Cisco Ipsec
Have in mind also that sitetosite IPSEC VPN can also be configured on Cisco ASA firewalls as I have described here With IPSEC VPNs, businesses can connect together remote office LANs over the Internet with the strong encryption and security offered by the IPSEC protocol IPSEC is an IETF security standard It is basically a suit of several.

Cisco ipsec. IPSEC The Internet Protocol Security is a set of protocols that provides security features to IP;. IPsec Overview The ASA uses IPsec for LANtoLAN VPN connections and provides the option of using IPsec for clienttoLAN VPN connections In IPsec terminology, a peer is a remoteaccess client or another secure gateway For both connection types, the ASA supports only Cisco peers. The router has the HSEC and throughput licences and shows 1000Mbps for the throughput command In the diag.
Like authentication, encryption and confidentialityVPN can be implemented using IPSEC, L2TP Layer Two Tunneling Protocol is a tunneling protocol (VPN) used to transport in L2 traffic over an IP Network ( Internet). Cisco, GRE, IKEv2, IOS, IOSXE, IPSEC, VPNs IPSec VPNs on Cisco routers when both are behind NAT Date July 12, 19 Author J5 0 Comments IPSec VPNs or really any sitetosite VPN works best when at least one of the sides or better yet both have Public IP addresses. Provide Support for the Cisco VPN Client In most cases, IPSec VPN traffic does not pass through ISA Server 00 However, Cisco Concentrator 3300, with the latest firmware updates, uses "transparent tunneling" that uses User Datagram Protocol (UDP) ports 500, 4500, and to communicate securely between VPN clients and concentrators.
Fullcrypto Cisco IPsec VPN gateway with software client Learn how to build an IPsec VPN gateway with a Cisco router and software client using a fullcrypto traffic model in which all traffic is either encrypted or processed by an internal firewall. In the tunnel mode, IPSec protects peertopeer communication between two end nodes by establishing a virtual tunnel between those two endpoints On the Cisco CGOS router, this virtual tunnel is built between itself (source) and the destination router such as the Cisco ASR 1000 Series Aggregation Services Routers (Cisco ASR), which serve as a headend router. Troubleshooting Cisco IPSec Site to Site VPN – “QM Rejected” CISCO ASA VPN Tips and Tricks By Jon Related Post VPN Create VPN Tunnel Between CheckPoint FIrewall and WatchGuard FireBox Firewall Dec 30, Jon VPN Install Mac OSX AnyConnect Package on Cisco Router and on Mac Machine.
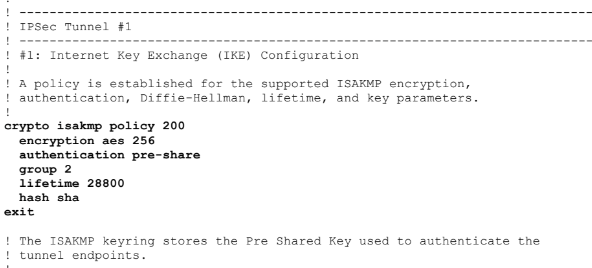
A vulnerability in the hardware crypto driver of Cisco IOS XE Software for Cisco 4300 Series Integrated Services Routers and Cisco Catalyst 9800L Wireless Controllers could allow an unauthenticated, remote attacker to disconnect legitimate IPsec VPN sessions to an affected device The vulnerability is due to insufficient verification of authenticity of received Encapsulating Security Payload. Implementing IPSEC In this example, we will set up IPSEC to encrypt communications between two windows machines The first machine, a windows 12 server will act as the VPN server The second machine, a Windows 10 client, will act as the VPN client A LT2P IPSEC VPN can exchange either a preshared key or a certificate. Crypto isakmp policy 1 encr 3des hash md5 authentication preshare group 2 !.
If the following example does not help, there are several examples that turn up in a Google search for “cisco ios nonat ipsec” ip nat inside source route map NONAT interface FastEthernet0 / 0 overload access list 110 deny ip 50 00 0255 110 00 0255 access list 110 permit ip 50 00 0255 any. This article seems to be the reference for IPsec SitetoSite (routebased) VPN between FortiGate and Cisco Router This helped me greatly to get a VPN tunnel up between my 2 devices (Fortigate 60C and Cisco 1W) I can ping from the Fortigate LAN to the Cisco LAN however I cannot ping from the Cisco to the Fortigate. Cisco Meraki uses IPSec for Sitetosite and Client VPN IPSec is a framework for securing the IP layer IPSec is a framework for securing the IP layer In this suite, modes and protocols are combined to tailor fit the security methods to the intended use.
CiscoASA# more systemrunningconfig b tunnelgroup tunnelgroup type ipsecl2l tunnelgroup ipsecattributes ikev1 presharedkey cisco1234@ Below commands is a filters to see the specific peer tunnelgorup of vpn tunnel. The five steps are summarized as follows Step 1 Interesting traffic initiates the IPSec process —Traffic is deemed interesting when the IPSec security policy configured in the IPSec peers starts the IKE process Step 2 IKE phase one —IKE authenticates IPSec peers and negotiates IKE SAs during this phase, setting up a secure channel for negotiating IPSec SAs in phase two. Crypto ipsec transformset vpn esp3des espmd5hmac mode transport !.
Luckily, a workaround exists to allow the Cisco VPN Client application to function on Windows 10 and other 64bit versions of Windows until your organization is ready to migrate to a newer VPN. In most cases, IPSec VPN traffic does not pass through ISA Server 00 However, Cisco Concentrator 3300, with the latest firmware updates, uses "transparent tunneling" that uses User Datagram Protocol (UDP) ports 500, 4500, and to communicate securely between VPN clients and concentrators. IPsec uses cryptographic security services to protect communications over Internet Protocol (IP) networks It supports networklevel peer authentication, dataorigin authentication, data integrity, data confidentiality (encryption), and replay protection The initial IPv4 suite was developed with few security provisions.
Like authentication, encryption and confidentialityVPN can be implemented using IPSEC, L2TP Layer Two Tunneling Protocol is a tunneling protocol (VPN) used to transport in L2 traffic over an IP Network ( Internet). Cisco is committed to providing the best cryptographic standards to our customers NGE still includes the best standards that one can implement today to meet the security and scalability requirements for network security in the years to come or to interoperate with the cryptography that will be deployed in that time frame In IPsec, a 24. If the following example does not help, there are several examples that turn up in a Google search for “cisco ios nonat ipsec” ip nat inside source route map NONAT interface FastEthernet0 / 0 overload access list 110 deny ip 50 00 0255 110 00 0255 access list 110 permit ip 50 00 0255 any.
Cisco IOS software implements and processes IPSec in a predictable and reliable fashion A summary of how IPSec works in Cisco IOS software is shown in Figure 4 The process shown in the figure assumes that you have already created your own public and private keys, and that at least one access list exists Figure 4 IKE and IPSec flowchart. If you update your Ciscocom account with your WebEx/Spark email address, you can link your accounts in the future (which enables you to access secure Cisco, WebEx, and Spark resources using your WebEx/Spark login). During the IPSec workshops, the NRL's standards and Cisco and TIS' software are standardized as the public references, published as RFC15 through RFC17 Security architecture The IPsec is an open standard as a part of the IPv4 suite IPsec uses the following protocols to perform various functions.
The Cisco IPSec VPN has two levels of protection as far as credentials concern The remote client must have valid group authentication credential, followed by valid user credential The group credentials are entered once and stored in the VPN connection entry, however the user credentials are not stored and requested every time a connection is. IPSEC The Internet Protocol Security is a set of protocols that provides security features to IP;. IPSec and Crypto setup in Cisco, also here trasnport mode of IPSec should be setup !.
We would like to inform our readers that we have updated our download section to include Cisco's popular Windows VPN Client The Cisco VPN Client is available for both 32bit and 64bit Windows operating systems To download the latest Cisco VPN Client, simply visit our download section and look for our new Cisco Tools category!. Connecting to Cisco PIX/ASA Devices with IPsec¶ Using IPsec to create a VPN tunnel between pfSense® router and a Cisco PIX should work OK As always with IPsec, be sure that the Phase 1 and Phase 2 settings match up on both sides. Having been discontinued back in 11, it shouldn’t come as a shock that the Cisco VPN client isn’t supported by Windows 10In fact, you would be lucky to get it working with Windows 81 since.
IPsec provides security for transmission of sensitive information over unprotected networks such as the Internet IPsec services are similar to those provided by Cisco Encryption Technology (CET), a proprietary security solution introduced in Cisco IOS Software Release 112. Hello guys I configured GRE IPsec but I get the following message oct 3 %CRYPTO6IKMP_MODE_FAILURE Processing of Informational mode failed with peer at access is mandatory for crypto map when i created access list for permitting gre traffic between R1 and R3 my OSPF. Introduction to Cisco IPsec Technology • Data origin authentication • Connectionless data integrity authentication • Data content confidentiality • Antireplay protection • Limited traffic flow confidentiality IPsec protects IP datagrams by defining a method of specifying the traffic to • Secure.
IPSec acts at the network layer, protecting and authenticating IP packets between participating IPSec devices (peers), such as PIX Firewalls, Cisco routers, Cisco VPN 3000 Concentrators, Cisco VPN Clients, and other IPSeccompliant products IPSec is not bound to any specific encryption or authentication algorithms, keying technology, or security algorithms. Crypto ipsec profile ProtectGreCPB set securityassociation lifetime seconds set transformset CpbTS !!!!!. @Matt, Both are cisco routers, I have seen that but seem like tunnel on the other end went down when adding IPSEC protected ## Router1 (NEW ROUTER) crypto ipsec transformset TSET esp3des espshahmac crypto ipsec profile VTI set transformset TSET Interface tun 1 tunnel protection ipsec profile VTI Tunnel1 is up, line protocol is down.
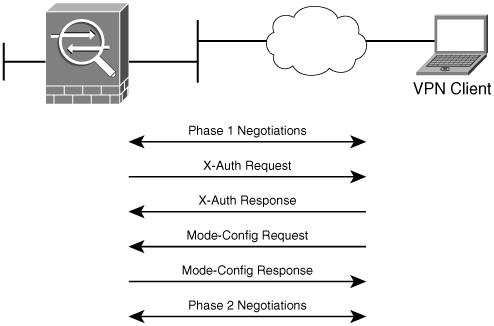
With the Cisco Secure VPN Client, you use menu windows to select connections to be secured by IPSec When interesting traffic is generated or transits the IPSec client, the client initiates the next step in the process, negotiating an IKE phase 1 exchange Step 1 is shown in Figure 4 Figure 4 Defining "interesting traffic". IPsec is pretty complex and there are a lot of different ways to implement it In this lesson I will start with an overview and then we will take a closer look at each of the components Before we can protect any IP packets, we need two IPsec peers that build the IPsec tunnel. Interface Tunnel1 ip address no ip redirects ip mtu 1400 ip nhrp map multicast dynamic ip nhrp map.
IPsec acts at the network layer, protecting and authenticating IP packets between participating IPsec devices (“peers”), such as Cisco routers Starting with Cisco IOS XE Release 318S, IPsec tunnel is supported only on the Cisco ASR912SZIM routers with payload encryption (PE) images IPsec requires an IPsec license to function. This article shows how to configure, setup and verify sitetosite Crypto IPSec VPN tunnel between Cisco routers Understand IPSec VPNs, including ISAKMP Phase, parameters, Transform sets, data encryption, crypto IPSec map, check VPN Tunnel crypto status and much more Full set of commands and diagrams included. Cisco ASA IPSec VPN Overview The Cisco IPSec configuration protects IKE encrypted connections that use Cisco's desktop VPN client First Steps Before moving on to the deployment steps, it's a good idea to familiarize yourself with Duo administration Install the Duo Authentication Proxy The Duo.
Cisco ASA IPsec VPN Troubleshooting Command In this post, we are providing insight on Cisco ASA Firewall command which would help to troubleshoot IPsec vpn issue and how to gather relevant details about IPsec tunnel This document describes common Cisco ASA commands used to troubleshoot IPsec issueThis document assumes you have configured IPsec tunnel on ASA. Crypto ipsec transformset CpbTS esp3des espmd5hmac mode transport!. IPSEC AntiReplay is a feature available to the ESP data plane that sequentially marks packets as they are encapsulated with a number Each new packet is encapsulated/encrypted and gets 1 added to its sequence number (in the ESP header) and is sent on.
For Cisco ASA, i wrote an article of IPSEC VPN with presharedkey authentication IPSECwithCiscoASApdf This does also explain the possibilities for IPSEC VPN with ASA and one end with dynamic ip address Juergen, Correct, ASA doesn't support DMVPN, hence why I mentioned using different hardware As for GRE over IPSEC, you do have the. With the Cisco Secure VPN Client, you use menu windows to select connections to be secured by IPSec When interesting traffic is generated or transits the IPSec client, the client initiates the next step in the process, negotiating an IKE phase one exchange. Cisco IOS ® devices that are configured for Internet Key Exchange (IKE) protocol and certificate based authentication are vulnerable to a resource exhaustion attack Successful exploitation of this vulnerability may result in the allocation of all available Phase 1 security associations (SA) and prevent the establishment of new IPsec sessions.
Multiple Cisco products contain vulnerabilities in the processing of IPSec IKE (Internet Key Exchange) messages These vulnerabilities were identified by the University of Oulu Secure Programming Group (OUSPG) "PROTOS" Test Suite for IPSec and can be repeatedly exploited to produce a denial of service. An IPSec transform in Cisco IOS specifies either an AH or an ESP protocol and its corresponding algorithms and mode (transport or tunnel) The Cisco Secure VPN Client uses the concept of security policies to specify the same parameters Figure 2 contains an actual example of SA parameters for two IPSec peers R1 and R2 Remember that each IPSec. Cisco IOS routers can be used to setup IPSec VPN tunnel between two sites In this post, I will show steps to Configure IPSec VPN With Dynamic IP in Cisco IOS RouterThis VPN configuration is different from Site to Site IPSec VPN with static IP address on both ends Configure IPSec VPN With Dynamic IP in Cisco IOS Router.
How to configure an L2TP/IPSec connection by using Preshared Key Authentication. Crypto isakmp key ipsec address 0000 0000 !. Hi We have a 4431 running as a VPN head end and have roughly 700x users connecting concurrently I'm having difficulty understanding what the IPSEC throughput should be and how to measure it?.
Rightclick the IPSec policy that you just created, and then click Assign Setp 4 Connect VPN Now you should be able to connect to Cisco ASA VPN Other Resources L2TP Over IPsec Between Windows 00/XP PC and PIX/ASA 72 Using Preshared Key Configuration Example;. The price of Cisco ASA firewall appliance is very expensive comparing to Cisco router Due to budget limitation, some companies would prefer to use Cisco router as a VPN gateway instead of Cisco ASA firewall appliance In this article will demonstrate how to configure sitetosite IPSec VPN between two Cisco routers 2 Prerequisites. IPSec VPN is a security feature that allow you to create secure communication link (also called VPN Tunnel) between two different networks located at different sites Cisco IOS routers can be used to setup VPN tunnel between two sites Traffic like data, voice, video, etc can be securely transmitted through the VPN tunnel.
IPsec feature set 56i—Indicates single Data Encryption Standard (DES) feature (on Cisco IOS Software Release 112 and later) k2—Indicates triple DES feature (on Cisco IOS Software Release 1 and later) Triple DES is available on the Cisco 2600 series and later. Cisco IOS software checks to see if IPSec SAs have been established Step 3 If the SA has already been established by manual configuration using the crypto ipsec transformset and crypto map commands or has been previously set up by IKE, the packet is encrypted based on the policy specified in the crypto map and is transmitted out of the interface. IPSec IPSec acts at the network layer, protecting and authenticating IP packets between participating IPSec devices (peers), such as PIX Firewalls, Cisco routers, Cisco VPN 3000 Concentrators, Cisco VPN Clients, and other IPSeccompliant products.

How To Configure Site To Site Ipsec Vpn Tunnel In Cisco Ios Router Tech Support Says

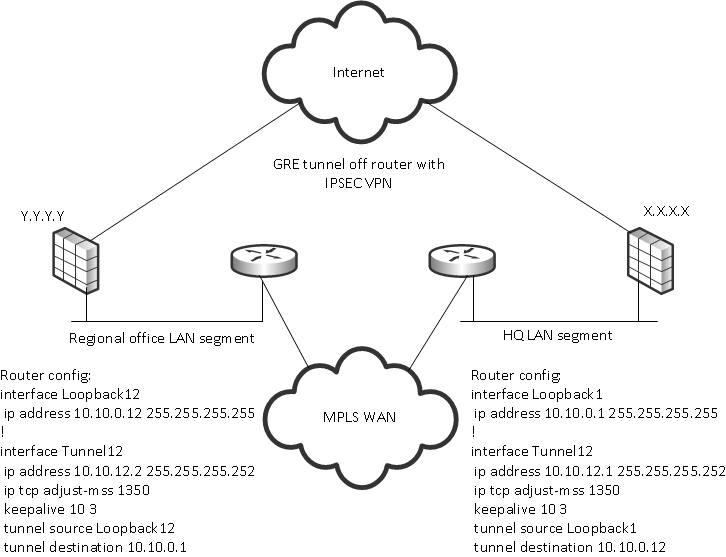
Encrypted Gre Tunnel With Ipsec
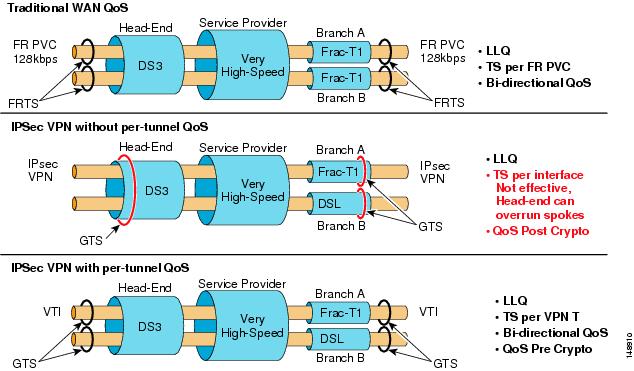
Ipsec Vpn Wan Design Overview Cisco
Cisco Ipsec のギャラリー

Ipsec Direct Encapsulation Vpn Design Guide Cisco
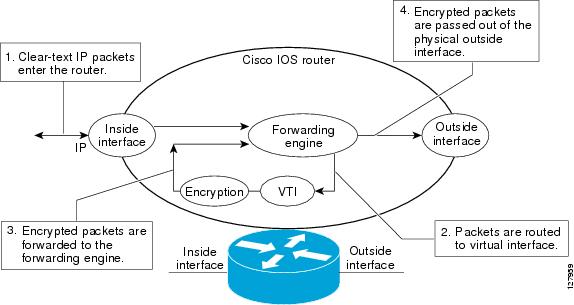
Ipsec Virtual Tunnel Interface Cisco Systems
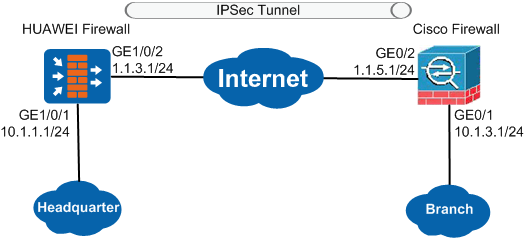
Establishing Ipsec Tunnels In Isakmp Mode Between Huawei Firewalls And Cisco Firewalls Huawei Usg Series Firewalls Interoperability Configuration Guide For Vpn Huawei
Configuring A Virtual Tunnel Interface With Ip Security Ipsec Negotiation Ike Protocols Cisco Systems

Ipsec Direct Encapsulation Vpn Design Guide Cisco

Linux Ipsec Site To Site Vpn Aws Vpc Cisco Router Lazy Geek
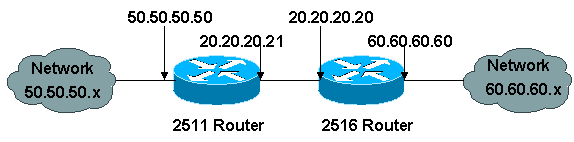
Configuring And Troubleshooting Cisco Network Layer Encryption Ipsec And Isakmp Part 2 Cisco
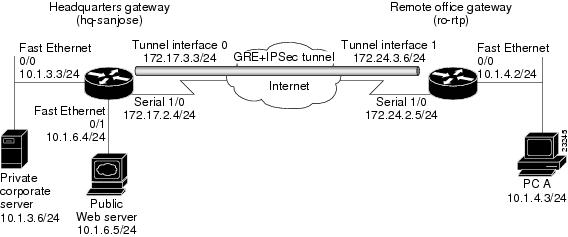
Cisco Ios Vpn Configuration Guide Site To Site And Extranet Vpn Business Scenarios Cisco 70 Series Routers Cisco

Gre Over Ipsec Configuration And Explanation Ccie Notes Networkology

Basic Ipsec Vpn Site To Site On Cisco Router Step By Step 01 Youtube

Cisco Ikev1 Site To Site Ipsec Configuration On Ios Routers 2 Using Two Different Ca Certificates Cyber Security Memo

Ha Site To Site Ipsec Vpn Using Hsrp Tech Space Kh

Implementation Of Ipsec Vpn On Cisco Routers And Configuring It On Is
Cisco Asa Vpn Ipsec With Bgp Tunnel
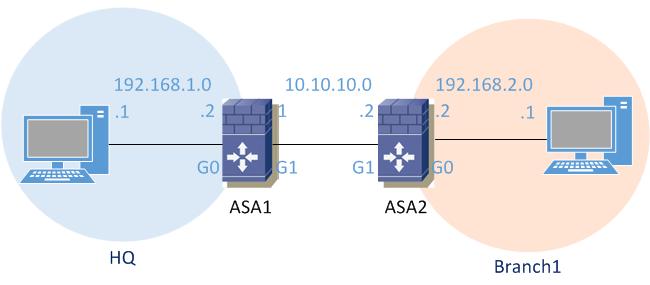
How To Configure Site To Site Ipsec Vpn On Cisco Asa Using Ikev2 Router Switch Blog

Cisco Ikev2 Site To Site Gre Over Ipsec Youtube

Ipsec Site To Site Vpn Between Mikrotik And Cisco Router

Configure Ipsec Vpn With Dynamic Ip In Cisco Ios Router
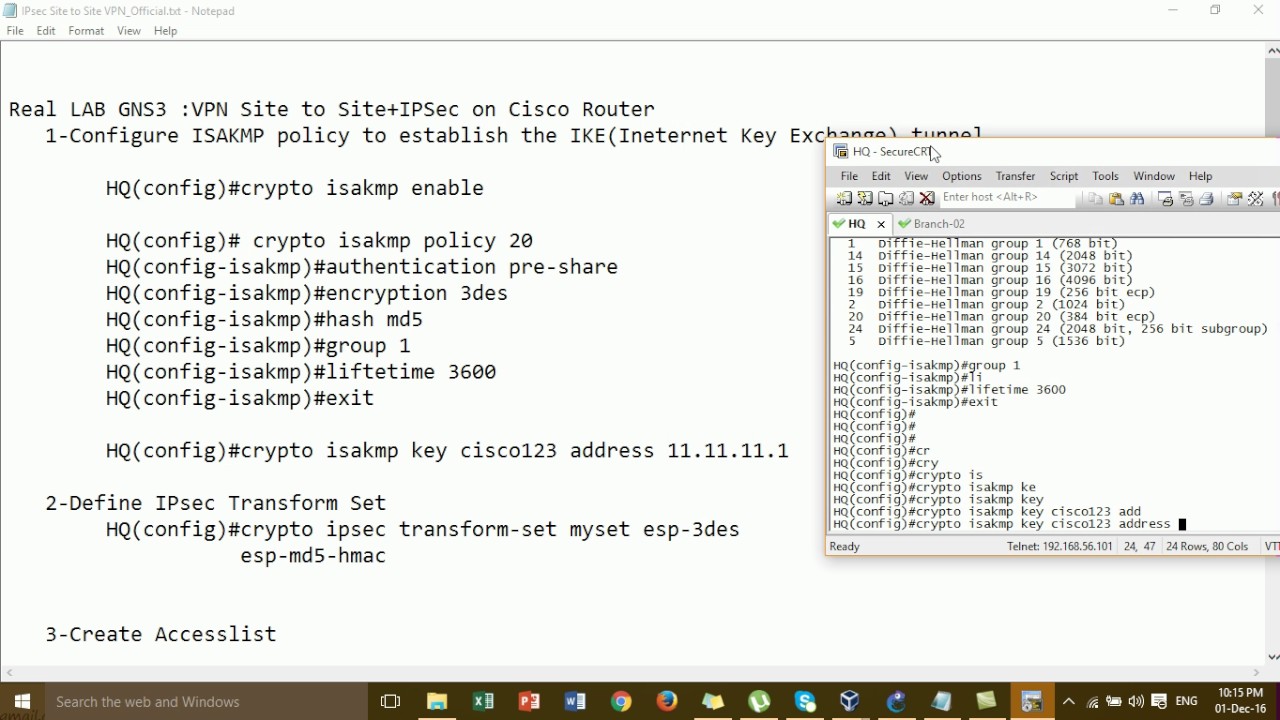
Lab Gns3 Configure Vpn Site To Site Ipsec On Cisco Router Step By Step Youtube
Q Tbn And9gcsopgxfektc Efrucghrk 7xlv1aphd49rrbojjs Xtpjn0mq2m Usqp Cau
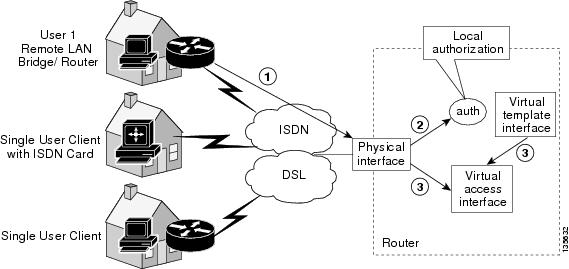
Security For Vpns With Ipsec Configuration Guide Cisco Ios Xe Release 3s Ipsec Virtual Tunnel Interfaces Support Cisco

Ipsec Direct Encapsulation Vpn Design Guide Cisco
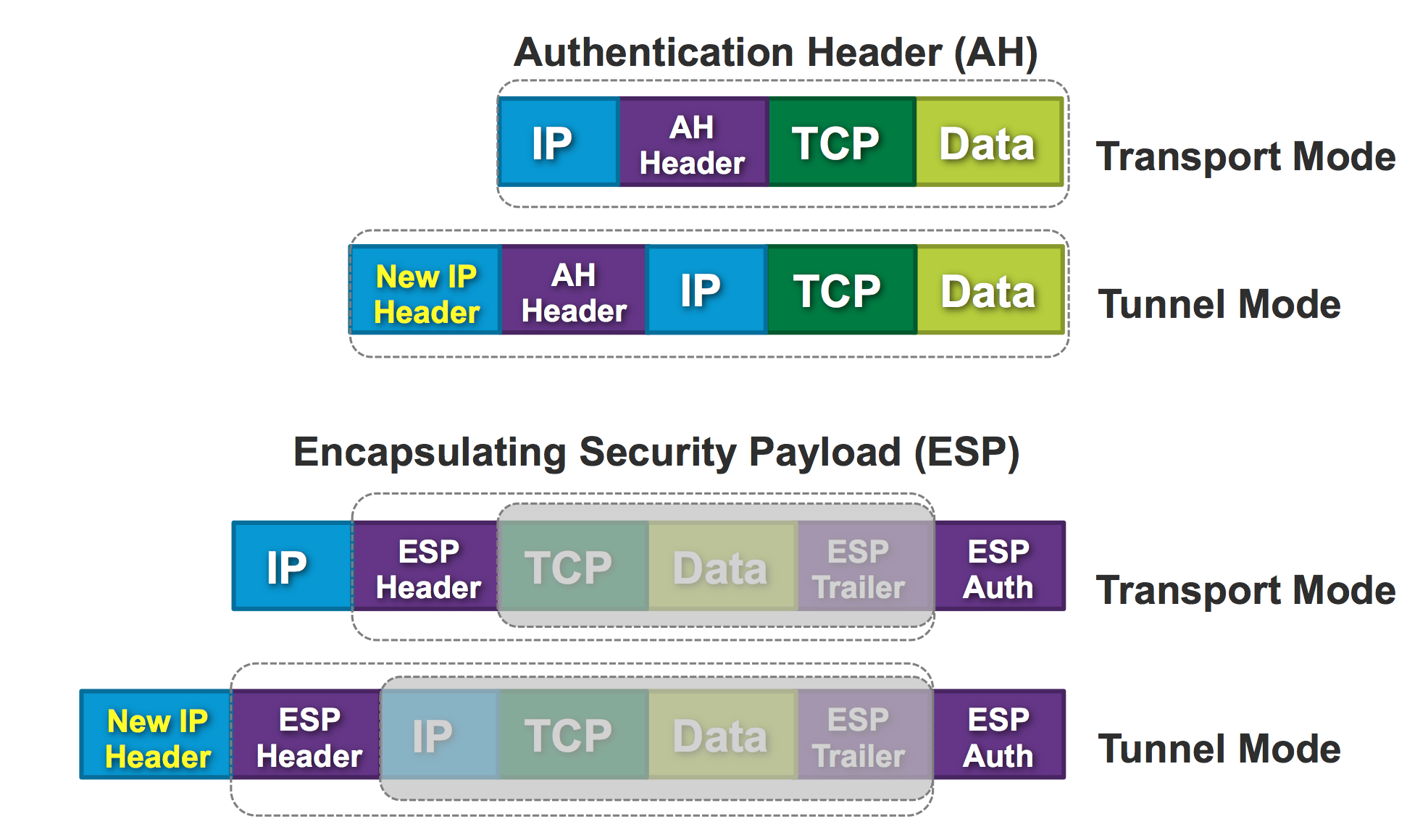
Crypto Map Based Ipsec Vpn Fundamentals Negotiation And Configuration Cisco Community

Learn How To Configure Ipsec Site To Site Vpn On Cisco Router Using Cisco Packet Tracer Learn Linux Ccna Ceh Ccnp Ipv6 Cyber Security Python

Ipsec Vpn Between Srx And Cisco Rtodto Net
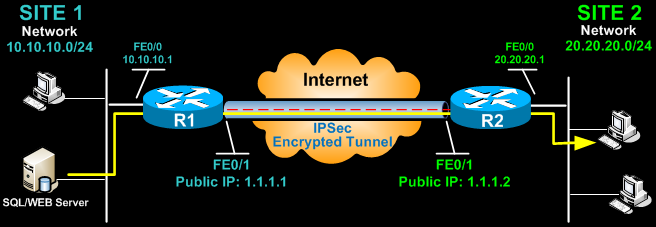
Configuring Site To Site Ipsec Vpn Tunnel Between Cisco Routers

Mikrotik Router To Cisco Pix Firewall Ipsec Mikrotik Wiki
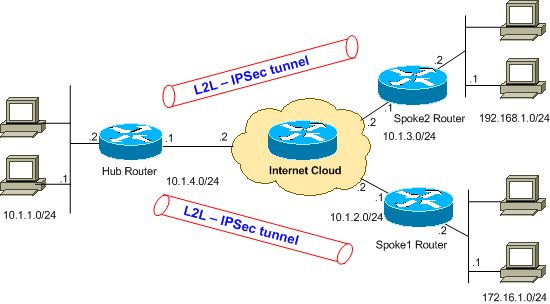
Configuring Ipsec Router To Router Hub And Spoke With Communication Between The Spokes Cisco
It Blogtorials Configuring Ipsec Vpn Between Linux And Cisco
Ipsec Tunnel Between Cisco Ios Router And Aws Vpc Grandmetric

Configuring Ipsec Between Softlayer Vyatta And Cisco Router Insidepacket
Cisco Ipsec Remote Access Vpn Solution Remote Access Vpn
Ipsec Vpn Connection To Cisco Asa With Loopback Interfaces On Internal Gre Routers Discussions Xg Firewall Sophos Community

Troubleshooting Cisco Ipsec Site To Site Vpn Qm Rejected Cyber Security Memo

Site To Site Ipsec Vpn Between Cisco Asa And Pfsense
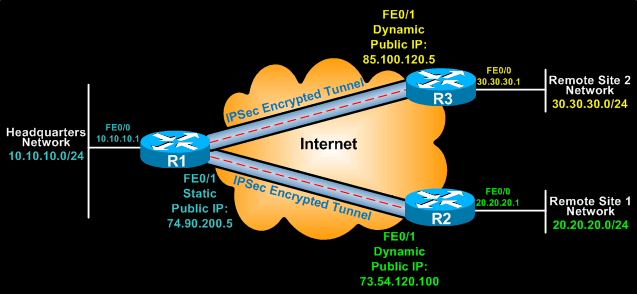
Configuring Cisco Site To Site Ipsec Vpn With Dynamic Ip Endpoint Cisco Routers
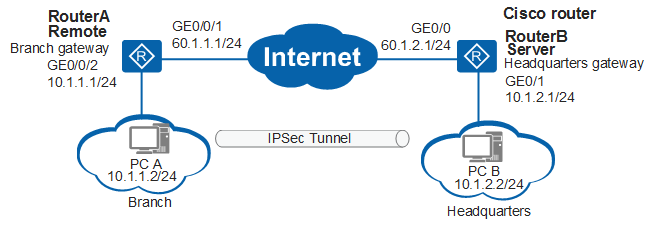
Example For Configuring The Headquarters Cisco Router To Manage Branches Using Efficient Vpn And Establishing Ipsec Tunnels Ar100 Ar1 Ar150 Ar160 Ar0 Ar10 Ar20 Ar30 And Ar3600 Cli Based Typical Configuration Examples

Cisco Ipsec Vpn Ccie Or Null
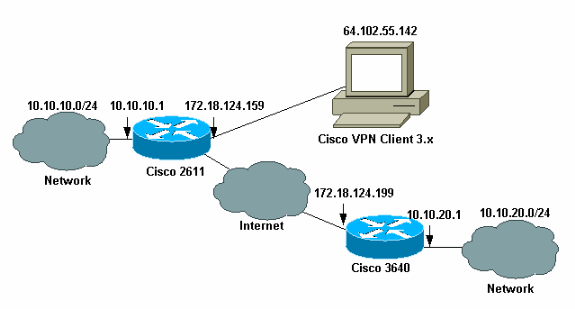
Configuring Ipsec Between Two Routers And A Cisco Vpn Client 4 X Cisco

Site To Site Ipsec Vpn Between Two Cisco Asa One With Dynamic Ip
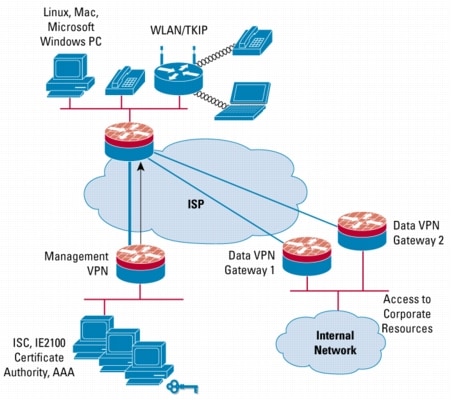
Cisco Ios Ipsec High Availability Ipsec Negotiation Ike Protocols Cisco Systems

Configuration Of Bgp In A Gre Over Ipsec Tunnel With A Cisco Router To Announce Nat Networks
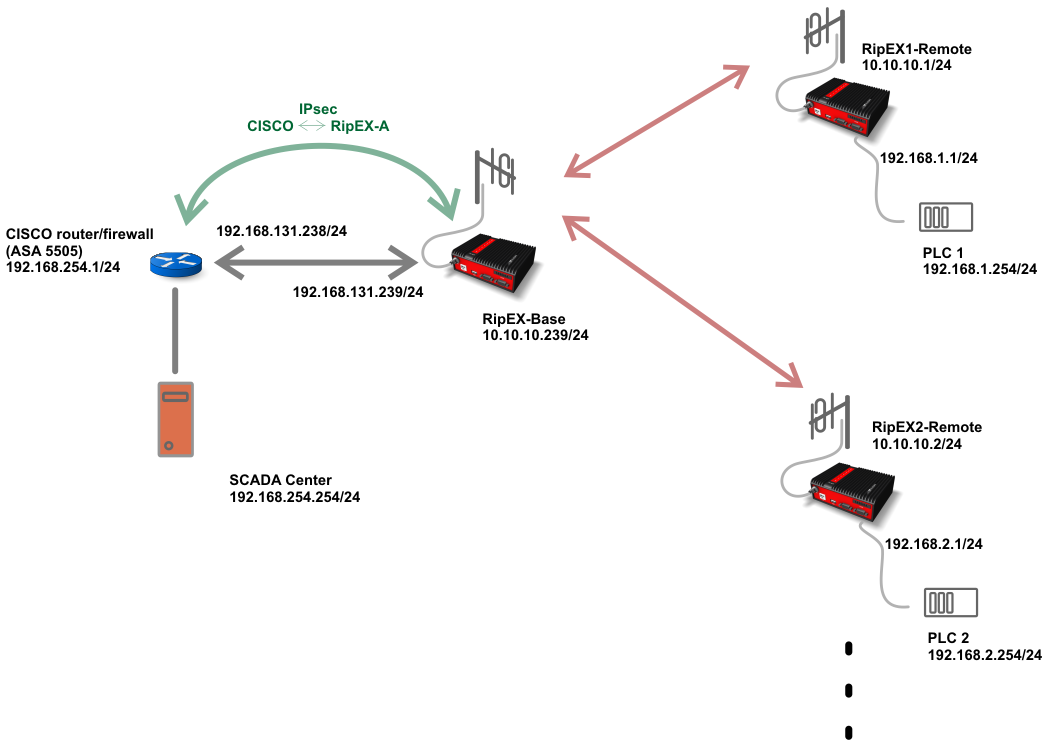
Ripex Ipsec 8 Configuration Example With Cisco Router Racom

Cisco Ipsec Tunnel Mode Configuration
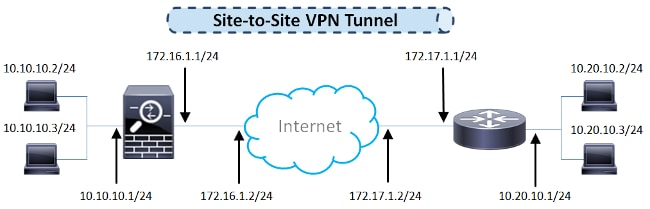
Configure A Site To Site Ipsec Ikev1 Tunnel Between An Asa And A Cisco Ios Router Cisco
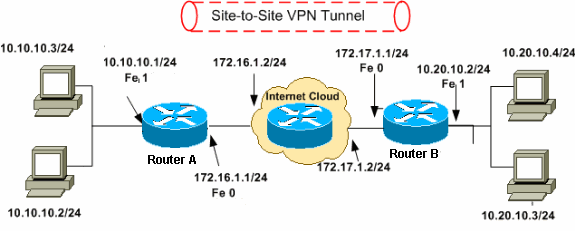
Configuration Professional Site To Site Ipsec Vpn Between Two Ios Routers Configuration Example Cisco

Administration Guide Fortigate Fortios 6 4 4 Fortinet Documentation Library
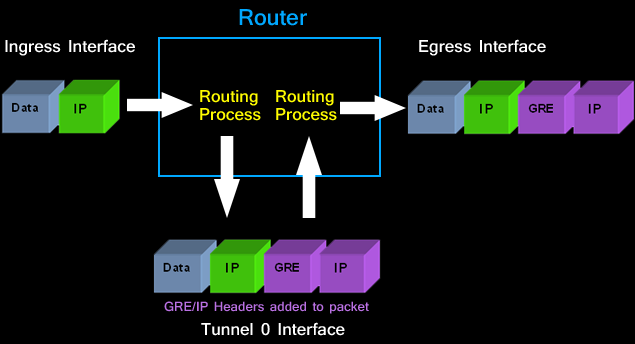
Configuring Point To Point Gre Vpn Tunnels Unprotected Gre Protected Gre Over Ipsec Tunnels
Q Tbn And9gctaxbkdp 97eqcfbvs7hiemhqp80fvgiyy314h8ay7njex8aivf Usqp Cau

Ipsec Over Gre Tunnel On Ios How To Configure Two Cisco Routers To Create Site To Site Vpn Tunnel Uninets Blog

Site To Site Ikev2 Ipsec Vpn Between Sophos Xg And Cisco Router Route Xp Private Network Services

Mo S Ccie Blog Cisco Asa Site To Site Ikev2 Ipsec Vpn
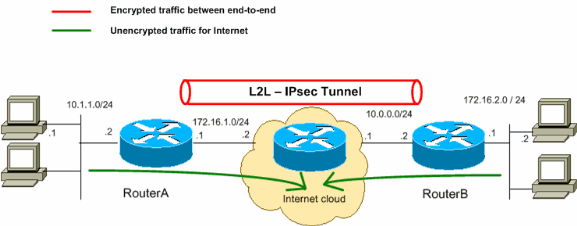
Lan To Lan Ipsec Tunnel Between Two Routers Configuration Example Cisco
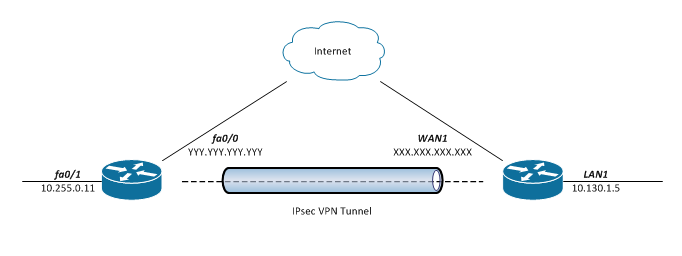
How To L2l Ipsec Vpn Between Cisco Isr 2811 And Draytek Vigor 2850n Sk Scratchpad

Site2site Ipsec Vpn Tunnel With Cisco Easyvpn Network Guy
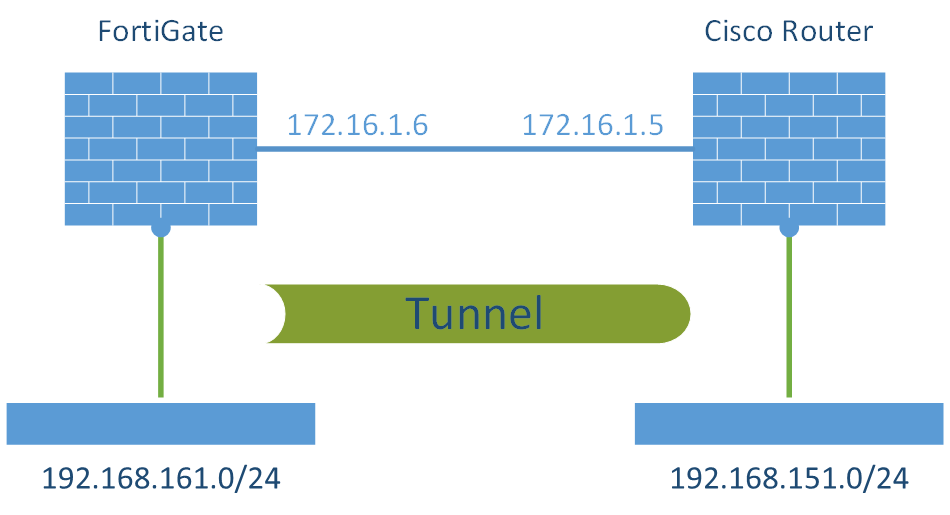
Ipsec Site To Site Vpn Fortigate Cisco Router Weberblog Net
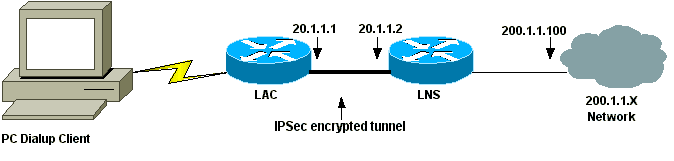
Configuring Layer 2 Tunneling Protocol L2tp Over Ipsec Cisco
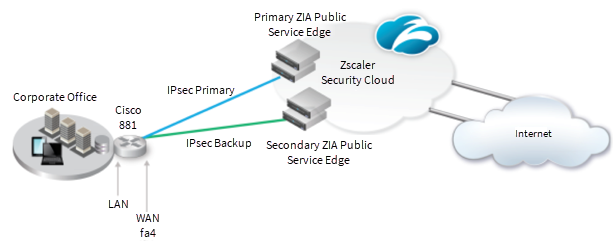
Ipsec Vpn Configuration Guide For Cisco 1 Isr Zscaler
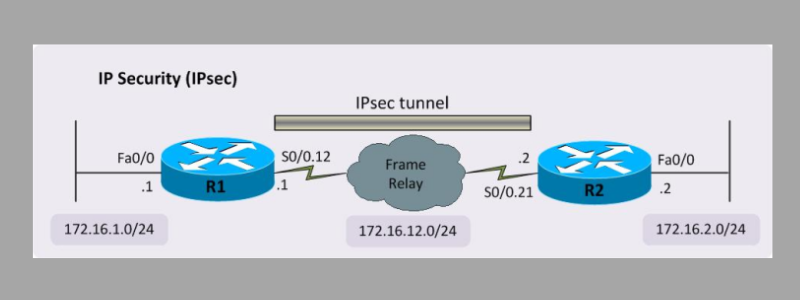
Ipsec Tunnel Vs Transport Mode Comparison And Configuration

Gre Over Ipsec In Cisco Ios Sina Shahriar S Blog
Full Crypto Cisco Ipsec Vpn Gateway With Software Client

Cisco Ipsec Vpn
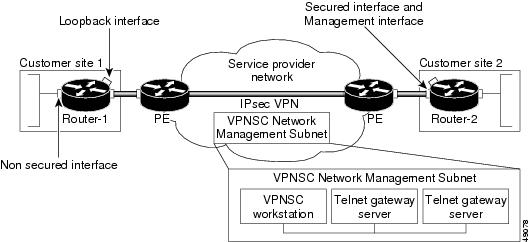
Introduction To Cisco Ipsec Technology Cisco

Cisco Ipsec Vpn Ccie Or Null
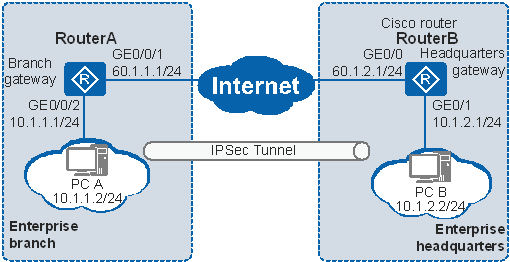
Establishing An Ipsec Tunnel Between The Ar And The Cisco Router In The Ikev1 Aggressive Mode
Ikev2 Ipsec Virtual Private Networks Understanding And Deploying Ikev2 Ipsec Vpns And Flexvpn In Cisco Ios Cisco Press
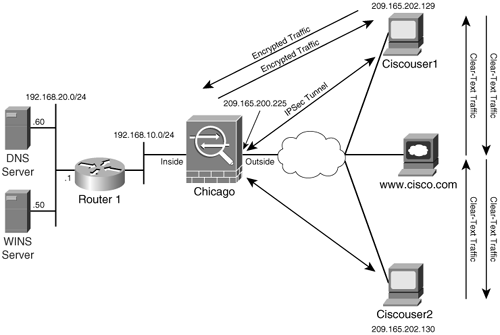
Cisco Remote Access Ipsec Vpn Setup Vpn Management Using Asdm
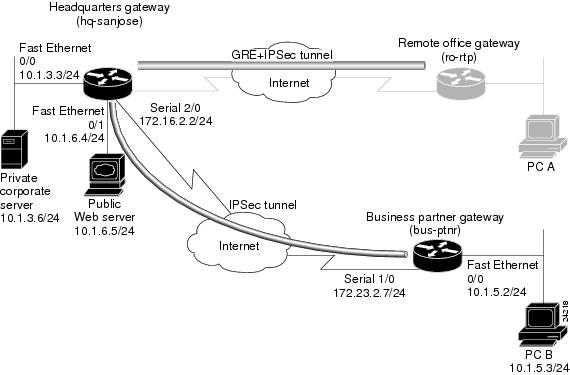
Cisco Ios Vpn Configuration Guide Site To Site And Extranet Vpn Business Scenarios Cisco 70 Series Routers Cisco

Pfsense Configuration Recipes Connecting To Cisco Ios Devices With Ipsec Pfsense Documentation
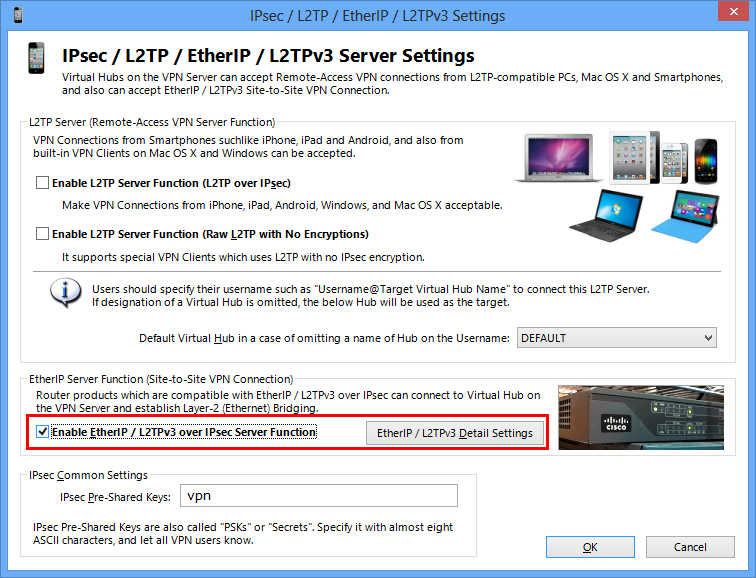
Cisco L2tpv3 Ipsec Edge Vpn Router Setup Softether Vpn Project

How To Configure Ipsec Vpn With Dynamic Ip In Cisco Ios Router Tech Support Says

Handbook Fortigate Fortios 6 0 0 Fortinet Documentation Library
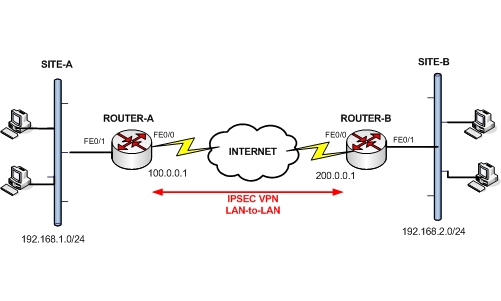
Lan To Lan Ipsec Vpn Between Cisco Routers Configuration Example
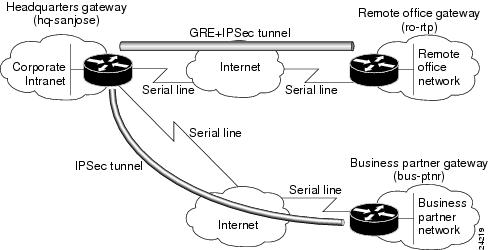
Cisco Ios Vpn Configuration Guide Site To Site And Extranet Vpn Business Scenarios Cisco 70 Series Routers Cisco

Gns3 Ipsec Tunnel Between Asav And Oci A Team Chronicles
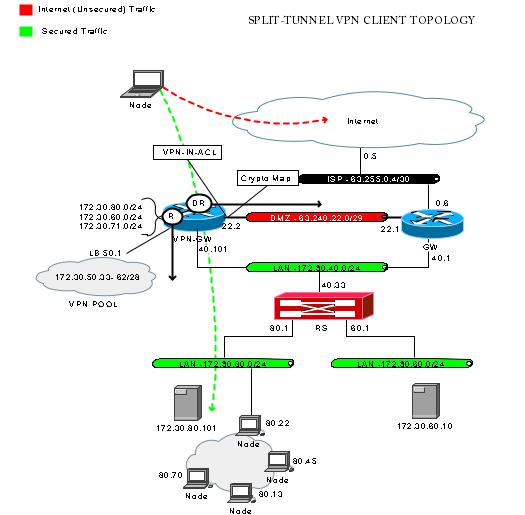
Split Tunnel Cisco Ipsec Vpn Gateway With Software Client

Configuring Ipsec Vpn On Cisco Ios Techrepublic
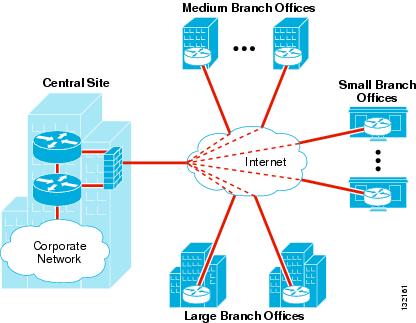
Ipsec Direct Encapsulation Vpn Design Guide Cisco

Ipsec Vti On Cisco Isr Reporting Up Up And Decapsulating Packets But Not Encapsulating Network Engineering Stack Exchange
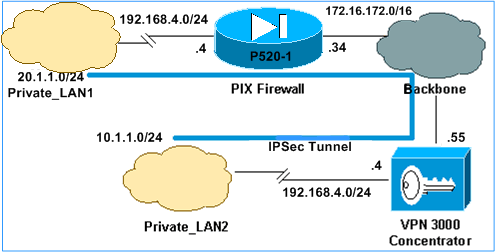
Ipsec Between Pix Firewall And Cisco Vpn 3000 Concentrator With Overlapping Private Networks Configuration Example Cisco

Configure Site To Site Vpn With Ipsec In Cisco Networking And Wireless Training Courses
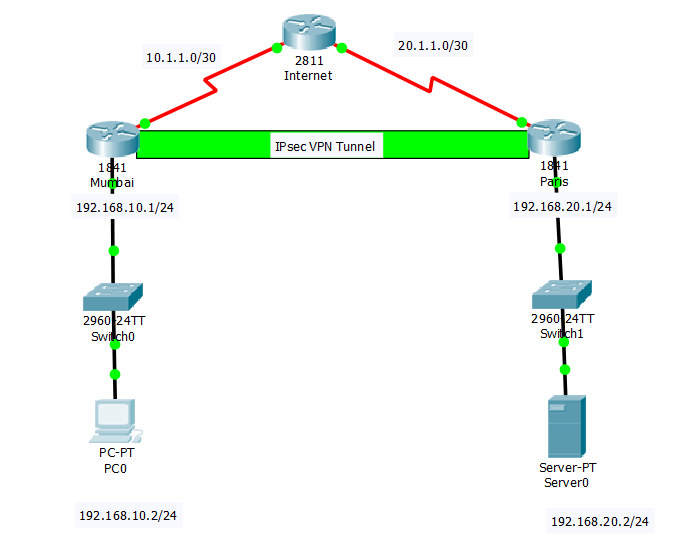
How To Configure Site To Site Ipsec Vpn Using Cisco Packet Tracer

Implementation Of Ipsec Vpn On Cisco Routers And Configuring It On Is
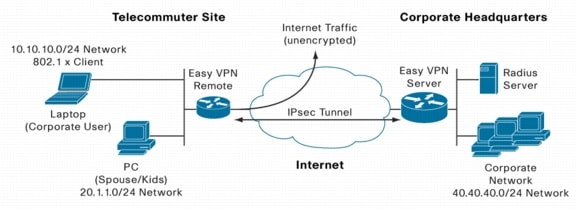
Configuring Cisco Ios Easy Vpn Remote With 802 1x Authentication Ipsec Negotiation Ike Protocols Cisco Systems

Configure Site To Site Ipsec Vpn Cisco Routers Tech Space Kh
Q Tbn And9gcrpgu9 Griep1rzlsbhcq9hiujig4ls0knvdpsg0yf 9g5xtsxh Usqp Cau
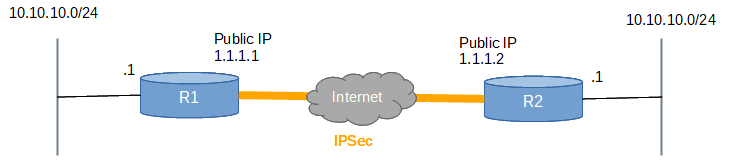
Cisco Ipsec Vpn Configuration Examples Cmdref Net Cheat Sheet And Example
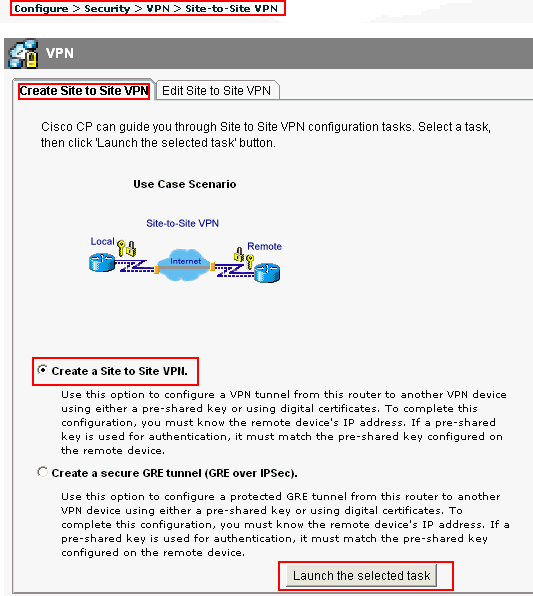
Configuration Professional Site To Site Ipsec Vpn Between Two Ios Routers Configuration Example Cisco
Q Tbn And9gctylqclezpwxnmpqtu8uuz6z 5c39du0b6fj9mwsysnu5wu1 C Usqp Cau
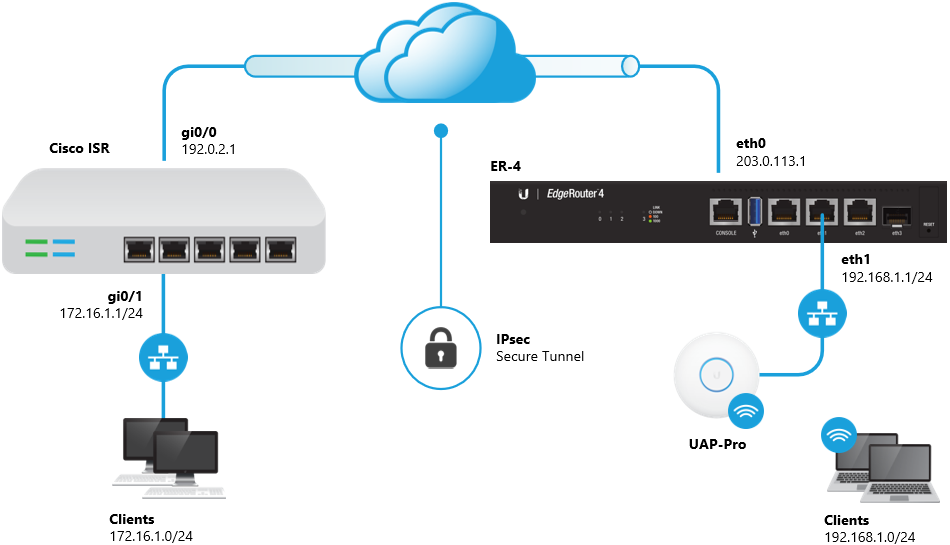
Edgerouter Site To Site Ipsec Vpn To Cisco Isr Ubiquiti Support And Help Center
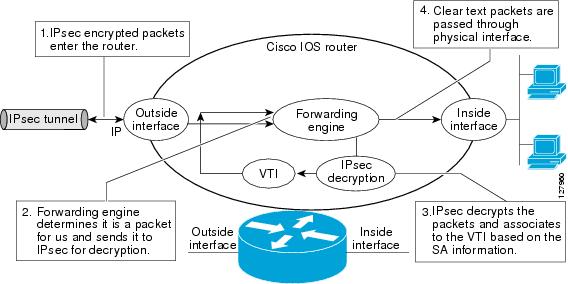
Ipsec Virtual Tunnel Interface Cisco Systems
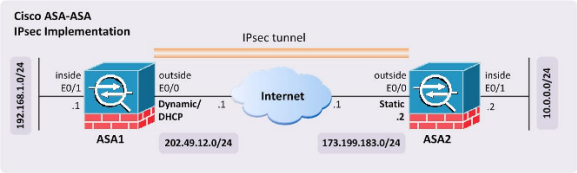
Site To Site Ipsec Vpn Between Two Cisco Asa 55 Router Switch Blog

Site To Site Vpn Tunnel On Cisco Router Gns3 Mr Robot

Cisco Asa Site To Site Ikev1 Ipsec Vpn

Ipsec Tunnel Between Cisco Routers Site To Site Vpn Between Cisco Routers

Tricks How To Debug A Specific Ipsec Vpn Tunnel On Cisco Marktugbo Com
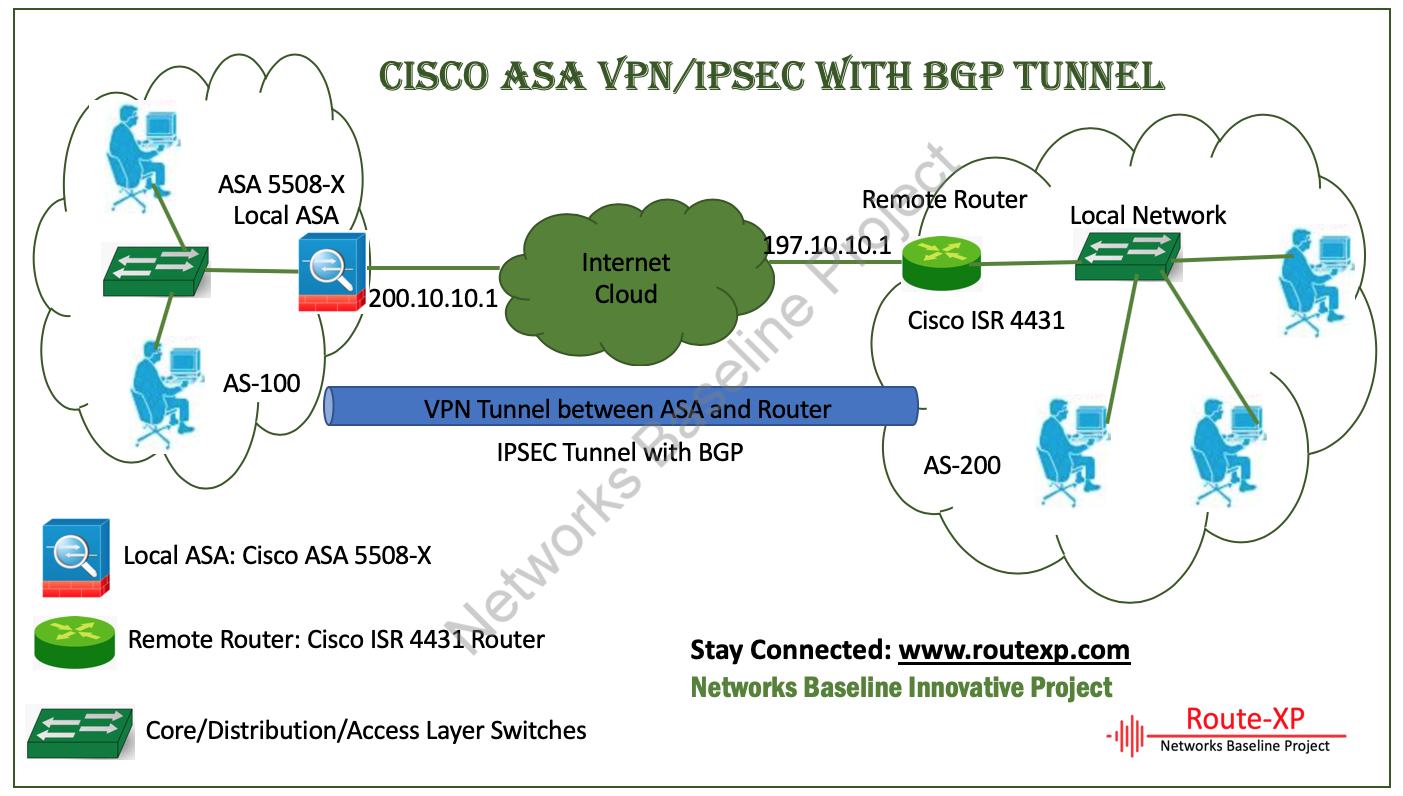
Cisco Asa 5508 X Vpn Ipsec With Bgp Tunnel Route Xp Private Network Services
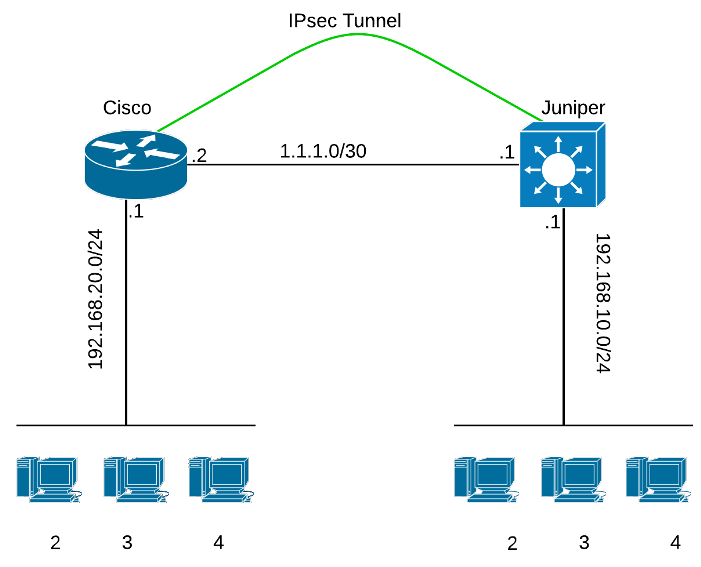
Site To Site Ipsec Vpn Between Cisco Router And Juniper Security Gateway

How To Configure Ipsec Vpn Between Cisco Asa And Palo Alto Firewall

Five Steps Of Ipsec ran Cisco Certified Expert
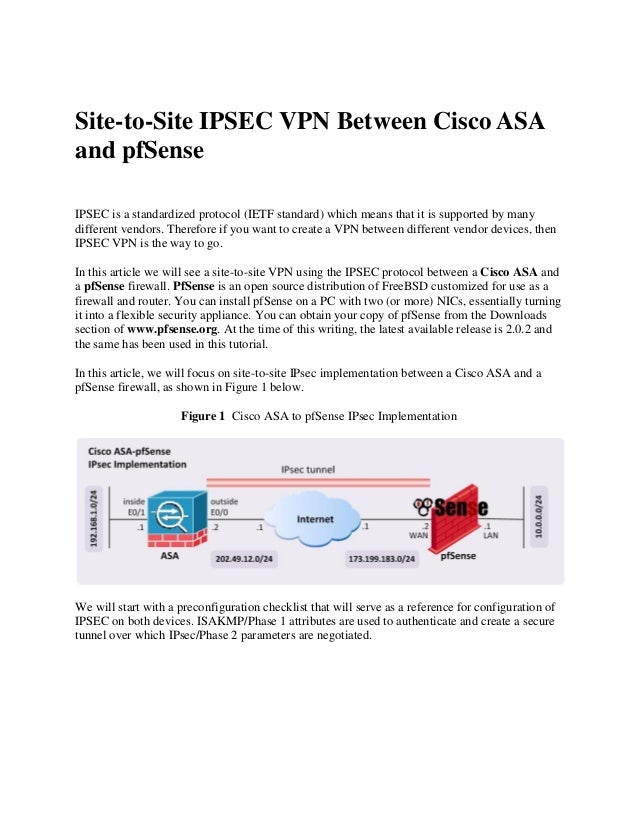
Site To Site Ipsec Vpn Between Cisco Asa And Pfsense



