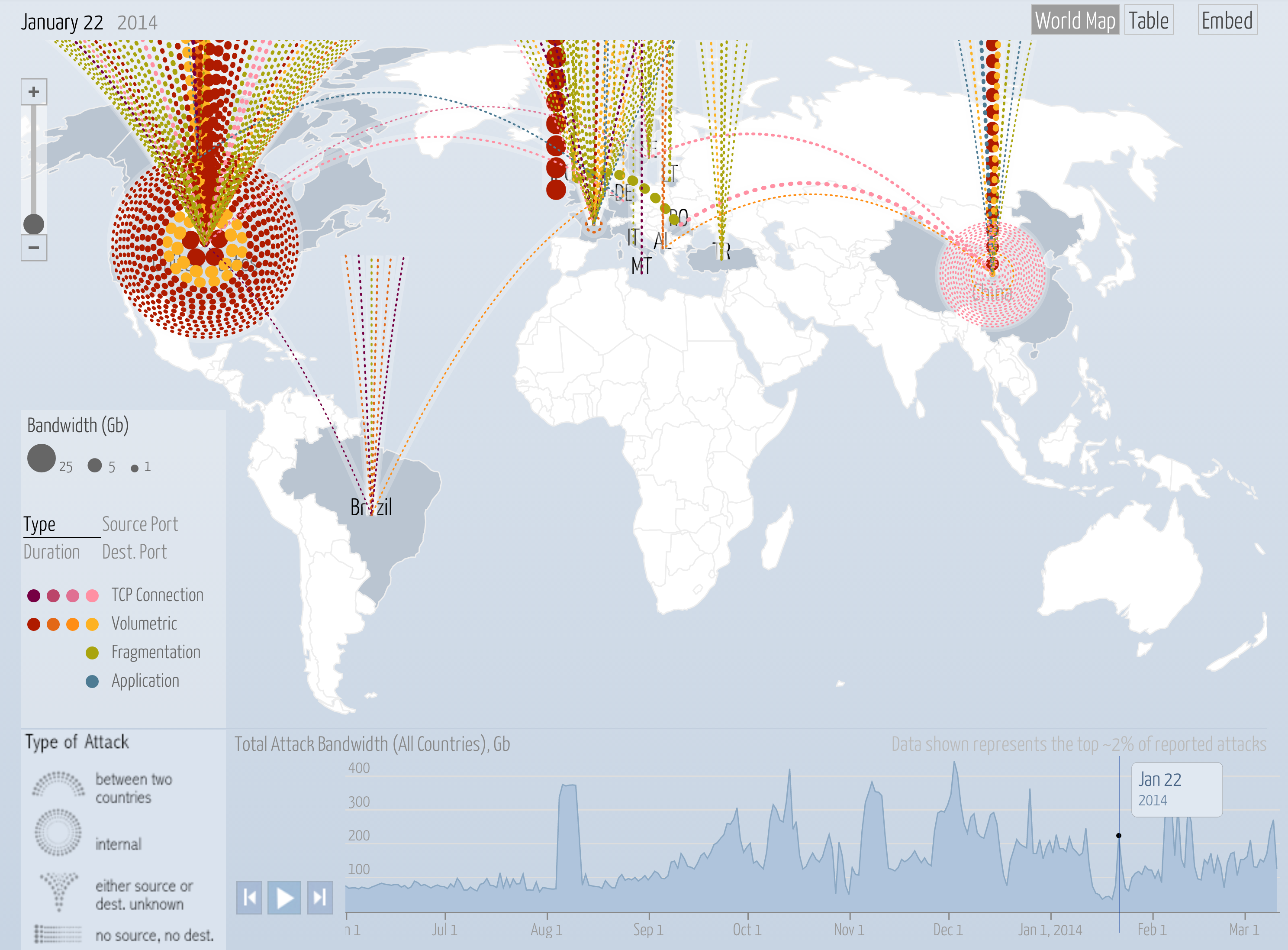
Digital Attack Map Google Ideas Design And Violence

What Is A Ddos Attack Cybernews

11 Interesting Ways To Watch Cyberattack In Real Time Worldwide

Google S Digital Attack Map Plots Live Ddos Attacks Around The World Graham Cluley
Www Cisco Com C Dam M En Us Network Intelligence Service Provider Digital Transformation Knowledge Network Webinars Pdfs 14 Msn Ckn Pdf Pdf
8 Top Cyber Attack Maps And How To Use Them Tahawultech Com
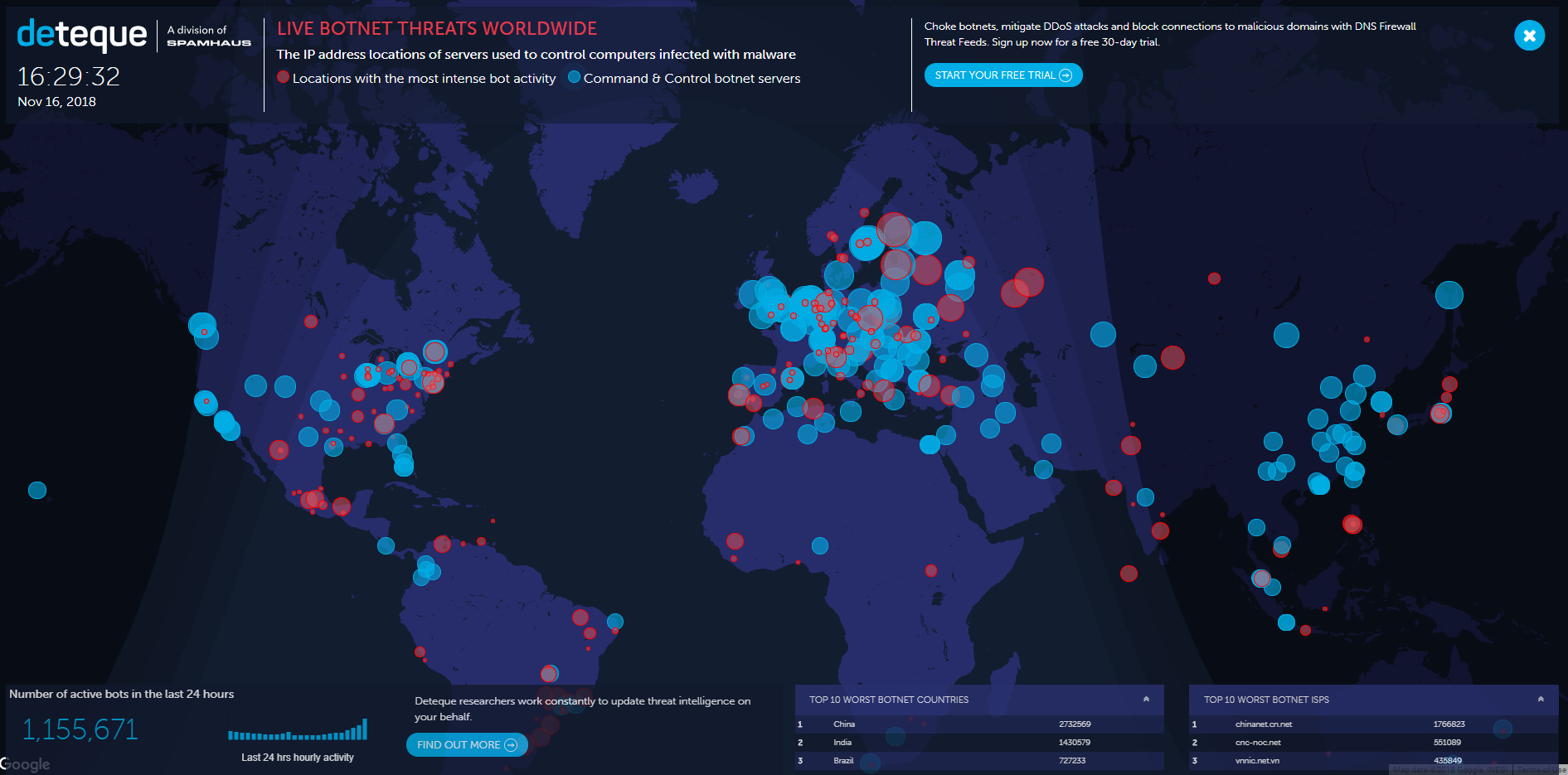
Top Ten Hacking Attack Maps And How They Can Help You
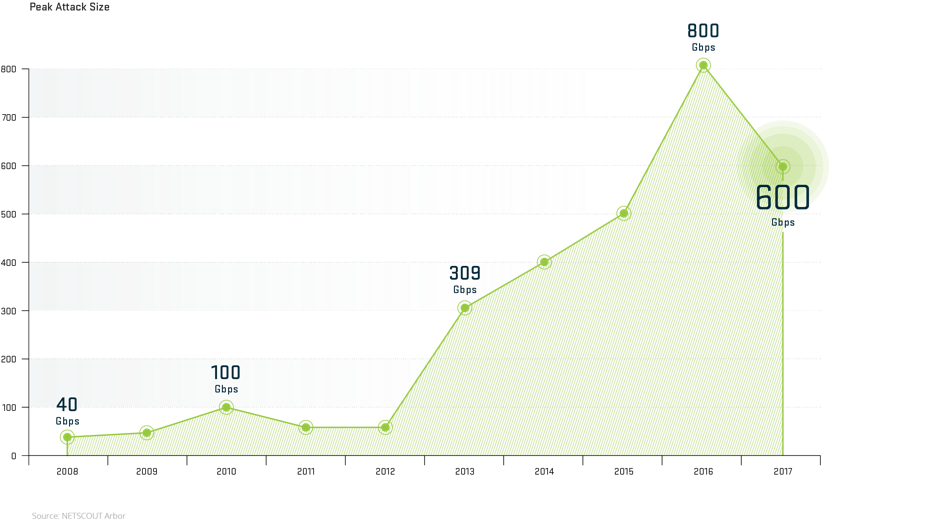
The Ddos Threat Landscape In 17 Apnic Blog

What Is A Ddos Attack Cybernews

Google And Arbor Networks Team Up On Ddos Digital Attack Map Infosecurity Magazine
What Is An Http Flood Ddos Attack Glossary Imperva
Q Tbn And9gcq142yriifpg2tyee7msk0hzibrxfgjawwxbs3gtdw Usqp Cau

Mapping Digital Attacks Around The World Geography Realm

Top 15 Live Cyber Attack Maps For Visualizing Digital Threat Incidents Norse Corp Com

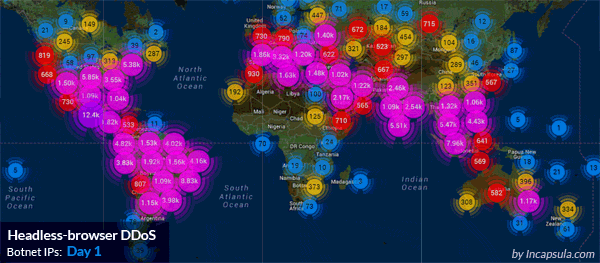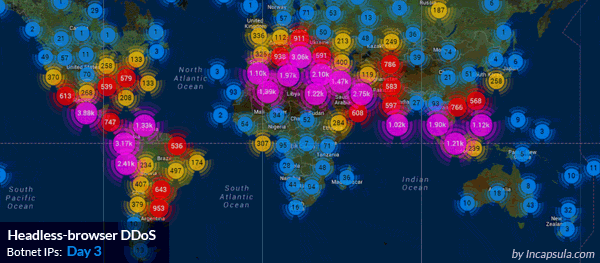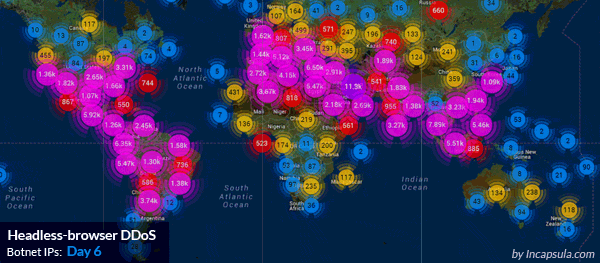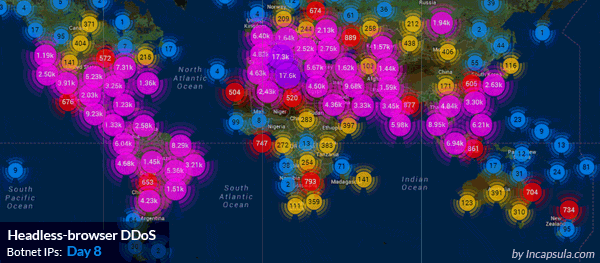
Ddos Attack Data From Arbor S Atlas System Source Arbor Networks Network Security Ddos Attack Cyber Security
Top 10 Cyber Attack Maps To See Digital Threats For

The Why Axis Google S Digital Attack Map

Top 15 Live Cyber Attack Maps For Visualizing Digital Threat Incidents Norse Corp Com
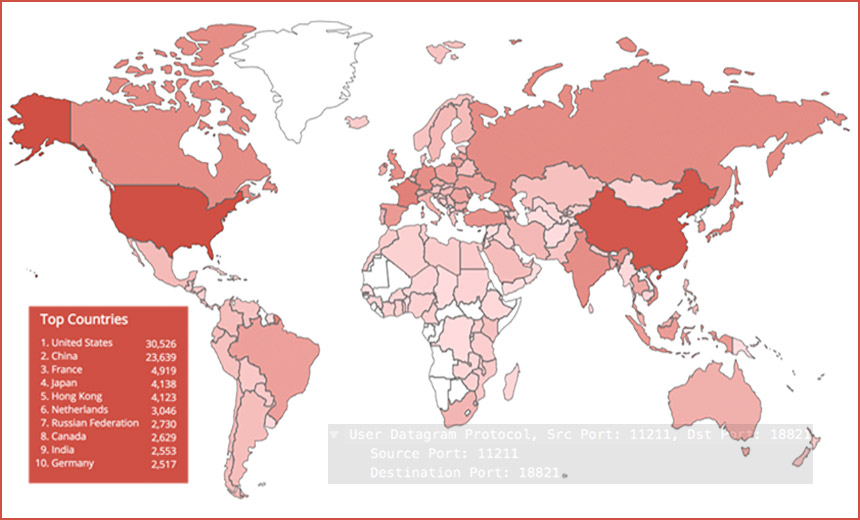
Memcached Ddos Attacks 95 000 Servers Vulnerable To Abuse

Google Collaborates With Arbor Networks On Ddos Visualisation Computer Business Review
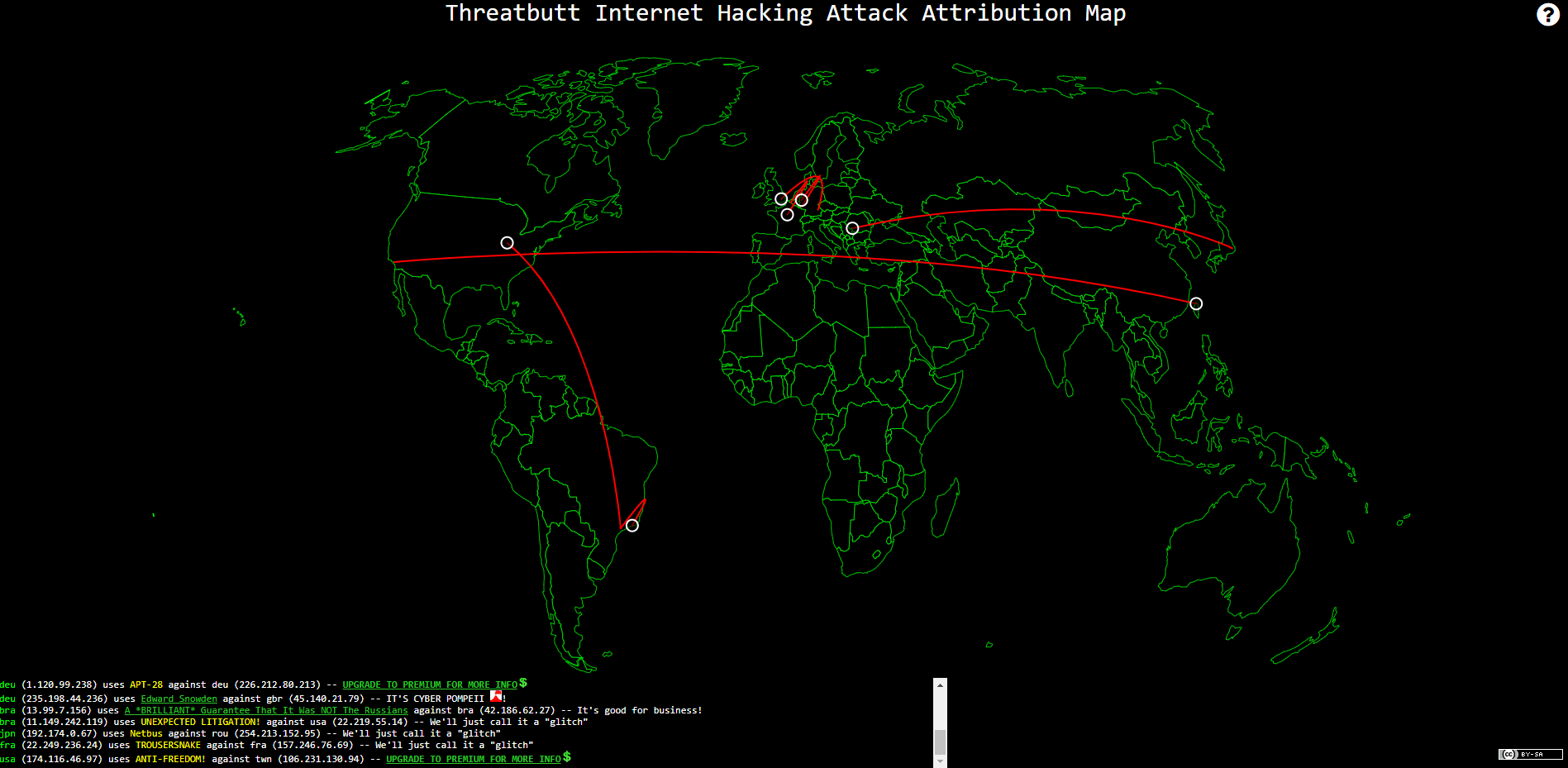
Top Ten Hacking Attack Maps And How They Can Help You

Arbor Networks Jigsaw Boost Digital Details In Ddos Attack Map
Anonymous Tweets Ddos Everyone Freaks Out Techbeacon
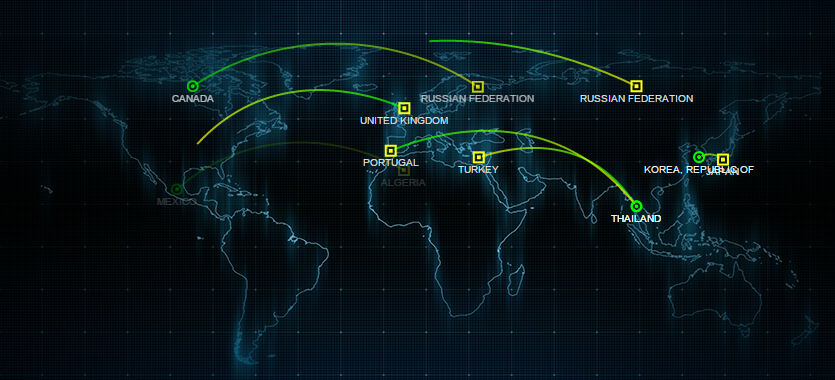
Who S Attacking Whom Realtime Attack Trackers Krebs On Security

Hybrid Ddos Prevention Solutions Appliances Netscout
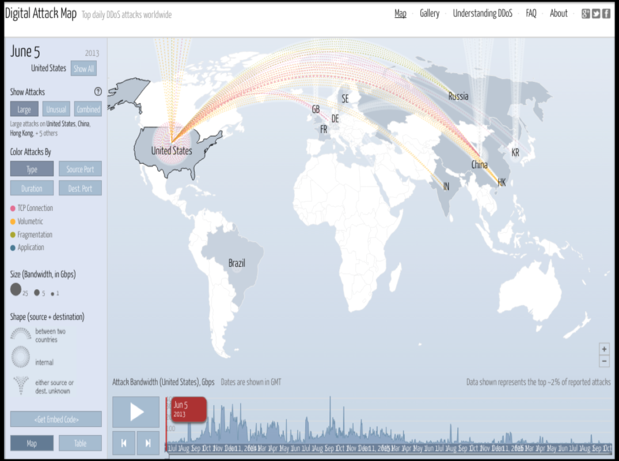
Ddos Attacks Using Iot Devices Follow The Manchurian Candidate Model Network World
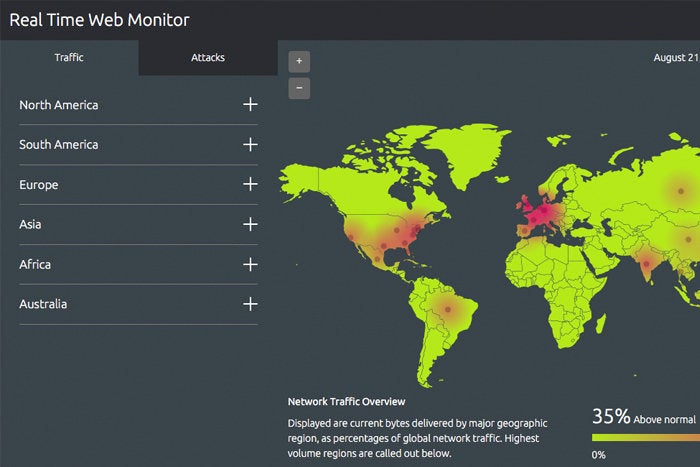
8 Top Cyber Attack Maps And How To Use Them Cso Online
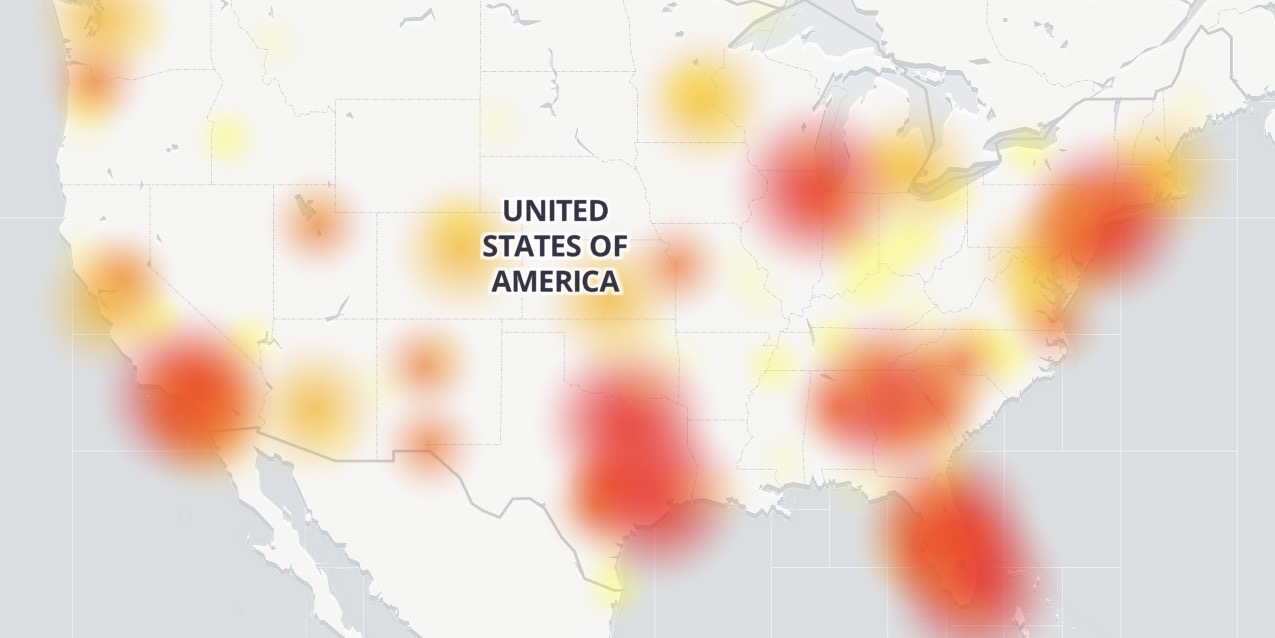
Outage Hits T Mobile Verizon At T And Sprint 9to5mac

Top 15 Live Cyber Attack Maps For Visualizing Digital Threat Incidents Norse Corp Com
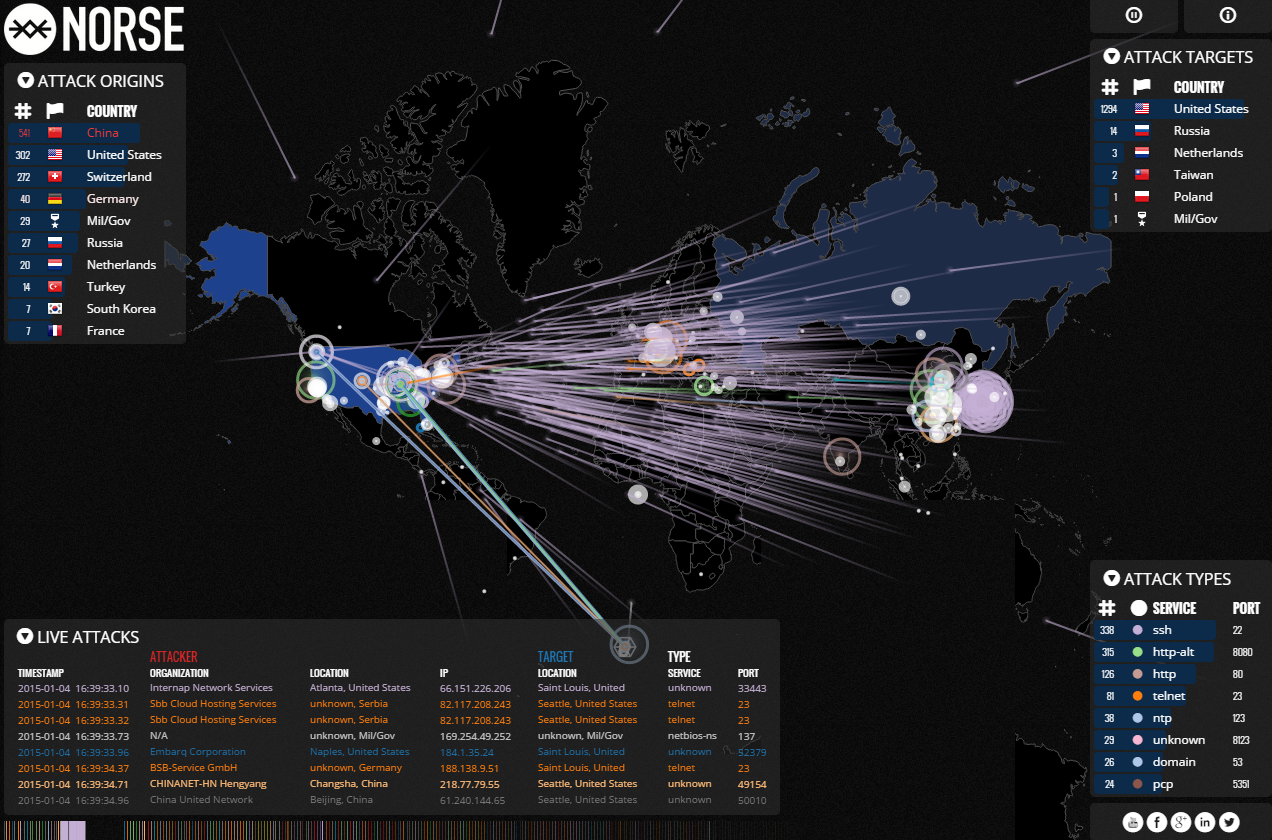
Who S Attacking Whom Realtime Attack Trackers Krebs On Security
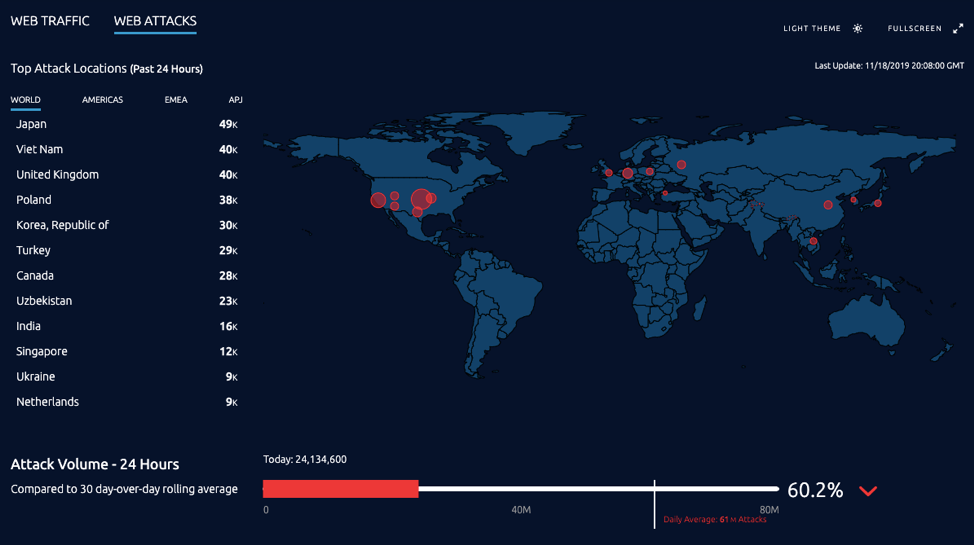
Top 8 Cyber Threat Maps To Track Cyber Attacks

Cyber Attacks And Data Breaches Visualised Leron Zinatullin S Blog

Top 15 Live Cyber Attack Maps For Visualizing Digital Threat Incidents Norse Corp Com

Techmeme World S Largest Ddos Attack Reached 400gbps Says Arbor Networks John E Dunn Techworld Com

Converge Network Digest Arbor Networks Largest Ddos Attack Hits 579 Gbps

It S Still A World Of Botnets And Cyber Attacks Hackmageddon

Who S Attacking Whom Realtime Attack Trackers Krebs On Security

Biggest Ddos Cyber Attack On U S Just Rampant Social Media Speculation Cpo Magazine

Cyber Attacks Geographical Imaginations

Top 15 Live Cyber Attack Maps For Visualizing Digital Threat Incidents Norse Corp Com
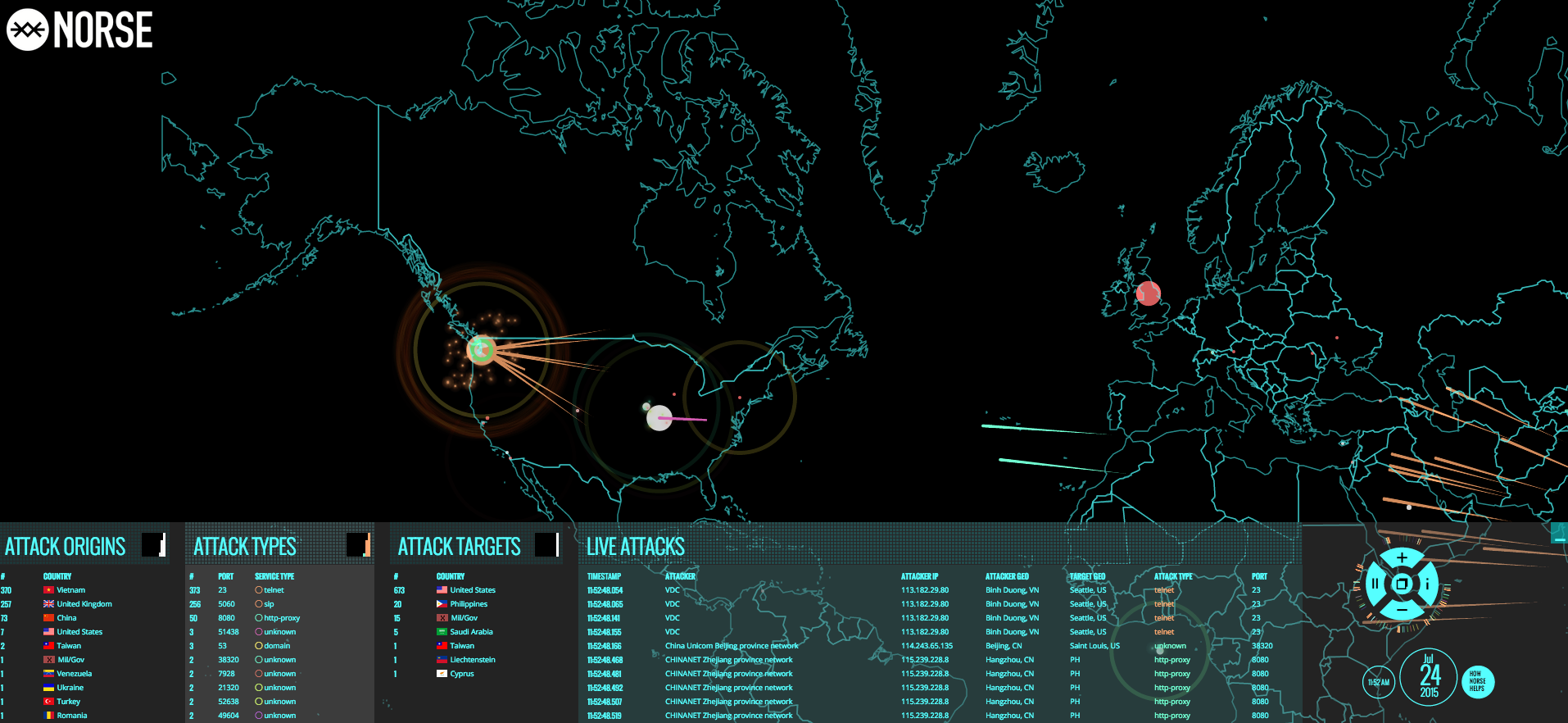
Watch International Cyber Attacks Take Place In Real Time Dogtown Media

Net Should Brace For More Giant Ddos Attacks
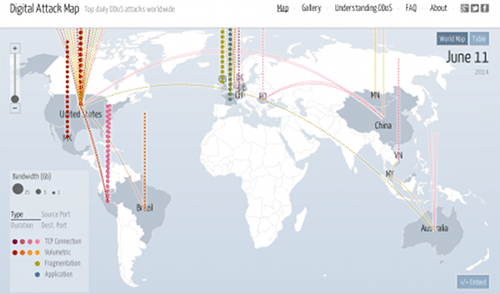
Ddos Attacks Hit Cloud Apps Evernote Feedly
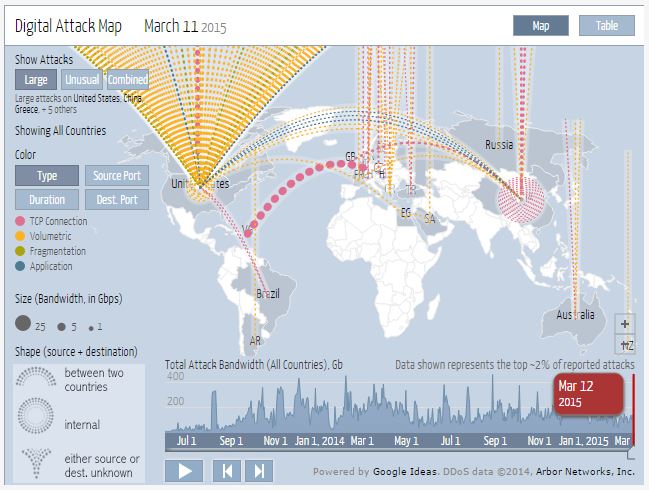
Cyberrescue Blog

8 Top Cyber Attack Maps And How To Use Them Cso Online

Worst Ddos Attack Of All Time Hits French Site Zdnet

Cyber Security In 15 Ssls Com Blog
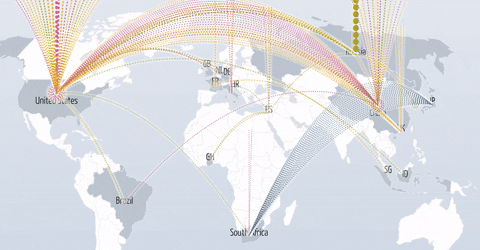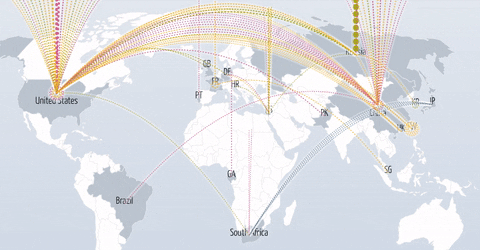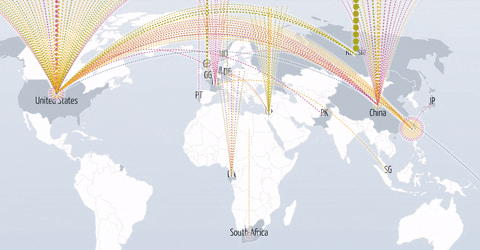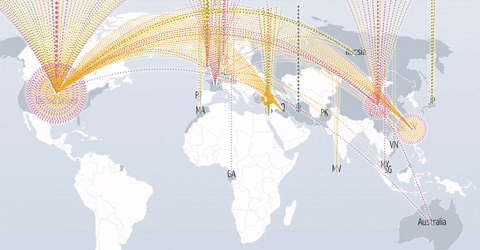
Arbor Networks Report Largest Ddos Attack Of 579gbps In The First Half Of 16
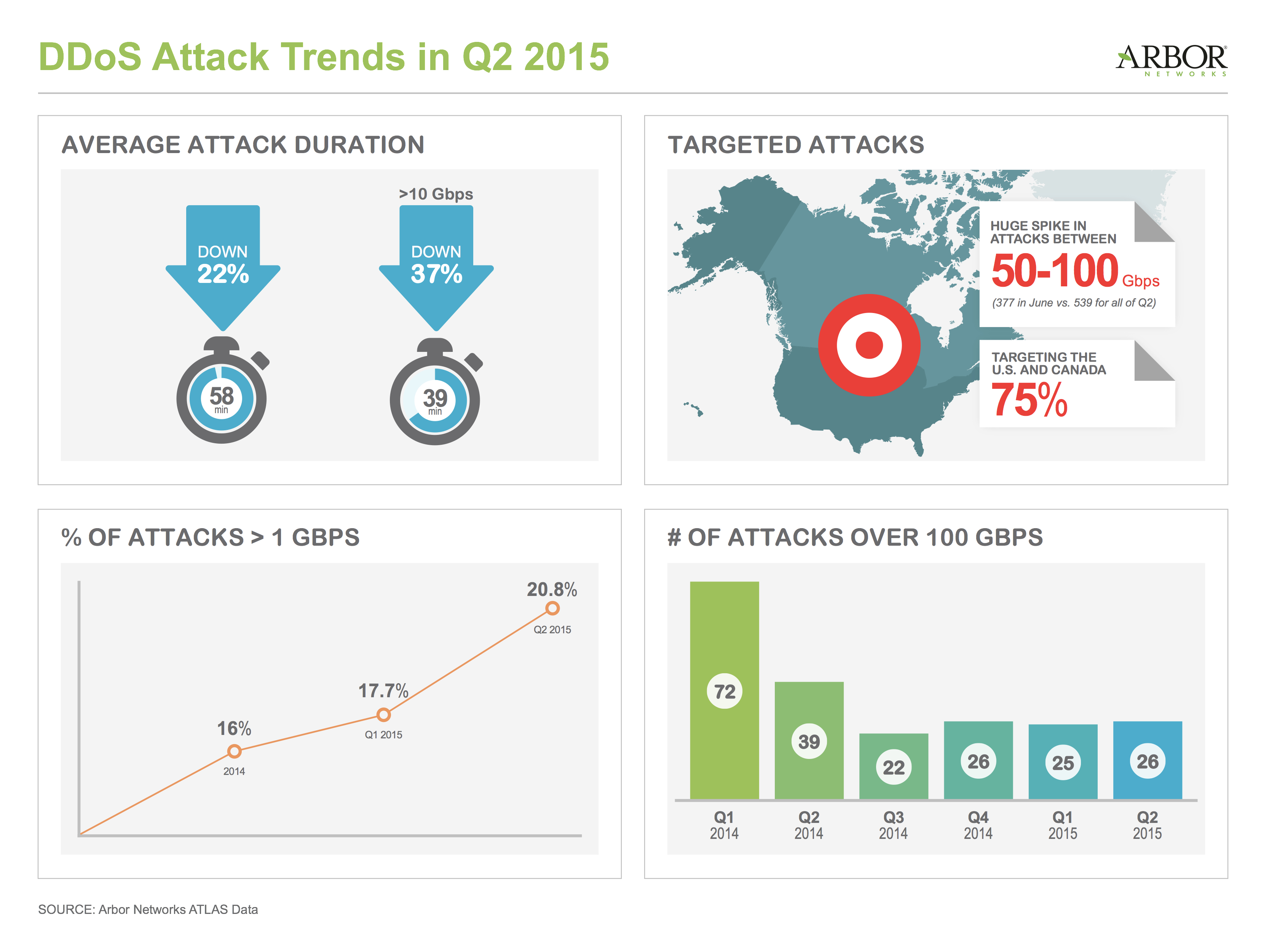
Arbor Networks Atlas Data Shows The Average Ddos Attack Size Increasing Business Wire

Top 15 Cyber Attack Maps For Visualizing Incidents Stephen Ajulu



